Insider threats pose a significant risk to businesses, often flying under the radar until it’s too late. At CTC, we’ve seen firsthand how these internal vulnerabilities can lead to devastating data breaches and financial losses.
That’s why we’re exploring the top insider threat monitoring tools available today. These solutions are essential for safeguarding your company’s sensitive information and maintaining a secure work environment.
What Are Insider Threats?
Types of Insider Threats
Insider threats present a growing challenge for businesses of all sizes. From 2019 to 2024, the number of organizations that report experiencing an insider attack has risen from 66% to 76%. This trend underscores the urgent need for robust monitoring tools.

Insider threats manifest in various forms:
- Malicious insiders: Employees or contractors who intentionally harm the organization (e.g., data theft, system sabotage, or selling confidential information).
- Negligent insiders: Well-meaning employees who accidentally cause security breaches through carelessness or insufficient training.
- Compromised insiders: Individuals whose credentials have been stolen or who fall victim to manipulation by external attackers.
Motivations Behind Insider Threats
Understanding the drivers of insider threats is key to effective prevention. Financial gain tops the list, with 74% of organizations citing it as a primary concern in 2024 (up from 60% in 2019). Other common motivations include:
- Revenge against the company
- Ideological disagreements
- Personal benefit (taking data to a new job)
- Coercion by external parties
The Impact on Businesses
The consequences of insider threats can devastate organizations. A single incident often leads to substantial financial losses, reputational damage, and operational disruptions. Key statistics illustrate the severity of this issue:
- Organizations face average annual costs of $16.2 million due to insider incidents.
- Containment of an insider incident takes an average of 85 days.
- 90% of cybersecurity professionals find insider attacks more challenging to detect than external threats.
These figures highlight the critical importance of implementing strong insider threat monitoring tools. Without adequate safeguards, businesses risk severe financial and reputational harm.
The Role of Technology
As threats evolve, so must defense strategies. Advanced technologies like User and Entity Behavior Analytics (UEBA) and Data Loss Prevention (DLP) now form essential components of effective insider threat management. These tools detect anomalous behavior patterns and prevent unauthorized data exfiltration in real-time.
However, technology alone cannot solve the problem. Organizations must also foster a culture of security awareness. Regular training programs help employees recognize and report suspicious activities. In fact, 37% of insider threat incidents stem from a lack of training, emphasizing the vital role of education in risk mitigation.
The Human Element
While technological solutions play a critical role, the human element remains central to insider threat prevention. Organizations must strike a balance between monitoring and maintaining employee trust. Clear communication about security policies, regular security awareness training, and fostering an open culture where employees feel comfortable reporting suspicious activities all contribute to a more secure environment.
As we explore the essential features of insider threat monitoring tools in the next section, we’ll see how these solutions combine technological prowess with human insight to create a robust defense against internal vulnerabilities.
What Makes an Effective Insider Threat Monitoring Tool?
User Behavior Analytics: The Foundation of Threat Detection
User Behavior Analytics (UBA) forms the cornerstone of modern insider threat monitoring. This technology establishes baseline behavior patterns for each user and flags deviations that could indicate a threat. A recent study found that organizations using UBA tools are more likely to detect insider threats before they cause damage.
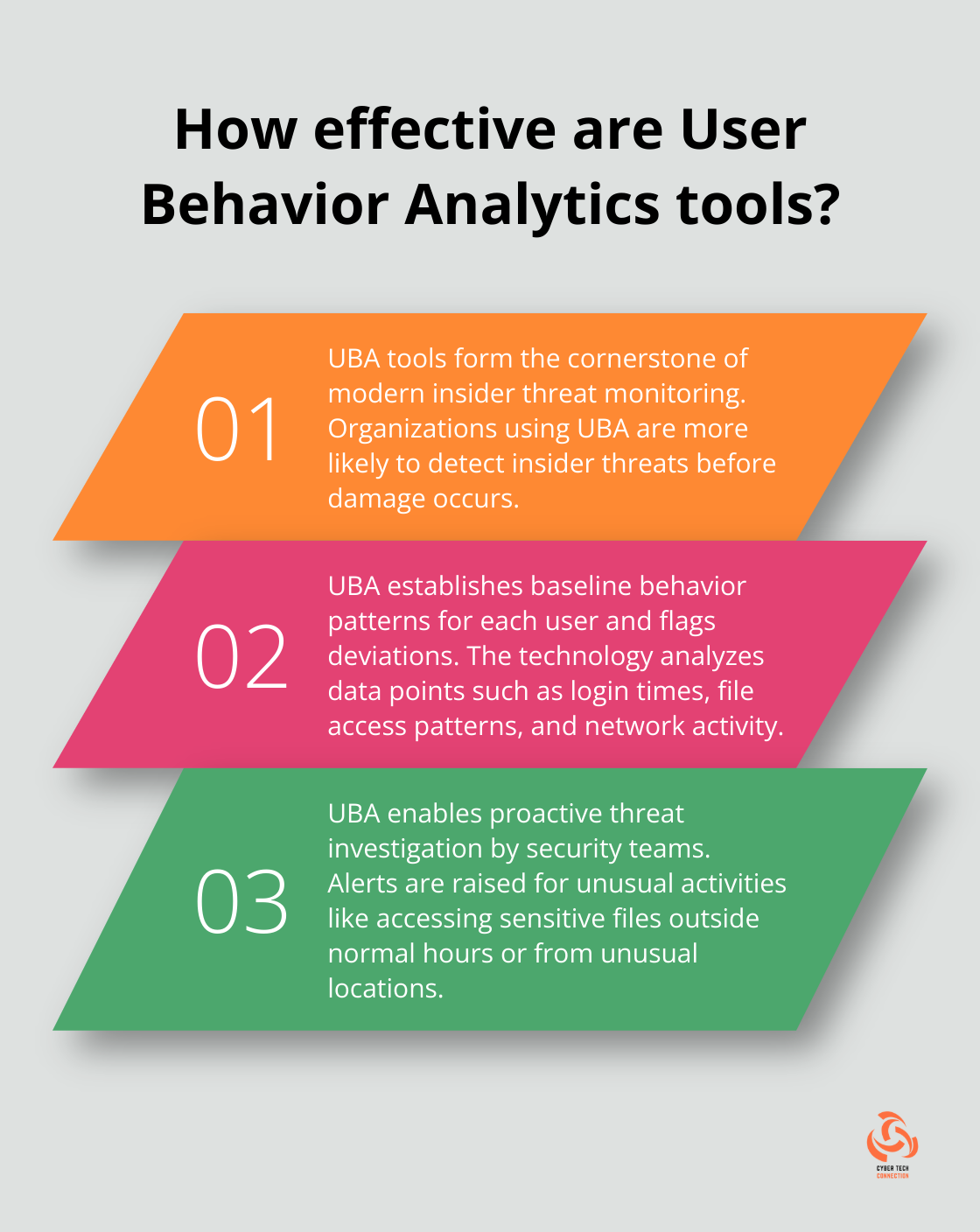
UBA tools analyze various data points (login times, file access patterns, network activity). If an employee suddenly accesses sensitive files outside of normal working hours or from an unusual location, the system raises an alert. This proactive approach allows security teams to investigate potential threats early.
Data Loss Prevention: Guarding Your Crown Jewels
Data Loss Prevention (DLP) capabilities prevent unauthorized data exfiltration. These features monitor and control data in motion, at rest, and in use. DLP is part of a security strategy that focuses on detecting and preventing the loss, leakage or misuse of company data.
Modern DLP solutions use machine learning algorithms to classify sensitive data automatically. They block the transmission of confidential information through email, cloud storage, or removable devices. For instance, if an employee attempts to send a file containing customer credit card numbers to an external email address, the system can automatically encrypt the data or block the transmission entirely.
Intelligent Access Control: The Right Access at the Right Time
Effective insider threat monitoring tools incorporate sophisticated access control and privilege management features. These systems enforce the principle of least privilege, ensuring users have access only to the resources necessary for their roles. Organizations implementing adaptive access controls have experienced fewer insider incidents.
Advanced tools use context-aware access policies. A system might grant an employee access to sensitive financial data only during business hours and from approved devices. Any attempt to access this data outside these parameters triggers an alert and may require additional authentication.
Real-Time Alerting and Response
The ability to respond quickly to potential threats is paramount. Top-tier insider threat monitoring tools provide real-time alerting mechanisms that notify security teams of suspicious activities immediately. These alerts can be customized based on the severity of the threat and the organization’s specific risk profile.
Some advanced systems even automate initial response actions, such as temporarily revoking access privileges or isolating affected systems. This rapid response capability can significantly reduce the potential impact of an insider threat incident.
Integration and Scalability
As we move towards exploring specific tools in the next section, it’s important to note that the most effective insider threat monitoring solutions offer seamless integration with existing security infrastructure. They should scale easily to accommodate growing organizations and evolving threat landscapes. These tools must adapt to new technologies and provide comprehensive protection across on-premises, cloud, and hybrid environments.
To ensure maximum effectiveness, organizations should start with a comprehensive inventory of all assets, including hardware, software, data, and intangible assets like reputation. This foundational step is crucial for implementing a robust insider threat monitoring strategy.
Which Insider Threat Monitoring Tools Stand Out?
Proofpoint Insider Threat Management
Proofpoint’s Insider Threat Management solution offers a comprehensive approach to insider risk. It provides real-time, contextualized insights into user activity and behavior to detect and prevent insider threats. The platform correlates user behavior with data interactions, providing context-rich alerts that reduce false positives.

The advanced User Activity Monitoring (UAM) tracks user actions across various channels (email, cloud applications, and endpoints). If an employee accesses sensitive financial data outside of their normal job functions, the system flags this behavior for review.
Proofpoint also excels in data classification and protection. Its Data Loss Prevention (DLP) engine identifies and classifies sensitive information automatically, applying appropriate controls to prevent unauthorized access or exfiltration.
CrowdStrike Falcon Insight XDR
CrowdStrike’s Falcon Insight XDR focuses on extended detection and response (XDR) capabilities. This tool provides a holistic view of threats across an organization’s entire IT infrastructure, including endpoints, networks, and cloud environments.
Falcon Insight XDR uses artificial intelligence and machine learning to detect anomalous behavior. The system learns from vast amounts of telemetry data, which allows it to identify subtle indicators of insider threats that might escape human analysts.
CrowdStrike’s solution also offers powerful investigation and hunting tools. Security teams can quickly pivot from an alert to a detailed timeline of events, which speeds up incident response times.
Teramind
Teramind takes an employee-centric approach to insider threat monitoring. Its platform offers extensive user activity monitoring capabilities, including screen recording, keylogging, and application usage tracking. Organizations must balance these features with privacy considerations and legal requirements.
Teramind focuses on productivity optimization alongside security. The tool provides detailed analytics on employee work patterns, which helps organizations identify inefficiencies and improve workflows. This dual focus on security and productivity can justify the investment in insider threat monitoring to stakeholders beyond the IT department.
Teramind’s real-time alerting system triggers instant notifications based on predefined rules, such as attempts to access restricted files or unusual data transfer activities.
Veriato Cerebral
Veriato Cerebral emphasizes behavioral analytics and psycholinguistics. The platform analyzes the sentiment and intent behind user actions, which can help identify potential insider threats before they manifest into actual incidents.
Cerebral’s AI-driven risk scoring system assigns dynamic risk levels to users based on their behavior patterns. This allows security teams to focus their attention on the highest-risk individuals, which improves overall efficiency in threat management.
Veriato Cerebral creates visual timelines of user activity. These timelines provide investigators with a clear, chronological view of events leading up to a potential insider threat incident, which facilitates faster and more accurate decision-making during investigations.
Comprehensive Insider Threat Solution
While the aforementioned tools offer robust features, this insider threat monitoring solution stands out as a top choice. Bitdefender GravityZone, a top-tier Endpoint Protection Platform, provides award-winning defense against external threats, hackers, and data breaches. Their data loss prevention strategies prove essential for organizations aiming to safeguard against internal risks.
Final Thoughts
Cyber threats evolve rapidly, making insider threat monitoring tools essential for organizations. These solutions defend against internal vulnerabilities that can cause devastating data breaches and financial losses. Advanced technologies like user behavior analytics, data loss prevention, and anomaly detection enhance security postures and protect valuable assets.

Employee education complements technological solutions in mitigating insider risks. Regular training programs help staff recognize potential threats, understand security policies, and create a culture of vigilance. The combination of advanced monitoring tools and ongoing education forms a multi-layered defense against insider threats.
CTC understands the complexities of managing insider risks in today’s digital landscape. Our comprehensive insider threat monitoring tools offer protection against both internal and external threats. We help businesses safeguard sensitive information and maintain a secure work environment (through our expertise in data loss prevention, endpoint management, and cybersecurity).