Operational threat intelligence has become a critical component of effective cybersecurity strategies. At CTC, we’ve seen firsthand how this proactive approach can significantly enhance an organization’s ability to detect, prevent, and respond to cyber threats.
Operational threat intelligence provides real-time, actionable insights that enable security teams to make informed decisions and take immediate action against potential threats. This blog post will explore the key aspects of operational threat intelligence and how it can be implemented to strengthen your organization’s security posture.
What is Operational Threat Intelligence?
Real-Time Insights for Immediate Action
Operational threat intelligence transforms cybersecurity strategies. It provides actionable information that helps organizations identify and respond to immediate threats. Unlike strategic and tactical intelligence, operational intelligence focuses on the present moment.
The Power of Up-to-the-Minute Data
Operational threat intelligence offers a constant flow of information about current threats, attack patterns, and adversary tactics. This real-time data empowers security teams to make swift, informed decisions. For instance, when a new malware strain targets companies in your industry, operational intelligence supplies immediate details on its behavior, allowing you to update your defenses promptly.
Concrete Steps, Not Theoretical Scenarios
The actionable nature of operational intelligence sets it apart. It doesn’t deal with long-term trends or hypothetical situations. Instead, it provides specific, immediate steps to protect your organization.
Seamless Integration for Maximum Effect
Operational threat intelligence must integrate smoothly into existing security infrastructure to be effective. This integration means feeding intelligence directly into SIEMs, firewalls, and other security tools.
The Irreplaceable Human Touch
While automation plays a vital role in operational threat intelligence, human expertise remains invaluable. Skilled analysts interpret data, understand its context, and make critical decisions.

Operational threat intelligence isn’t optional in today’s world, it’s a necessity. As cyber threats evolve rapidly, the ability to quickly identify and respond to threats can determine whether an organization faces a minor incident or a major breach. The next section will explore the key features that make operational threat intelligence truly effective in protecting your digital assets.
What Makes Operational Threat Intelligence Effective?
Speed and Accuracy in Data Processing
Operational threat intelligence thrives on rapid and precise data processing. With the help of machine learning (ML) algorithms and historical security data, OTI can identify the signatures of known threats. Once trained, these algorithms can analyze vast amounts of data in real-time, enabling security teams to act quickly.
Contextual Analysis for Meaningful Insights
Raw data alone doesn’t suffice. Effective operational threat intelligence provides context, transforming information into actionable insights. For instance, when a system detects an unusual spike in failed login attempts, it doesn’t merely flag the activity. It analyzes the source, compares it to known threat actors, and recommends immediate actions.

This contextual analysis proves invaluable. A Ponemon Institute study revealed that organizations using security intelligence technologies reduced data breach costs by an average of $1.55 million.
Seamless Integration with Existing Security Infrastructure
Operational threat intelligence must work in harmony with an organization’s existing security tools to maximize effectiveness. This integration allows for automated responses to certain threats, reducing the workload on security teams and minimizing response times.
When integrated with a SIEM system, threat intelligence can automatically correlate incoming threat data with internal log data, providing a more comprehensive view of potential risks. Some organizations report a reduction in mean time to detect (MTTD) threats by up to 70% through such integrations.
Tailored Intelligence for Specific Threats
Every organization faces unique threats based on its industry, size, and digital footprint. Effective operational threat intelligence addresses these specific risks. A financial institution might focus on detecting and preventing fraud attempts, while a healthcare provider might prioritize protecting patient data from ransomware attacks.
This tailored approach ensures efficient resource allocation, focusing on the most relevant threats to the organization. A SANS Institute survey found that 71% of organizations using threat intelligence reported improved prevention, detection, and response capabilities.
Continuous Adaptation to Evolving Threats
Cybersecurity changes rapidly, and effective operational threat intelligence must keep pace. This requires constant updates to threat databases, refinement of detection algorithms, and adaptation of response strategies.
AI improves threat detection by using machine learning to analyze data in real time, identifying patterns and anomalies to catch new threats early. This proactive approach proves essential in maintaining a robust security posture in an ever-changing digital environment.
As we explore the implementation of operational threat intelligence in the next section, we’ll examine how organizations can leverage these key features to enhance their cybersecurity strategies and protect their digital assets effectively.
How to Implement Operational Threat Intelligence
Assess Your Current Security Posture
Start with a thorough assessment of your existing security infrastructure. Identify gaps in your defenses and areas where threat intelligence can provide the most value. This assessment should include an inventory of your digital assets, current security tools, and processes.
Operational intelligence provides context that helps security teams understand how attackers plan and sustain campaigns.
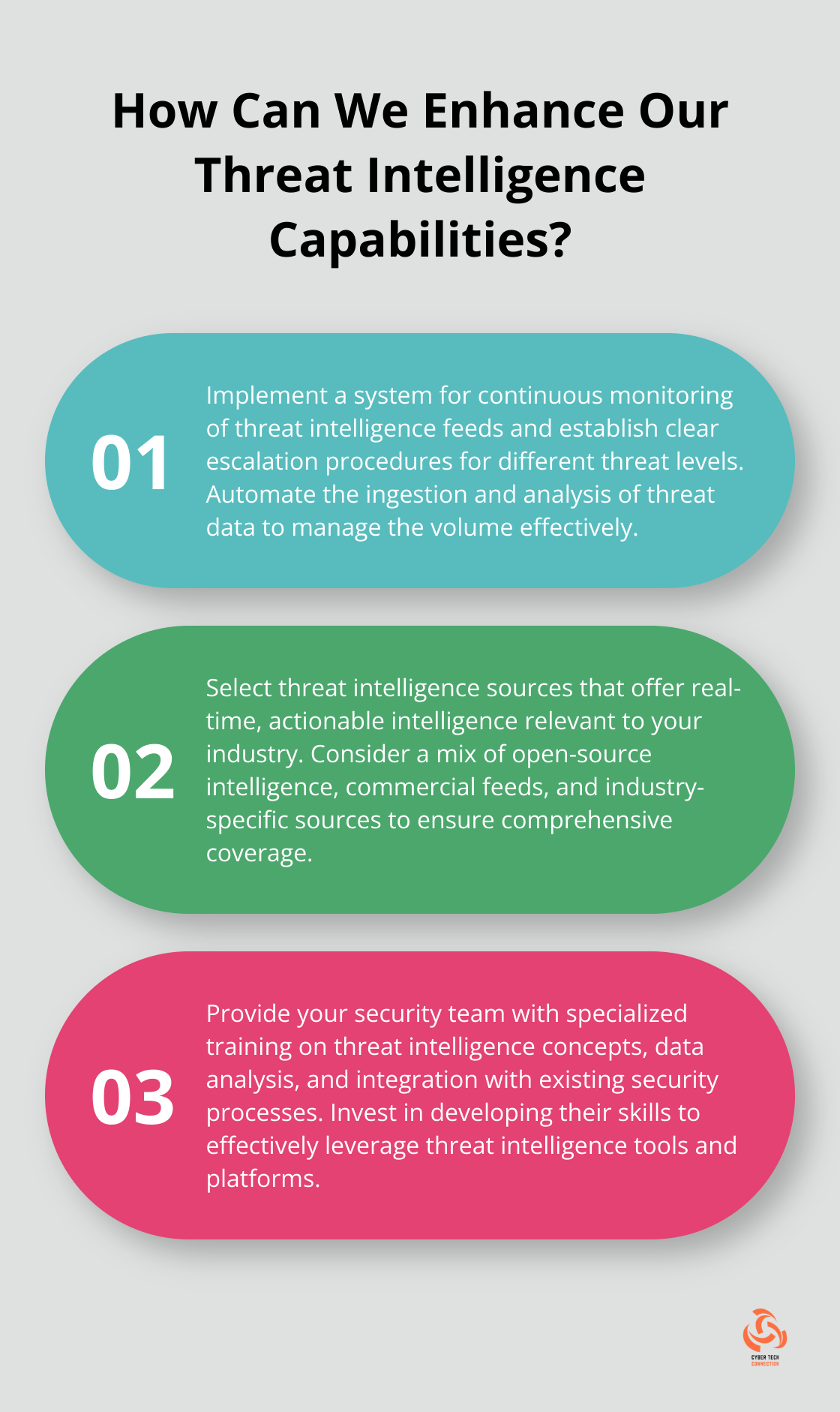
Select Appropriate Threat Intelligence Sources
Choose threat intelligence sources that offer real-time, actionable intelligence relevant to your industry and threat landscape. Consider a mix of open-source intelligence (OSINT), commercial feeds, and industry-specific sources.

The quality of your intelligence sources directly impacts the effectiveness of your OTI program. A strong 71% of organizations have a dedicated threat intelligence team, and 87% of them consider their threat intelligence activities to be at an “intermediate” level or higher.
Equip Your Security Team
Provide your security team with the skills needed to leverage threat intelligence effectively. This training should cover:
- Understanding threat intelligence concepts and terminology
- Analyzing and interpreting threat data
- Integrating intelligence into existing security processes
- Using threat intelligence platforms and tools
Investing in your team’s skills pays off. Organizations with skilled security teams can reduce the cost of a data breach by an average of $238,000 (according to a recent industry report).
Set Up Continuous Monitoring and Response Processes
Establish processes for continuous monitoring of threat intelligence feeds and rapid response to identified threats. This involves:
- Automating the ingestion and analysis of threat data
- Establishing clear escalation procedures for different threat levels
- Regularly updating security controls based on new intelligence
- Conducting regular threat hunting exercises
Automation is key to managing the volume of threat data effectively. Industry experts predict that by 2025, 50% of enterprises will use MDR (Managed Detection and Response) services that leverage AI for faster threat detection and response.
Evaluate and Enhance Effectiveness
Regularly assess the impact of your OTI program on your overall security posture. Key metrics to track include:
- Reduction in mean time to detect (MTTD) and respond (MTTR) to threats
- Number of prevented incidents based on threat intelligence
- Improvement in threat detection accuracy (reduced false positives)
- Return on investment (ROI) of your threat intelligence program
A study found that organizations using security intelligence technologies reduced data breach costs by an average of $1.55 million.
Try to refine your approach based on the evolving threat landscape and your organization’s changing needs. The goal is to turn data into actionable insights that enhance your security posture.
Final Thoughts
Operational threat intelligence has become an essential tool in modern cybersecurity. It provides real-time, actionable insights that enable organizations to detect, prevent, and respond to threats with unprecedented speed and accuracy. The benefits of implementing operational threat intelligence include reduced response times, improved threat detection accuracy, and a more robust overall security posture.
The role of operational threat intelligence will continue to grow in importance as cyber threats evolve and digital environments become more complex. We expect to see further advancements in machine learning and artificial intelligence, which will enhance the ability of threat intelligence platforms to identify and analyze emerging threats. The integration of threat intelligence with existing security infrastructure will become more seamless, allowing for automated responses to a wider range of threats.
Cyber Tech Connection understands the critical role that operational threat intelligence plays in protecting digital assets. Our comprehensive range of cybersecurity services (including endpoint management, penetration testing, and data loss prevention) helps organizations leverage the power of threat intelligence to enhance their security posture. In an era of constantly evolving cyber threats, proactive cybersecurity measures are essential for staying one step ahead of cybercriminals.