Cybersecurity threat intelligence is a powerful tool in the fight against digital threats.
This guide will walk you through the basics of threat intelligence, its key components, and how to implement it effectively in your organization.
Whether you’re new to cybersecurity or looking to enhance your existing defenses, understanding threat intelligence is a critical step towards robust protection in today’s digital landscape.
What is Cybersecurity Threat Intelligence?
The Foundation of Modern Digital Defense
Cybersecurity threat intelligence forms the cornerstone of cutting-edge digital defense strategies. It involves the collection, analysis, and application of information about potential or current attacks that threaten an organization’s assets. This process transforms raw data into actionable insights that prevent breaches and minimize damage.
Shifting to Proactive Defense
Threat intelligence revolutionizes the cybersecurity paradigm, moving from reactive to proactive approaches. Organizations can now anticipate and prepare for attacks, rather than merely responding to them.
Three Flavors of Intelligence
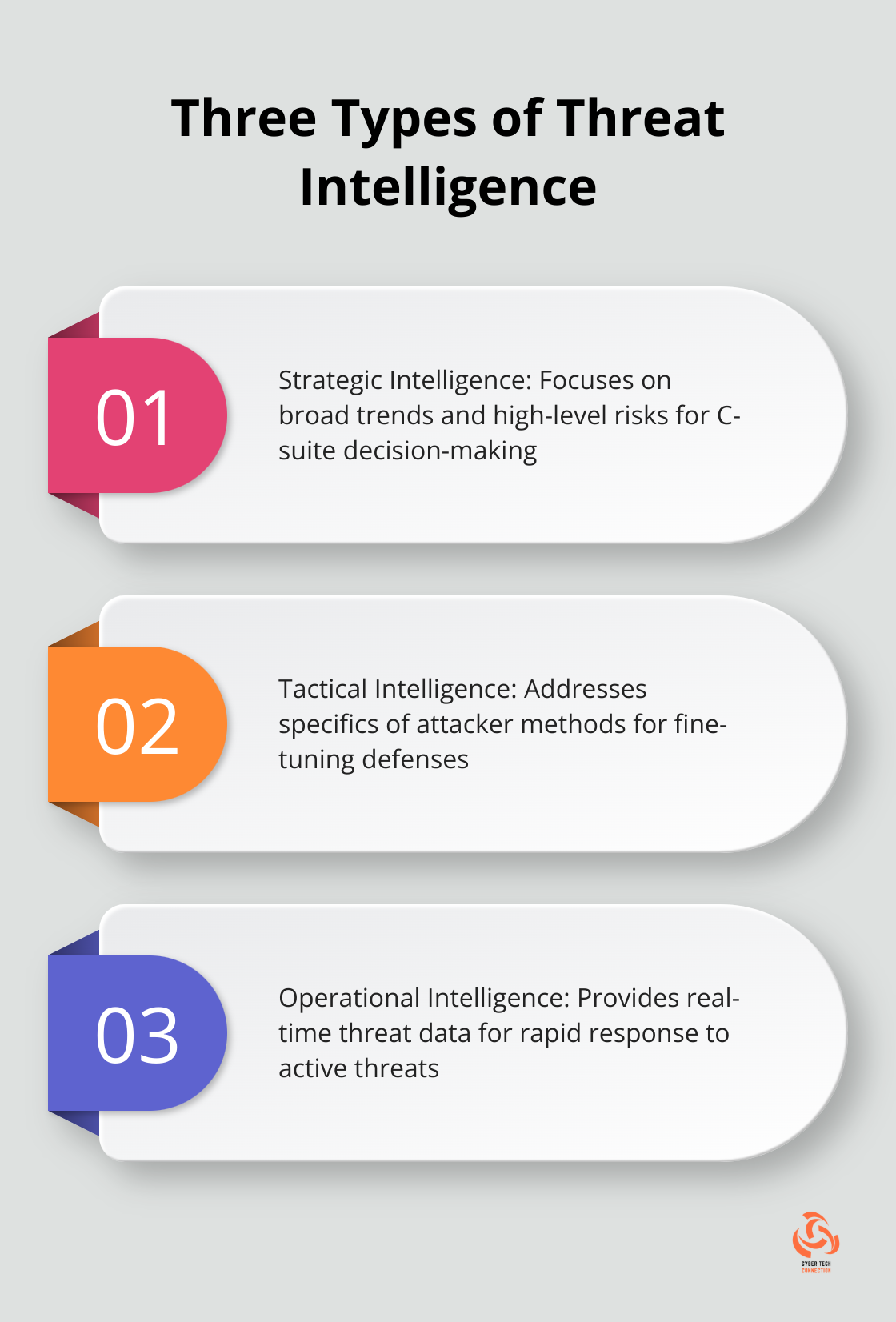
Threat intelligence manifests in three distinct forms, each serving a unique purpose:
- Strategic Intelligence: This focuses on broad trends and high-level risks. C-suite executives use it to make informed decisions about cybersecurity investments and policies.
- Tactical Intelligence: It addresses the specifics of attacker methods. Security analysts rely on this to fine-tune defenses against particular threats.
- Operational Intelligence: This provides real-time threat data, enabling rapid response to active threats (a critical factor in minimizing damage during an attack).
Boosting Your Cybersecurity Posture
The implementation of threat intelligence can significantly improve your overall security stance in several ways:
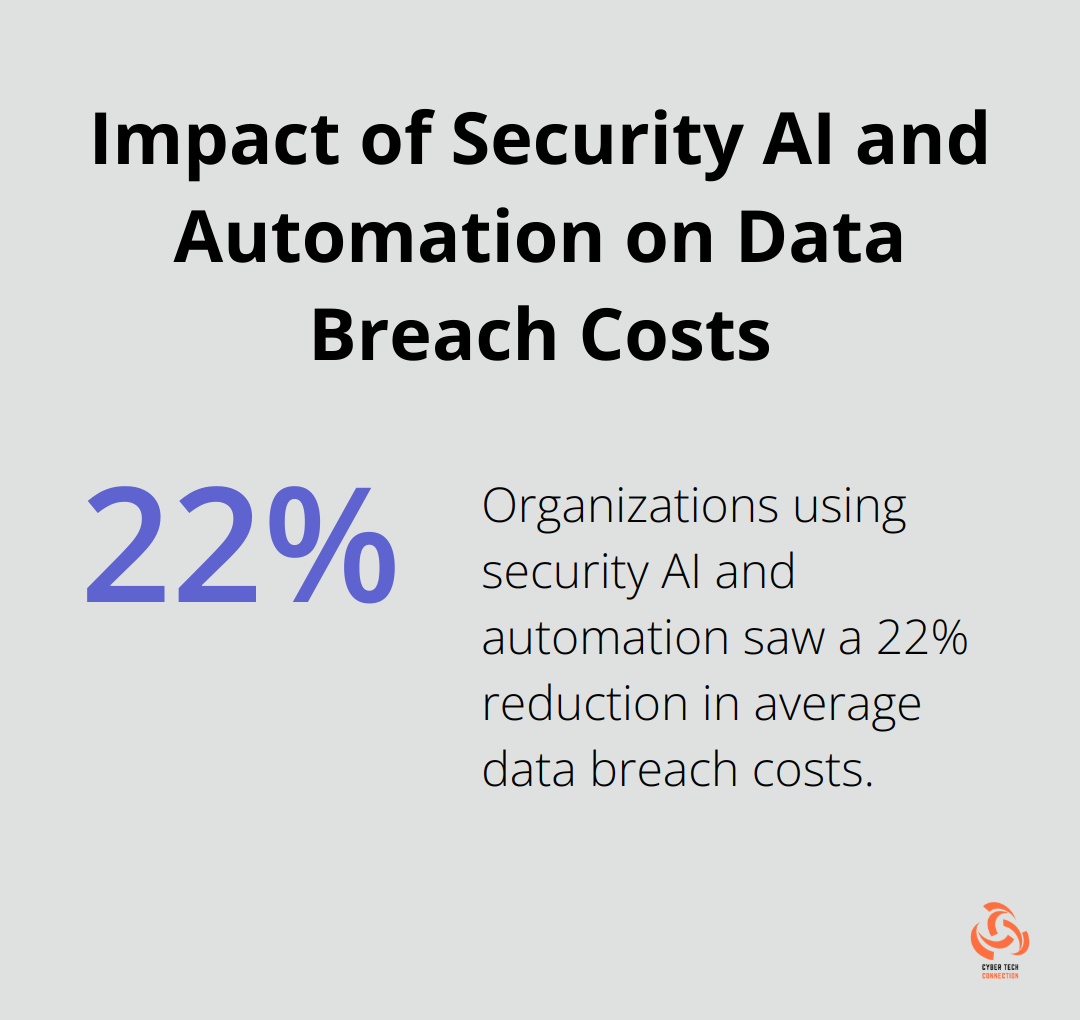
- Accelerated Threat Detection: Organizations using security AI and automation have seen a direct impact on the average cost of a data breach.
- Enhanced Incident Response: Teams can prioritize threats and respond more effectively with threat intelligence. The SANS Institute reports that 71% of organizations experienced improved incident response times after implementing threat intelligence.
- Optimized Resource Allocation: Understanding which threats are most likely to target your organization allows you to focus your resources where they’re needed most.
Getting Started with Threat Intelligence
To begin your journey with threat intelligence, consider using open-source tools like MISP (Malware Information Sharing Platform) or AlienVault OTX. For more comprehensive solutions, platforms like CrowdStrike Falcon X or CTC’s Threat Intelligence services offer advanced features and expert analysis.
It’s important to note that threat intelligence isn’t a one-size-fits-all solution. You need to tailor it to your organization’s specific needs and integrate it with your existing security infrastructure for maximum effectiveness.
As we move forward, let’s explore the key components that make up a robust threat intelligence system and how they work together to fortify your digital defenses.
Building Your Threat Intelligence Arsenal
Data Collection: Casting a Wide Net
The first step in threat intelligence involves gathering data from diverse sources. This includes public feeds, dark web monitoring, and industry-specific intelligence sharing platforms. A study by Ponemon Institute surveyed 1,548 IT and IT security practitioners in the United States (649), the United Kingdom (451) and EMEA (448) in 2025, highlighting the importance of comprehensive data collection in threat intelligence.
Analysis: Transforming Raw Data into Actionable Insights
After data collection, the next crucial step is analysis and processing. This process correlates information, identifies patterns, and assesses the relevance of threats to your specific organization. Advanced analytics tools (powered by machine learning algorithms) can process vast amounts of data quickly. For example, IBM’s Watson for Cyber Security analyzes up to 1 million security documents per second, which significantly speeds up threat analysis.
Dissemination: Spreading the Word Effectively
Actionable intelligence only provides value if it reaches the right people at the right time. Effective dissemination creates clear, concise reports tailored to different stakeholders within your organization. To address challenges in making threat intelligence actionable, we recommend the use of standardized formats like STIX (Structured Threat Information eXpression) for sharing threat intelligence. This approach ensures consistency and ease of interpretation across different teams and tools.
Integration: Maximizing Impact Through Seamless Connectivity
The final component involves integrating threat intelligence with existing security systems. This integration could mean feeding data into your SIEM (Security Information and Event Management) system, firewalls, or intrusion detection systems. Gartner reports that organizations that integrate threat intelligence into their security operations see a 22% improvement in threat detection capabilities.

These four pillars form the foundation of a robust threat intelligence system. The next section will explore how to implement these components effectively in your organization, ensuring you maximize the benefits of your threat intelligence efforts.
How to Implement Threat Intelligence
Assess Your Current Security Posture
Before you implement threat intelligence, conduct a thorough assessment of your existing security infrastructure. This evaluation should cover your current tools, processes, and team capabilities. A 2025 survey by Ponemon Institute revealed that 67% of organizations with successful threat intelligence programs started with a comprehensive security assessment.
Identify your most critical assets and the threats they face during this phase. This prioritization will help you focus your threat intelligence efforts where they matter most. For example, if you operate in the financial sector, you might prioritize intelligence related to financial malware and fraud tactics.
Select the Right Tools and Platforms
Choosing appropriate threat intelligence tools is essential for success. Look for platforms that offer a wide range of data sources, advanced analytics capabilities, and seamless integration with your existing security stack.
While many options exist, Cyber Tech Connection’s Threat Intelligence platform stands out for its comprehensive coverage and ease of use. It aggregates data from multiple sources (including dark web forums and industry-specific threat feeds), providing a holistic view of the threat landscape.
For organizations just starting out, open-source tools like MISP (Malware Information Sharing Platform) can serve as a good entry point. However, as your needs grow, consider more robust commercial solutions that offer advanced features like automated threat scoring and customizable alerts.
Train Your Team
Effective threat intelligence isn’t just about tools-it’s about people. Invest in training your security team to interpret and act on threat intelligence data. This includes understanding different types of indicators, recognizing patterns, and making informed decisions based on the intelligence received.
A study by SANS Institute found that organizations that invested in regular threat intelligence training for their security teams saw a 35% improvement in incident response times. Try to send team members to specialized courses or bring in experts for on-site training sessions.
Measure and Refine
Implementing threat intelligence requires continuous measurement and refinement. Establish clear metrics to gauge the effectiveness of your program. These might include:
- Reduction in mean time to detect (MTTD) and mean time to respond (MTTR) to threats
- Number of prevented attacks based on threat intelligence
- ROI in terms of avoided breach costs
Gartner highlighted the impact of cyber threat intelligence (CTI) and its future potential at the Gartner Security & Risk Management Summit in Mumbai.
Regularly reassess your threat intelligence needs and adjust your strategy accordingly. As your organization grows and the threat landscape evolves, your approach to threat intelligence should adapt as well.
Final Thoughts
Cybersecurity threat intelligence has become an essential component of modern digital defense strategies. It empowers organizations to anticipate and prepare for potential attacks, transforming raw data into actionable insights that prevent breaches and minimize damage. The future of threat intelligence looks promising, with advancements in artificial intelligence and machine learning set to revolutionize how we collect, analyze, and act on threat data.
To implement threat intelligence effectively, organizations must assess their current security posture, select appropriate tools, and invest in team training. Continuous measurement and refinement of the threat intelligence program will ensure its ongoing effectiveness in the face of evolving digital threats. The implementation of a robust threat intelligence system can significantly enhance an organization’s overall cybersecurity posture.
For comprehensive cybersecurity threat intelligence solutions, consider partnering with Cyber Tech Connection. CTC offers a range of cybersecurity services, including mobile phone defense, endpoint management, and penetration testing, to help organizations stay ahead of potential threats and secure their digital assets.

