This introduction to cybersecurity for business will equip you with essential knowledge and practical steps to protect your organization. We’ll cover the basics, key measures, and best practices for safeguarding your business in today’s digital landscape.
What Are the Cybersecurity Basics?
Understanding Cybersecurity
Cybersecurity protects systems, networks, and programs from digital attacks. This practice has become indispensable for businesses in today’s digital landscape.
The Evolving Threat
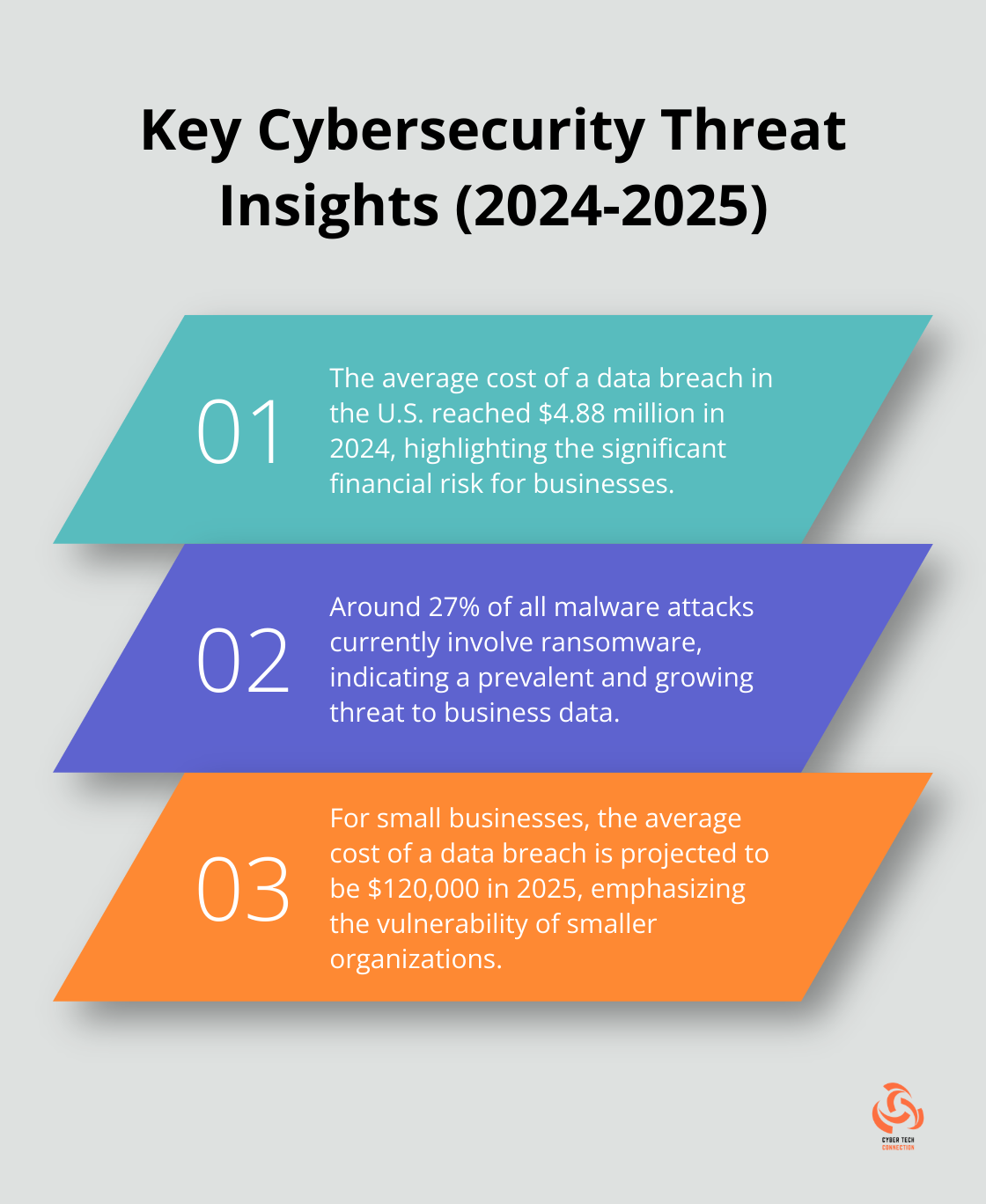
Cyber threats manifest in various forms. Around 27% of all malware attacks right now involve ransomware. Data breaches expose customer information and tarnish reputations. IBM reported that the average cost of a data breach in the U.S. reached $4.88 million in 2024, underscoring the financial implications of cybersecurity for businesses.
Business Impact of Cybersecurity
Cybersecurity transcends attack prevention; it maintains business continuity. A cyberattack can halt operations, resulting in lost revenue and customer trust. Small businesses face particular vulnerability, with the average cost of a small business data breach in 2025 being $120,000.
Practical Cybersecurity Measures
- Risk Assessment: Identify your most valuable assets and potential vulnerabilities.
- Multi-Factor Authentication: Implement this across all accounts. Microsoft reports this simple step prevents 99.9% of account compromise attacks.
- Employee Training: Regular training is essential. IBM found human error contributes to 95% of cybersecurity breaches. Foster a culture where employees report suspicious activities without hesitation.
- Robust Endpoint Protection: Secure individual devices, especially with the prevalence of remote work. Use reputable antivirus software and maintain regular updates.
The Ongoing Nature of Cybersecurity
Cybersecurity requires continuous attention and adaptation. Stay informed about emerging threats and adjust your strategies accordingly. The next section will explore essential cybersecurity measures for businesses in more detail, providing you with actionable steps to enhance your organization’s digital defense.
How to Implement Essential Cybersecurity Measures
Strong Password Policies: Your First Line of Defense
Weak passwords open doors for hackers. Implement a policy that requires employees to use complex passwords with a minimum of 12 characters, including uppercase and lowercase letters, numbers, and symbols. Use a password manager (like LastPass or 1Password) to generate and store strong, unique passwords for each account.
A 2024 report shows a substantial increase in vulnerability exploitation, especially web application attacks, as a critical path to breaches. Don’t become part of this statistic. Enforce password changes every 90 days and implement multi-factor authentication (MFA) across all accounts.
Keep Your Systems Up-to-Date
Outdated software attracts cybercriminals. Set up automatic updates for all your systems and applications. For critical business software that doesn’t allow automatic updates, create and follow a strict manual update schedule.
Don’t overlook your employees’ devices. Use mobile device management (MDM) solutions to ensure all company-owned or BYOD devices stay up-to-date and comply with your security policies.
Employee Training: Your Human Firewall
Your employees are both your greatest asset and your biggest vulnerability. Regular, engaging cybersecurity training is essential. Interactive, scenario-based training often yields the best results.
Conduct phishing simulations to test and educate your staff. Include topics like social engineering, safe browsing habits, and proper data handling in your training programs.

Robust Network Security
Firewalls and antivirus software act as your network’s immune system. Choose next-generation firewalls (NGFW) that offer features like intrusion prevention, SSL inspection, and application awareness. For antivirus, select endpoint detection and response (EDR) solutions that use AI and machine learning to detect and respond to threats in real-time.
Pay attention to your Wi-Fi security. Use WPA3 encryption, hide your SSID, and change your Wi-Fi password regularly. If you offer guest Wi-Fi, ensure it’s separate from your main network.
Data Encryption and Backup: Your Safety Net
Encrypt all sensitive data, both at rest and in transit. Use full-disk encryption for all devices and SSL/TLS for all web traffic. For cloud storage, select providers that offer end-to-end encryption.
Implement a robust backup strategy following the 3-2-1 rule: keep at least three copies of your data, on two different storage types, with one copy off-site. Test your backups regularly to ensure they can be restored when needed.
Cybersecurity requires constant vigilance and adaptation. As we move into an era where remote work becomes increasingly common, businesses must adapt their cybersecurity strategies accordingly. Let’s explore how to secure your business in a remote work environment.
How to Secure Remote Work Environments
Remote work has become a permanent fixture in the business landscape, bringing new cybersecurity challenges. Today’s global demand for cybersecurity professionals exceeds supply, which can increase workforce-related challenges. This surge underscores the critical need for robust remote work security measures.
Fortify Home Networks
The first step in securing remote work environments is to strengthen home networks. Employees should change default router passwords, enable WPA3 encryption, and update firmware regularly. A study by the National Cyber Security Centre found that 23% of remote workers use unsecured Wi-Fi networks, exposing sensitive company data to potential breaches.
Implement Network Access Control (NAC) solutions to ensure only authorized devices connect to your company’s resources. This approach can significantly reduce unauthorized access attempts.
Use VPNs and Zero Trust
Virtual Private Networks (VPNs) are essential for encrypting data in transit. However, traditional VPNs aren’t enough. Adopt a Zero Trust Network Access (ZTNA) model, which verifies every access request regardless of its source. According to insights from a Gartner report, approximately 60 percent of organizations will adopt Zero Trust as a foundational element by 2024.
For maximum security, combine ZTNA with multi-factor authentication (MFA). This combination has proven to prevent 99.9% of automated attacks (as reported by Microsoft).

Secure Mobile and Cloud Environments
With the proliferation of mobile devices and cloud services in remote work, securing these environments is paramount. Implement Mobile Device Management (MDM) solutions to enforce security policies, remotely wipe lost devices, and separate personal and work data.
For cloud security, use Cloud Access Security Brokers (CASBs) to monitor and control cloud usage. A recent study found that organizations using CASBs experienced 35% fewer security incidents.
Regularly audit cloud configurations to prevent misconfigurations (which Gartner predicts will be responsible for 99% of cloud security failures through 2025).
Craft Incident Response Plans for Distributed Teams
Remote work complicates incident response. Develop and regularly test incident response plans tailored for distributed teams. Include clear communication channels, roles, and responsibilities.
Conduct tabletop exercises simulating various cyber incidents. These exercises have shown to reduce the average time to contain a breach by 30% (according to the Ponemon Institute).
Implement automated threat monitoring and protection tools. These tools can reduce the mean time to detect (MTTD) threats and the mean time to respond (MTTR) significantly for remote work environments.
Final Thoughts
This introduction to cybersecurity for business highlights the necessity of protecting digital assets in today’s evolving threat landscape. We covered essential strategies, from strong password policies to securing remote work environments with VPNs and Zero Trust models. Employee training remains a cornerstone of effective cybersecurity, creating a human barrier against social engineering attacks.
Cybersecurity requires continuous attention and adaptation to stay ahead of potential risks. Regular risk assessments and staying informed about emerging threats will help maintain a robust security posture. As cyber criminals become more sophisticated, your defenses must evolve accordingly.
Businesses looking to enhance their cybersecurity measures can benefit from partnering with experienced professionals. At Cyber Tech Connection, we offer comprehensive cybersecurity solutions tailored to specific needs. Don’t wait for a breach to occur before taking action (invest in your cybersecurity today to protect your business, customers, and future).

