Network attacks hit businesses every 39 seconds, making early detection the difference between a minor incident and a catastrophic breach.
At Cyber Tech Connection, we see organizations struggle with network security intrusion detection daily. Most companies only discover breaches 287 days after they occur, according to IBM’s 2024 Cost of a Data Breach Report.
This guide shows you proven methods to spot intrusions before they cause serious damage.
What Network Intrusions Target Your Business
Malware Infiltrates Through Multiple Attack Vectors
Malware attacks cost businesses significant amounts per incident according to IBM’s 2025 report, with ransomware accounting for 41% of all cyberattacks. Attackers deploy trojans through phishing emails that bypass traditional email filters 23% of the time. Worms spread laterally across networks within 18 minutes of initial infection, while polymorphic viruses change their code every 30 seconds to evade signature-based detection.
Ransomware groups like LockBit and ALPHV target specific file types (databases, backups, and configuration files). Your security team should monitor network traffic for unusual encryption patterns, unexpected file modifications, and processes that communicate with known command-and-control servers. Deploy behavioral analysis tools that flag applications when they request admin privileges or access unusual file locations.
Unauthorized Access Exploits Weak Authentication Points
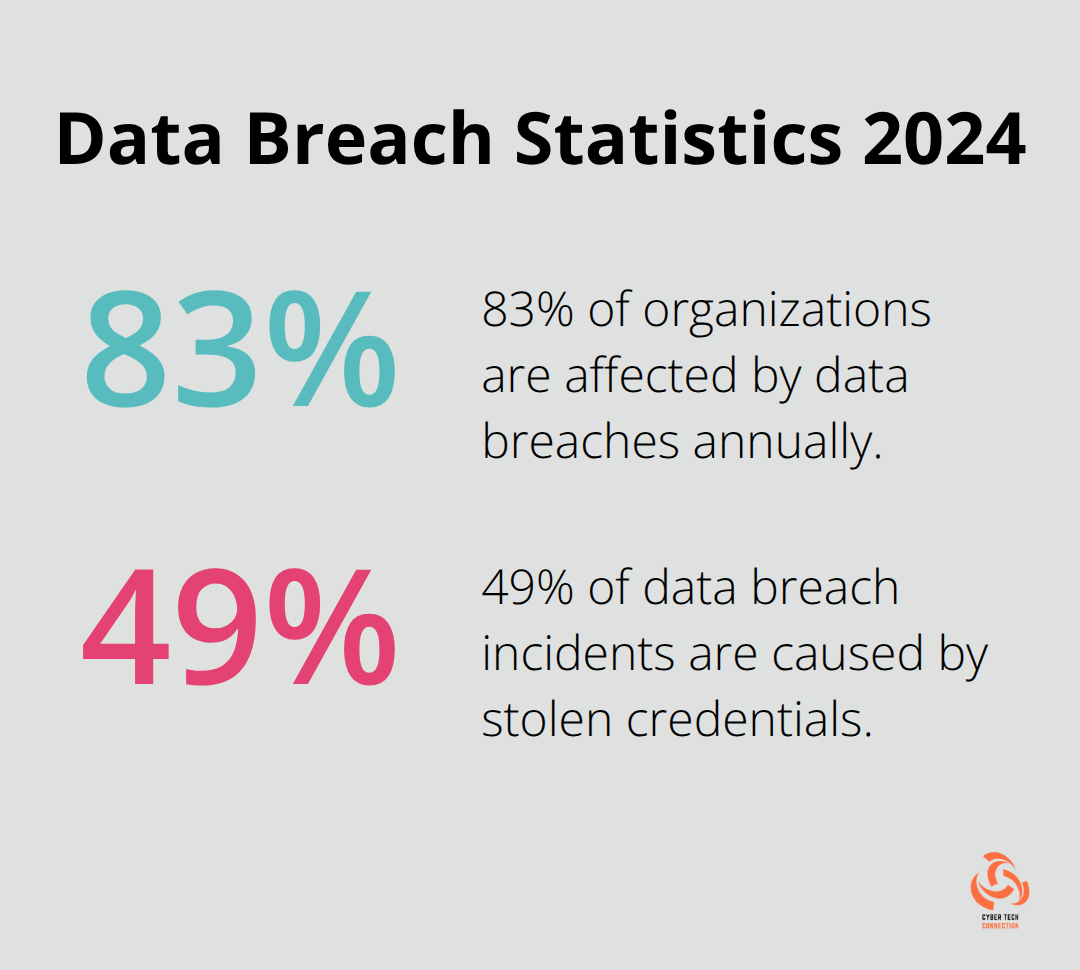
Data breaches through unauthorized access affect 83% of organizations annually, with stolen credentials responsible for 49% of incidents according to Verizon’s 2024 Data Breach Investigations Report. Attackers exploit weak passwords, unpatched vulnerabilities, and misconfigured access controls to gain initial foothold. Privilege escalation occurs within 4 hours of initial compromise in 67% of successful breaches.
Lateral movement techniques like pass-the-hash attacks spread across networks and use legitimate administrative tools. Track failed login attempts that exceed 5 per minute, monitor privileged account usage outside business hours, and watch for unusual database queries or file access patterns. Implement network segmentation to contain breaches and deploy endpoint detection tools that identify suspicious process behavior.
DDoS Attacks Overwhelm Infrastructure Resources
Distributed denial-of-service attacks increased 150% in 2024, with volumetric attacks that reach 3.8 Tbps according to Cloudflare’s DDoS report. Application-layer attacks target web servers with as few as 100 requests per second but consume server resources through complex database queries. Protocol attacks exploit TCP handshake weaknesses and consume connection state tables within 15 minutes. Amplification attacks use DNS and NTP servers to multiply attack traffic by 1000x.
Monitor bandwidth utilization spikes above 80% baseline, track connection attempt rates that exceed normal patterns, and identify traffic from unusual geographic locations (particularly regions with high cybercrime activity). Deploy rate limits at application level and implement traffic shaping to prioritize legitimate connections during attacks.
These attack patterns require sophisticated detection methods that go beyond basic perimeter security. The next section explores the specific tools and techniques that identify these threats before they compromise your network infrastructure.
Which Tools Actually Catch Network Intrusions
Intrusion Detection Systems Provide Real-Time Threat Intelligence
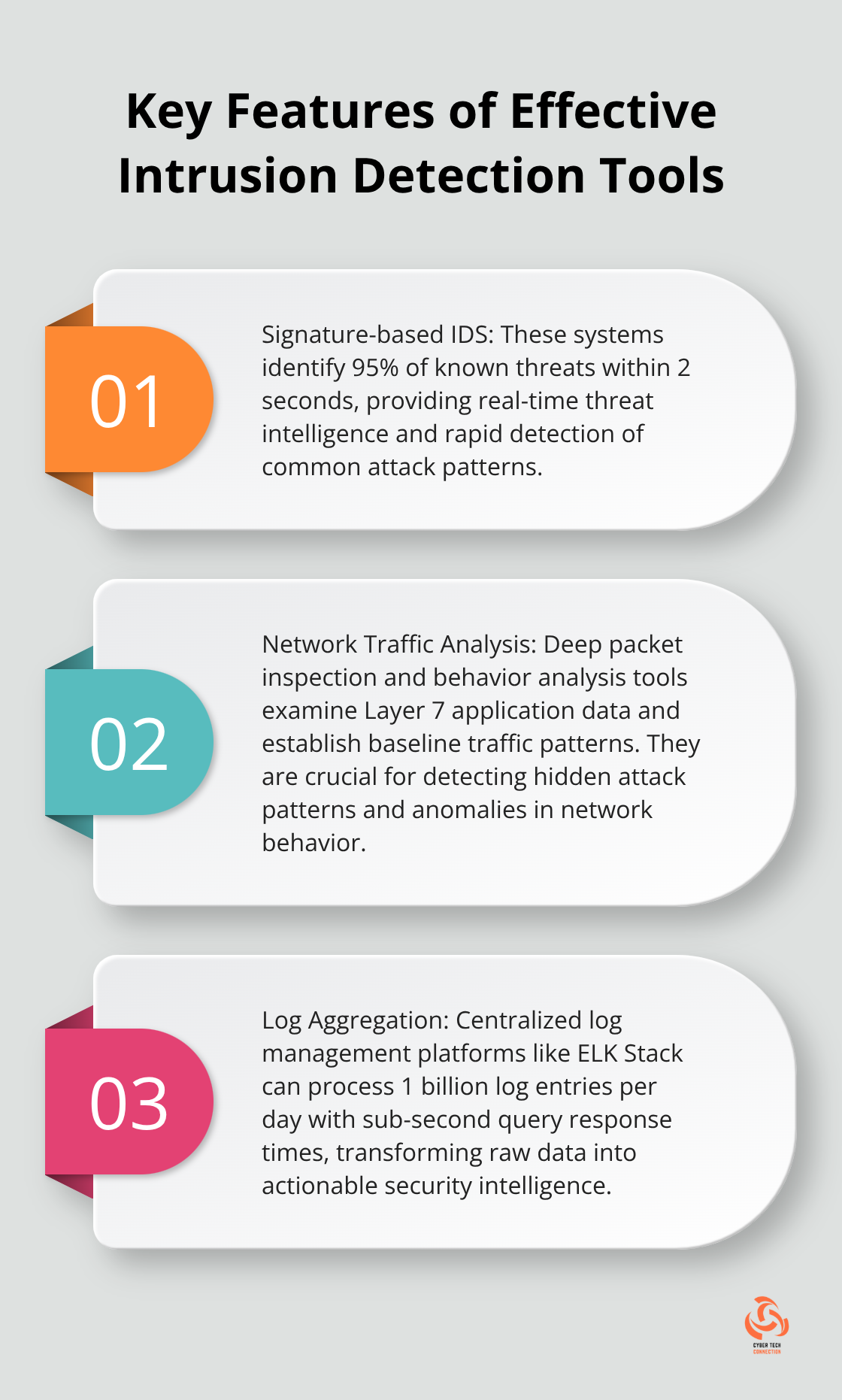
Modern intrusion detection systems like Suricata are designed for high-performance network monitoring and threat detection. Signature-based IDS identify 95% of known threats within 2 seconds, while anomaly-based systems catch zero-day attacks that traditional security tools miss. SIEM platforms aggregate data from network devices, servers, and applications to correlate events across your infrastructure. Splunk Enterprise processes 500 GB of log data daily and creates actionable alerts for security teams.
Deploy network-based IDS at strategic chokepoints like internet gateways, data center entrances, and between network segments. Configure custom rules for your environment rather than rely on default signatures. Set up automated responses that isolate compromised systems within 30 seconds of detection. Host-based IDS monitor individual servers for file integrity violations and unauthorized process execution.
Network Traffic Analysis Reveals Hidden Attack Patterns
Deep packet inspection tools examine Layer 7 application data to identify malicious payloads hidden in legitimate protocols. Network behavior analysis establishes baseline traffic patterns and flags deviations that indicate compromise. Wireshark captures full packet details for forensic analysis, while ntopng provides real-time flow monitoring with geographic threat mapping. Machine learning algorithms enhance detection capabilities compared to traditional rule-based systems.
Monitor east-west traffic between internal systems where 70% of advanced persistent threats operate undetected. Track DNS queries to known malicious domains, unusual data transfer volumes during off-hours, and encrypted tunnels used for data exfiltration. Implement network segmentation monitoring that alerts when devices communicate across security boundaries without authorization.
Log Aggregation Transforms Raw Data Into Security Intelligence
Centralized log management platforms collect events from firewalls, routers, switches, and security appliances into searchable databases. ELK Stack processes 1 billion log entries per day with sub-second query response times. Real-time correlation engines identify attack sequences that span multiple systems and timeframes. Security orchestration platforms automatically execute response playbooks based on threat severity scores.
Configure log retention for 90 days minimum to support incident investigations and compliance requirements. Set up automated parsing rules that extract key fields like source IP, destination port, and protocol type. Create custom dashboards that highlight critical security metrics and trend analysis for executive reports (essential for demonstrating ROI to leadership).
These detection tools work best when combined with proven security practices that strengthen your overall defense posture. The next section outlines specific implementation strategies that maximize your intrusion detection capabilities.
How Do You Build Bulletproof Intrusion Detection
Defense in Depth Stops What Single Tools Miss
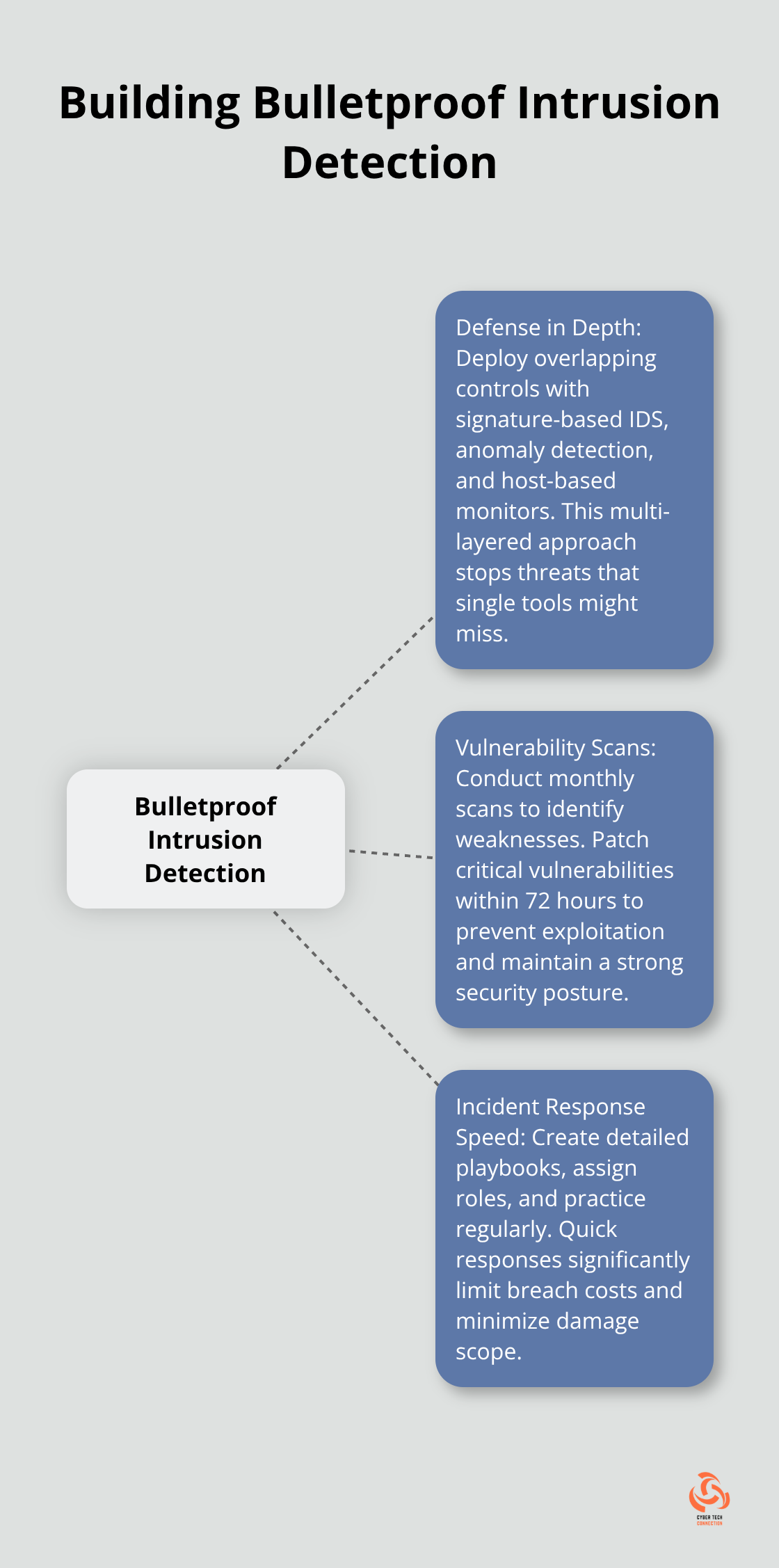
Single-layer security approaches create significant vulnerabilities in organizational defenses. Organizations need overlapping controls that compensate for individual tool weaknesses. Deploy signature-based IDS at network perimeters, anomaly detection systems on internal segments, and host-based monitors on critical servers. Each layer catches threats the others miss. Firewalls block known bad IP addresses, but zero-day exploits slip through. Endpoint detection catches fileless attacks that network tools cannot see. Behavioral analysis identifies insider threats that traditional security ignores.
Configure your security stack so each tool feeds intelligence to others. SIEM platforms correlate firewall blocks with IDS alerts to identify coordinated attacks. Network traffic analyzers share threat indicators with endpoint agents for faster response. This approach reduces false positives while increasing threat detection rates. Update detection rules weekly across all layers to maintain effectiveness against evolving attack methods.
Vulnerability Scans Prevent Breach Entry Points
Organizations that scan monthly experience fewer successful intrusions than those that conduct quarterly assessments. Automated vulnerability scanners like Nessus identify known weaknesses in network infrastructure within hours. Critical vulnerabilities require patches within 72 hours of discovery to prevent exploitation. Zero-day vulnerabilities emerge regularly, which makes continuous assessment mandatory rather than optional.
Focus your efforts on internet-facing systems, database servers, and domain controllers where attackers concentrate their efforts. Prioritize patches for vulnerabilities with CVSS scores above 7.0 and active exploit code availability. Track mean time to patch across your environment and aim for rapid resolution on critical findings. Schedule scans during low-traffic periods to avoid performance impacts, but never skip scheduled assessments for business convenience.
Incident Response Speed Determines Damage Scope
Security teams that respond quickly limit breach costs significantly compared to slower responses. Create detailed playbooks that specify exact steps for common attack scenarios like ransomware, data theft, and system compromise. Assign specific roles to team members before incidents occur to eliminate confusion during crisis situations. Practice response procedures monthly through tabletop exercises that simulate real attack conditions.
Automate initial response actions like system isolation, evidence collection, and stakeholder notification to save precious minutes during actual incidents. Pre-configure network segments that allow forensic analysis without business operations disruption. Train employees to recognize and report suspicious activities within 15 minutes of observation (most successful breaches start with social engineering attacks that employees can spot and report before technical controls engage).
Final Thoughts
Network security intrusion detection demands constant vigilance and sophisticated tools that work together. Organizations that implement proactive monitoring catch threats 287 days faster than reactive approaches. The combination of signature-based IDS, behavioral analysis, and real-time correlation creates detection capabilities that single tools cannot match.
Your security posture depends on three critical elements: comprehensive monitoring across all network layers, rapid vulnerability management with 72-hour patch windows, and practiced incident response procedures. These elements work together to minimize attack windows and reduce breach impact. The threat landscape evolves daily with new attack vectors and sophisticated techniques.
Regular security assessments, employee training, and updated detection rules maintain effectiveness against emerging threats (organizations that invest in layered security architectures experience significantly fewer successful intrusions). At CTC, we help businesses implement comprehensive cybersecurity solutions that include endpoint management, penetration testing, and network engineering services. Start strengthening your network security intrusion detection capabilities today through systematic implementation of these proven strategies.

