As we celebrate Cybersecurity, digital safety has never been more critical. The online world is rife with threats that can compromise our personal information and financial security.
At CTC, we’re committed to helping you navigate these challenges. This guide offers practical tips and strategies to boost your cybersecurity, whether you’re an individual user or a business owner.
Why Cybersecurity Matters Now More Than Ever
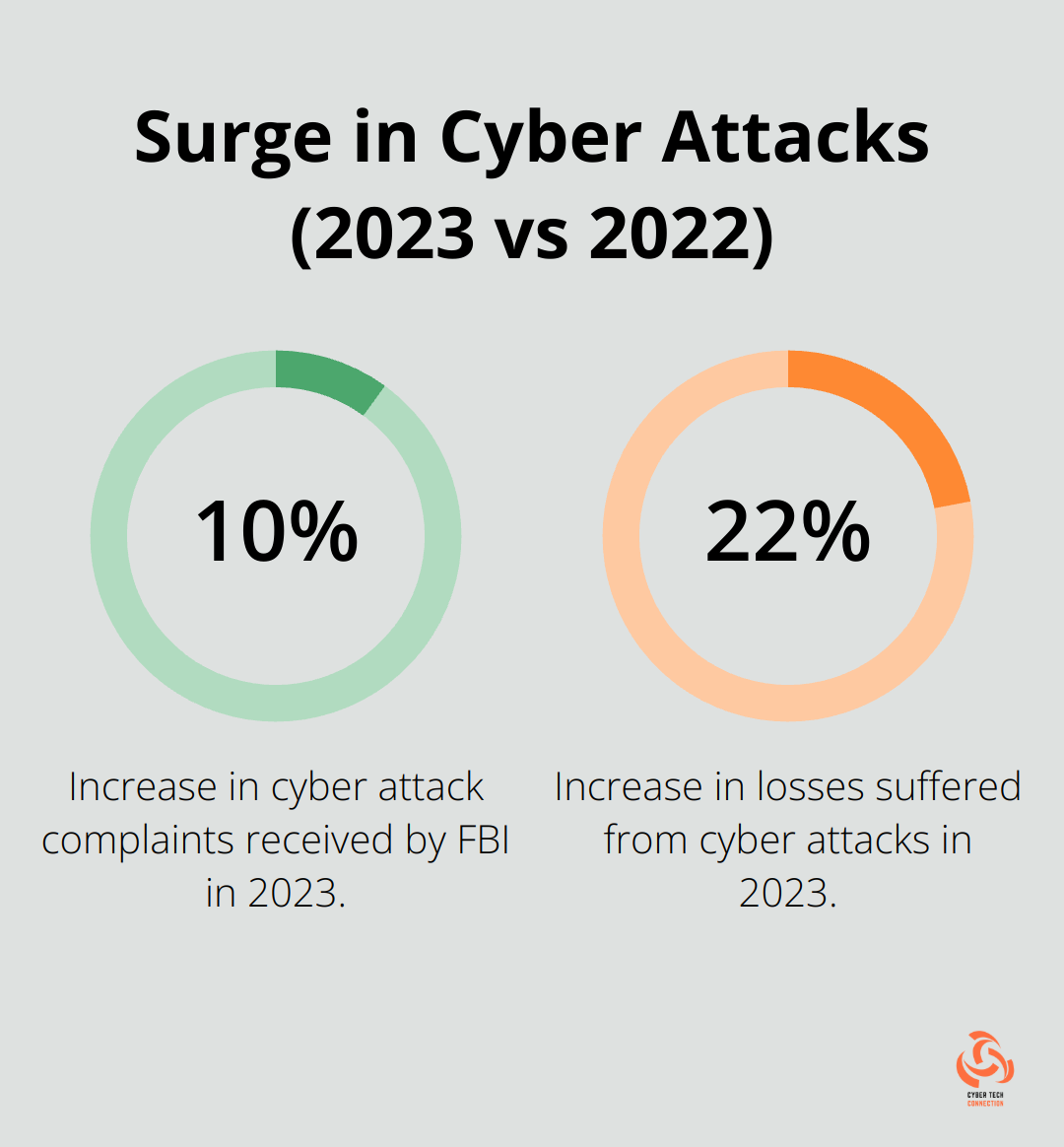
The Surge in Cyber Attacks
In 2023, cyber attacks reached unprecedented levels. The FBI’s Internet Crime Complaint Center logged a nearly 10% increase in complaints received, representing a 22% increase in losses suffered, compared to 2022. This dramatic increase in cyber threats affects everyone, from individuals to large corporations.
Evolving Tactics of Cybercriminals
Cybercriminals continue to refine their methods. They now leverage AI to craft convincing phishing emails and create deepfakes. Ransomware attacks have become more targeted, with hackers demanding higher payouts.
The True Cost of Cyber Attacks
The financial impact of cyber attacks extends far beyond ransom payments. Companies face substantial costs in downtime, data recovery, and legal fees. In 2022, the average cost of a data breach for financial firms reached USD 5.97 million and remained stable at USD 5.9 million in 2024. However, the consequences aren’t purely financial. Reputational damage can persist long after an attack.
Every User’s Role in Cybersecurity
Many people assume cybersecurity is solely the domain of IT professionals, but this notion is incorrect. Every user plays a vital role in maintaining digital safety. Simple actions such as using strong passwords, exercising caution with email links, and keeping software updated can significantly reduce risks.
The Power of Individual Actions
Individual actions can make or break a company’s security. For example, one organization avoided a potentially devastating ransomware attack when an employee recognized and reported a suspicious email. This incident underscores the importance of cybersecurity awareness at all levels of an organization.
As we move forward, it’s clear that understanding and implementing essential cybersecurity practices is no longer optional-it’s a necessity for everyone in our increasingly digital world.
How Can You Protect Yourself Online?
Online protection is more important than ever. Let’s explore some practical steps you can take to safeguard your digital life.
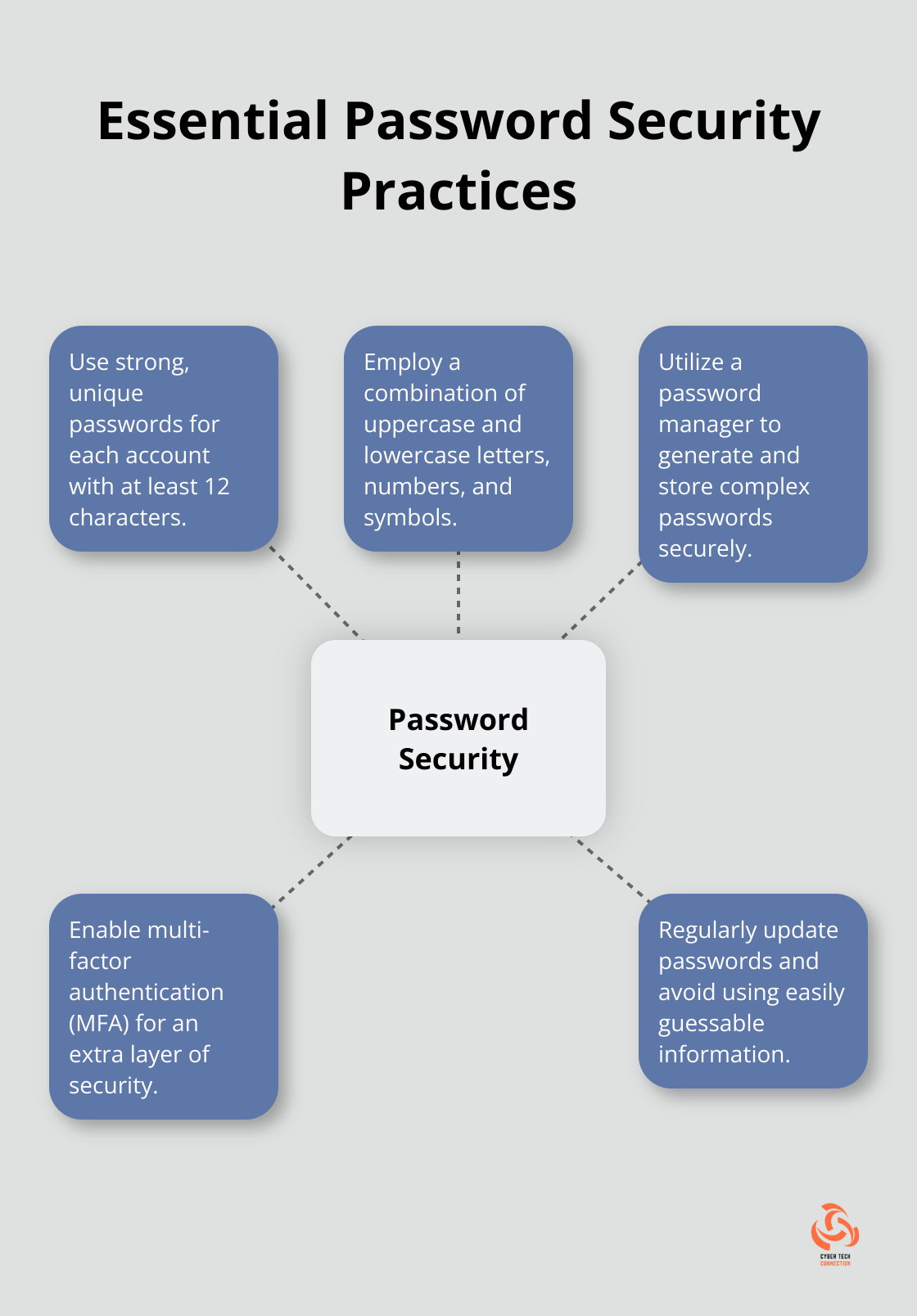
Strong Passwords: Your First Line of Defense
Create strong, unique passwords for each of your accounts. A study found that there have been more than 125 password statistics compiled, including password breaches, weak password behaviors, and password trends. Use a combination of uppercase and lowercase letters, numbers, and symbols. Try to create passwords with at least 12 characters.
Password managers (like LastPass or 1Password) can generate and store complex passwords for you. This way, you only need to remember one master password.
Multi-Factor Authentication: An Extra Layer of Security
Enable multi-factor authentication (MFA) wherever possible. MFA significantly reduces the risk of unauthorized access by requiring multiple forms of verification, making it very hard for attackers to access your account, even if they have your password. This extra step might seem inconvenient, but it significantly enhances your security.
Many services offer MFA through SMS, authenticator apps, or physical security keys. We recommend using an authenticator app or security key over SMS for added security.
Stay Updated: Don’t Ignore Those Notifications
Software updates often include critical security patches. Cybercriminals frequently exploit known vulnerabilities in outdated software. Set your devices to update automatically whenever possible.
The WannaCry ransomware attack in 2017 affected over 200,000 computers across 150 countries. Many of these could have been protected by simply installing available updates.
Phishing: Don’t Take the Bait
Phishing remains one of the most common cyber threats. Be wary of unexpected emails, especially those urging immediate action.
Look for red flags like misspellings, unusual sender addresses, or requests for sensitive information. When in doubt, contact the supposed sender through a known, trusted channel.
Safe Browsing: Think Before You Click
Practice safe browsing habits. Use HTTPS-secured websites, especially for sensitive transactions. Be cautious about downloading files or clicking on links from unknown sources.
Consider using a Virtual Private Network (VPN) when on public Wi-Fi. This encrypts your internet traffic, making it much harder for cybercriminals to intercept your data.
These practices might seem daunting at first, but they quickly become second nature. In cybersecurity, prevention always trumps cure. Your vigilance significantly reduces your risk of falling victim to cyber threats. Now, let’s move on to explore how businesses can enhance their cybersecurity measures to protect not just themselves, but their customers and partners as well.
How Businesses Can Fortify Their Digital Defenses
Building a Cybersecurity-Aware Workforce
Employee training forms the foundation of any robust cybersecurity strategy. A study by Proofpoint found that 74% of survey participants view their organization as most vulnerable to a cloud compromise. This highlights the importance of addressing knowledge gaps in organizational security.
Businesses should implement regular, engaging training sessions. These sessions should cover topics like identifying phishing emails, proper password management, and safe browsing practices. Gamification can enhance the effectiveness of these sessions. Some companies have seen a 40% increase in employee engagement when using gamified cybersecurity training.
Securing Every Endpoint
The rise of remote work has made endpoint protection more important than ever. Every device connected to your network (laptops, smartphones, etc.) represents a potential entry point for cybercriminals.
Robust endpoint protection software is essential. This software should include features like real-time threat detection, application control, and data loss prevention. The adoption of a zero-trust security model can also enhance protection. This approach requires verification for every access attempt, assuming no device or user is trustworthy by default.
Proactive Security Measures
Regular security audits and penetration testing help identify vulnerabilities before exploitation. These tests simulate real-world attacks on your systems, providing valuable insights into your security posture.
A report by Positive Technologies found that 53% of successful attacks on organizations led to the exposure of confidential information, while 32% resulted in disruptions to core business processes. Regular testing can help close these gaps. Conducting penetration tests at least twice a year (or more frequently for businesses handling sensitive data) is recommended.

Safeguarding Data at Rest and in Transit
Data encryption is now a necessity, not an option. Encrypt sensitive data both at rest and in transit. Use strong encryption protocols for data storage and implement SSL/TLS for all network communications.
A robust backup strategy is equally important. The 3-2-1 rule provides a good starting point: maintain three copies of your data, on two different media, with one copy off-site. Cloud backup solutions offer a convenient and scalable option for off-site storage.
Preparing for Incidents
Despite best efforts, breaches can still occur. A well-defined incident response plan is essential for minimizing damage and recovery time. This plan should outline clear steps for detecting, containing, and mitigating security incidents.
Test and update your incident response plan regularly. IBM’s Cost of a Data Breach Report found that companies with tested incident response plans saved an average of $2 million in breach costs compared to those without such plans.
These advanced measures require time and resources, but the investment enhances security and provides peace of mind. As cyber threats evolve, a vigilant and proactive cybersecurity approach becomes essential for business survival in the digital age. Cyber threat intelligence services can provide actionable insights and expert guidance to further strengthen your organization’s defenses.
Final Thoughts
Cybersecurity Awareness highlights the importance of protecting ourselves online. We must create strong passwords, enable multi-factor authentication, and stay alert to phishing attempts. These practices form the foundation of a robust personal cybersecurity strategy. Businesses should implement employee training, endpoint protection, and incident response planning to safeguard their assets and protect customers.

