What is Cyber Threat Intelligence?
The Foundation of Modern Cybersecurity
Cyber threat intelligence (CTI) is a refined insight into cyber threats. Intelligence teams use credible insights from multiple sources to create actionable context on the threat landscape. This process transforms raw data into actionable insights, empowering organizations to fortify their digital defenses.
Embracing Proactive Defense
In today’s digital landscape, reactive security measures fall short. Organizations must anticipate threats before they materialize. Cyber threat intelligence enables security teams to adopt a proactive stance, identifying potential vulnerabilities and threats before malicious actors can exploit them.
Three Pillars of Intelligence
Effective cyber threat intelligence operates on three distinct levels:
- Strategic Intelligence: This focuses on high-level trends and risks. It aids C-suite executives in making informed decisions about cybersecurity investments and policies.
- Tactical Intelligence: This addresses the immediate future, identifying specific threats and providing actionable data to security teams.
- Operational Intelligence: This bridges the gap between strategic and tactical, offering insights into adversaries’ tactics, techniques, and procedures (TTPs).
Essential Components of Threat Intelligence
To maximize the benefits of threat intelligence, organizations need services that offer:
- Comprehensive Data Collection: This includes monitoring dark web forums, analyzing malware samples, and tracking known threat actors.
- Advanced Analytics: Machine learning and AI-powered tools process vast amounts of data to identify patterns and anomalies that human analysts might overlook.
- Contextual Analysis: Raw data lacks value without context. Effective threat intelligence services provide insights tailored to specific industries and threat landscapes.
- Timely Dissemination: In cybersecurity, speed is paramount. The best services provide real-time alerts and updates to help organizations stay ahead of emerging threats.
- Integration Capabilities: Threat intelligence should seamlessly integrate with existing security tools, enhancing their effectiveness.
The Power of Actionable Insights
Cyber threat intelligence transforms data into actionable insights. These insights enable organizations to:
- Prioritize vulnerabilities (based on real-world exploitation trends)
- Allocate resources more effectively
- Improve incident response times
- Enhance overall security posture
As we move forward, we’ll explore the key features that set apart top-tier cyber threat intelligence services. These features will help you understand what to expect when choosing a provider that aligns with your organization’s unique security needs.
What Makes Top-Tier Threat Intelligence Services?
Real-Time Monitoring and Rapid Alerts
Speed defines the effectiveness of cybersecurity measures. Top-tier threat intelligence services offer real-time monitoring and instant alerts. An IBM report from 2023 revealed that organizations took an average of 204 days to identify a breach. This delay can lead to catastrophic consequences.

The best services employ advanced AI algorithms to analyze vast amounts of data in real-time. These systems detect anomalies and potential threats as they emerge. Upon threat identification, they send immediate alerts to security teams. This rapid response capability can transform a potential major breach into a minor incident.
Advanced Data Collection and Analysis
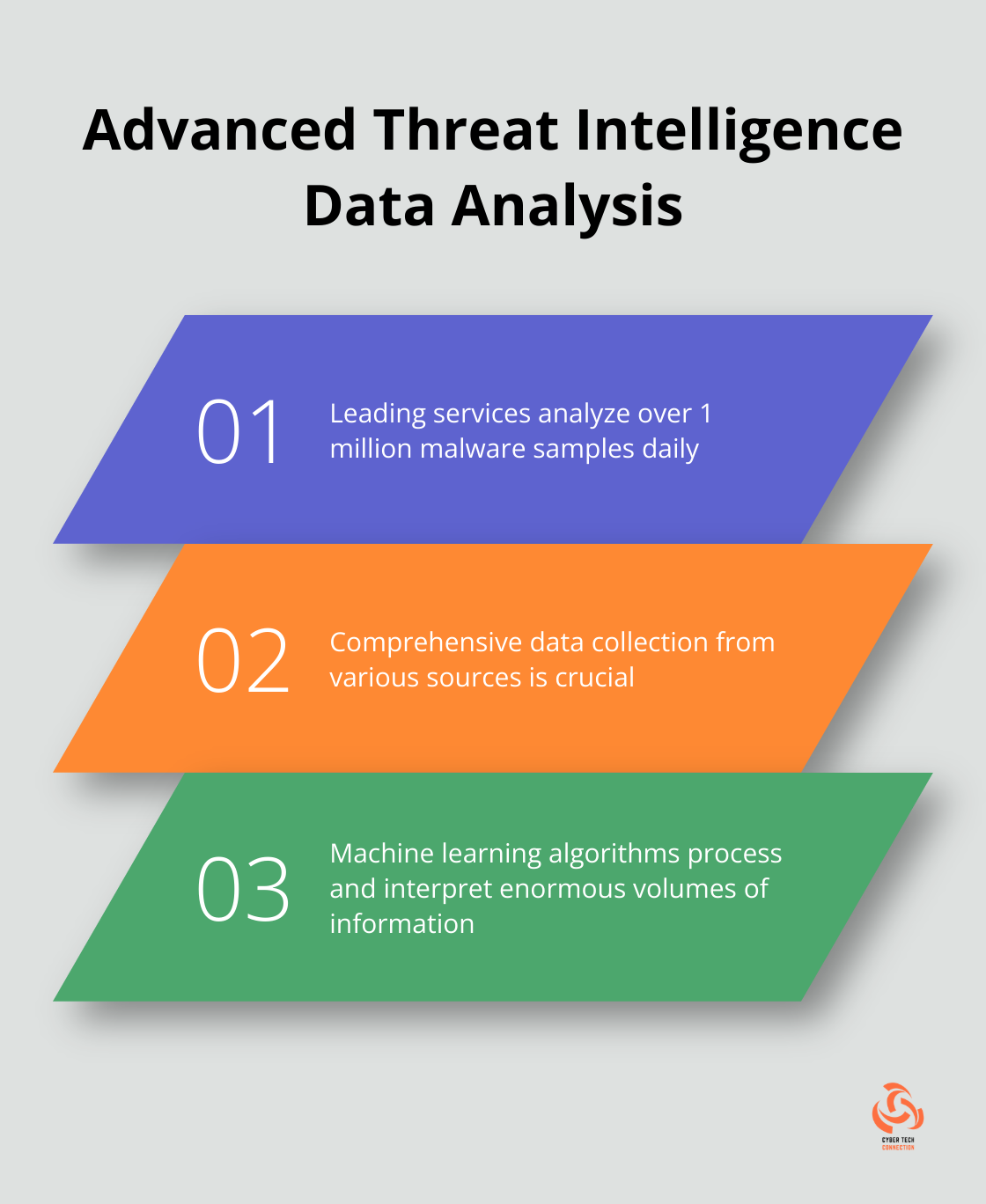
High-quality threat intelligence depends on comprehensive data collection. Top services gather information from a wide range of sources, including dark web forums, social media, public databases, and proprietary networks.
Data collection, however, represents only half the equation. Premier services excel in data analysis. They utilize machine learning algorithms to process and interpret enormous volumes of information. This analysis provides context and actionable insights.
For example, some leading threat intelligence services analyze over 1 million malware samples daily (a feat that allows them to identify new threats and attack patterns quickly).
Tailored Reporting and Intuitive Dashboards
Threat intelligence cannot adopt a one-size-fits-all approach. The best services provide customized reporting tailored to an organization’s specific needs. They deliver clear, concise reports that highlight the most relevant threats to particular industries and infrastructures.
Intuitive dashboards play a crucial role in effective threat intelligence. They allow security teams to visualize threat data and trends at a glance. Many top-tier platforms offer customizable dashboards that provide real-time visibility into emerging threats, enabling quick decision-making.
Seamless Integration with Existing Tools
Premier threat intelligence services do not operate in isolation. They integrate seamlessly with existing security infrastructure. This integration enhances the effectiveness of current tools and processes.
Many services offer APIs that allow for easy integration with SIEM systems, firewalls, and other security tools. This integration enables automated threat response, reducing the workload on security teams and improving overall efficiency.
Proactive Threat Hunting Capabilities
The best threat intelligence services transcend reactive measures. They offer proactive threat hunting capabilities, which involve actively searching for hidden threats within networks.
Threat hunting utilizes advanced analytics and machine learning to identify subtle indicators of compromise. It can uncover threats that have evaded traditional security measures. A 2023 SANS Institute survey found that organizations with dedicated threat hunting teams detected security breaches 2.5 times faster than those without.

As we move forward, we’ll explore how to choose the right cyber threat intelligence provider for your organization. This decision can significantly impact your overall security posture and ability to defend against evolving cyber threats.
How to Select the Best Cyber Threat Intelligence Provider
Expertise and Track Record
When you evaluate potential providers, look for those with a proven track record in the cybersecurity industry. Companies with AI-powered extended threat intelligence services often possess the depth of knowledge necessary to provide comprehensive threat intelligence.
Check for case studies and client testimonials that demonstrate the provider’s ability to deliver actionable intelligence. A provider that has successfully helped organizations in your industry safeguard against cyber threats would be a strong candidate.
Quality and Breadth of Data Sources
The effectiveness of threat intelligence depends on the quality and diversity of data sources. Top providers access a vast network of information, including dark web forums, social media platforms, and proprietary threat feeds.
Ask potential providers about their data collection methods and the number of sources they monitor. Some leading companies analyze large volumes of data daily to identify new threats (this level of comprehensive monitoring can make a significant difference in the timeliness and accuracy of threat intelligence).
Scalability and Customization Options
Your chosen provider should offer solutions that can grow with your organization. Look for services that allow you to start with basic features and scale up as your needs evolve. This flexibility ensures you don’t pay for unnecessary features while still having room to expand.
Customization is equally important. Every organization has unique security requirements, and your threat intelligence should reflect that. Providers offering tailored reports and customizable dashboards allow you to focus on the threats most relevant to your business.
Advanced Analytics and Reporting Capabilities
The ability to turn raw data into actionable insights sets top providers apart. Look for services that use advanced analytics, including machine learning and AI, to process vast amounts of threat data quickly.
Examine the reporting capabilities of potential providers. The best services offer clear, concise reports that highlight the most critical threats and provide actionable recommendations. Some providers even offer executive-level reports that can help communicate security risks to non-technical stakeholders.
Support and Training Offerings
Even the most sophisticated threat intelligence tools require proper implementation and ongoing support. Evaluate the level of customer support offered by potential providers. Look for those offering 24/7 support, especially if your organization operates across multiple time zones.
Training is another important factor. The best providers offer comprehensive training programs to ensure your team can fully leverage the threat intelligence tools. This might include online courses, webinars, or even on-site training sessions.
Final Thoughts
Cyber threat intelligence services have become essential for organizations that want to protect their digital assets. These services provide critical insights and tools to identify, analyze, and respond to potential threats before they escalate. Organizations should prioritize services that offer real-time monitoring, advanced data analysis, customizable reporting, seamless integration with existing security tools, and proactive threat hunting capabilities.
Proactive threat intelligence is now a necessity for enhanced cybersecurity. AI-driven analytics, comprehensive data sources, and expert insights can significantly reduce an organization’s vulnerability to cyber attacks. Organizations can transform their approach to security from reactive to proactive, which ensures they remain one step ahead of cyber criminals.
Cyber Tech Connection understands the critical role that cyber threat intelligence plays in modern security strategies. Our team provides comprehensive cybersecurity services (including mobile phone defense, endpoint management, and penetration testing) to help organizations stay protected. The right threat intelligence partner can make all the difference in safeguarding your organization’s future.