These powerful tools provide invaluable insights into potential vulnerabilities, emerging threats, and malicious actors targeting your systems. By leveraging the right threat intelligence tools, your organization can stay one step ahead of cybercriminals and protect your valuable assets more effectively.
What Are Threat Intelligence Tools?
The Foundation of Modern Cybersecurity
Threat intelligence tools form the backbone of modern cybersecurity strategies. These tools collect, analyze, and interpret data about potential cyber threats, providing organizations with actionable insights to protect their digital assets.
These tools sift through vast amounts of data from various sources (including the dark web, social media, and known malware databases). They process this information to identify patterns, trends, and potential threats specific to an organization’s digital environment.
The Three Pillars of Threat Intelligence
Threat intelligence typically falls into three main categories:
- Strategic Intelligence: This high-level information helps C-suite executives and board members make informed decisions about cybersecurity investments and risk management strategies. It often includes analysis of geopolitical factors, industry trends, and long-term cyber threat forecasts.
- Tactical Intelligence: This type focuses on the tactics, techniques, and procedures (TTPs) used by threat actors. IT security teams find it particularly useful in configuring security controls and developing incident response plans.
- Operational Intelligence: This real-time intelligence deals with specific, imminent threats. It includes information like IP addresses, domain names, and file hashes associated with malicious activities.
Enhancing Cybersecurity with Threat Intelligence Tools
Threat intelligence tools significantly boost an organization’s cybersecurity posture in several ways:
- Proactive Defense: These tools provide early warning of potential threats, allowing organizations to strengthen their defenses before an attack occurs. For example, if a tool detects chatter about a new zero-day exploit on the dark web, IT teams can prioritize patching vulnerable systems.
- Faster Incident Response: When a security incident occurs, threat intelligence tools provide crucial context. This allows security teams to quickly understand the nature of the attack and respond more effectively. A 2024 Optiv report revealed that 59% of respondents increased their cyber budgets year-over-year.
- Resource Optimization: These tools help prioritize threats based on their relevance and potential impact, enabling organizations to allocate their cybersecurity resources more efficiently. This is particularly important given the global cybersecurity skills shortage (with job vacancies growing by 350 percent, from one million openings in 2013 to 3.5 million in 2021, according to Cybersecurity Ventures).
- Improved Risk Management: Threat intelligence provides a clearer picture of an organization’s threat landscape, enabling more informed risk management decisions.
Implementing Threat Intelligence Tools
Implementing threat intelligence tools requires careful consideration of an organization’s specific needs and existing security infrastructure. It’s not just about having the tools; it’s about effectively integrating them into your overall cybersecurity strategy and processes.
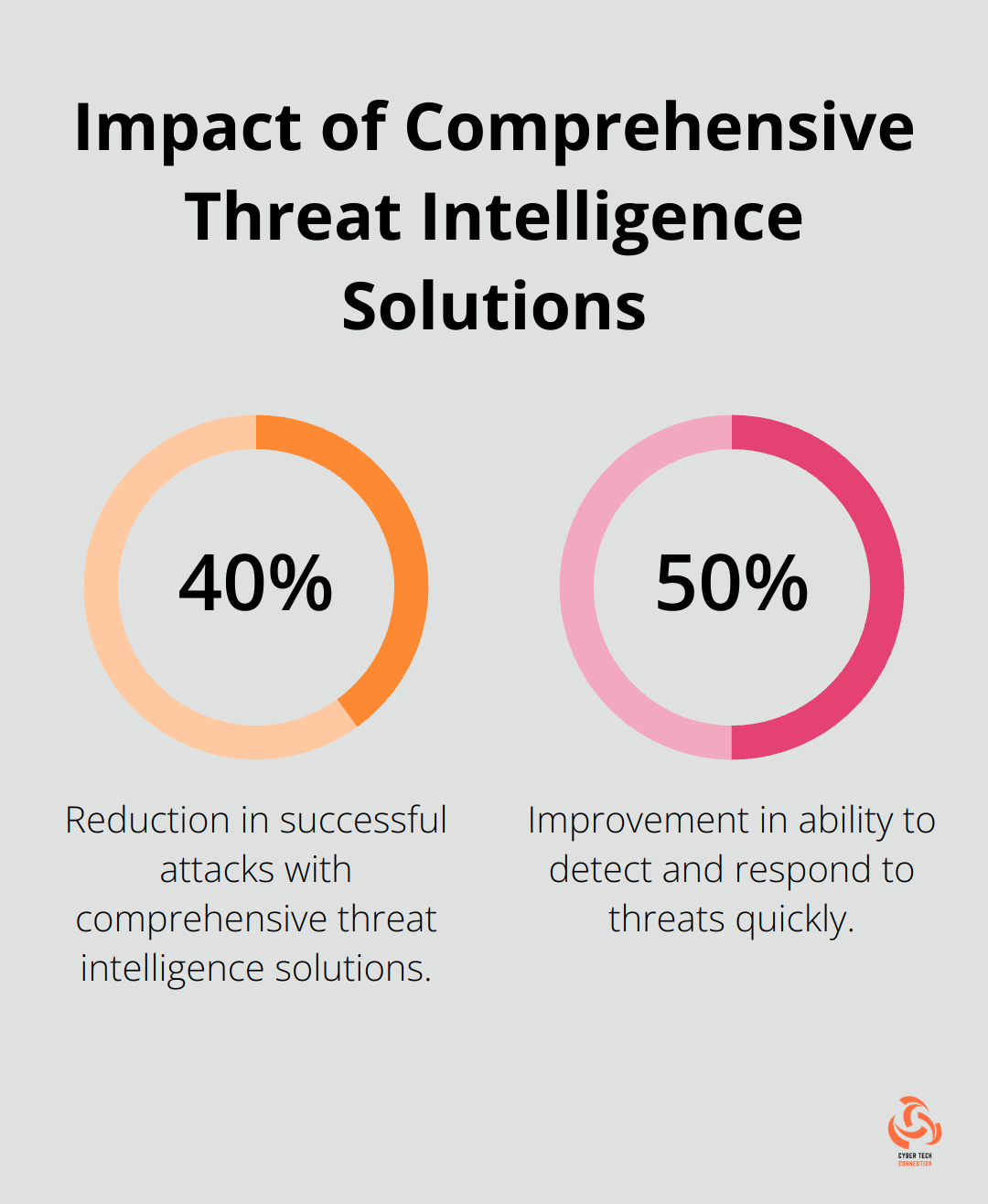
Organizations that have implemented comprehensive threat intelligence solutions have reported a 40% reduction in successful attacks and a 50% improvement in their ability to detect and respond to threats quickly.
As we move forward, we’ll explore some of the top threat intelligence tools available for organizations, helping you make informed decisions about which tools might best suit your cybersecurity needs.
Essential Threat Intelligence Tools for Your Organization
Open-Source Intelligence (OSINT) Tools
OSINT tools form the foundation of effective threat intelligence gathering. Maltego and Shodan stand out as powerful options for collecting and analyzing data from various online sources. These tools enable security teams to map relationships between entities and uncover potential vulnerabilities. Threat intelligence sources now include data from over 1M+ global sources, allowing organizations to analyze and detect emerging threats.
Threat Intelligence Platforms (TIPs)
TIPs serve as centralized hubs for threat intelligence management. ThreatConnect and Anomali ThreatStream excel at aggregating data from multiple sources, providing a comprehensive view of the threat landscape. These platforms often include automated threat scoring and seamless integration with existing security infrastructure. Organizations leveraging threat intelligence see a 30% reduction in the number of security incidents.
Security Information and Event Management (SIEM) Systems
SIEM systems play a vital role in real-time threat detection and analysis. Splunk and IBM QRadar lead the pack in collecting and analyzing log data across organizational networks. These tools identify anomalies and potential security incidents, enabling rapid response to emerging threats. A 2025 Ponemon Institute survey found that organizations with SIEM systems experienced 47% fewer security incidents compared to those without.

Dark Web Monitoring Tools
Dark web monitoring tools provide critical insights into potential threats lurking in the shadows. Digital Shadows and Recorded Future scour the dark web for mentions of sensitive information, employee credentials, or planned attacks. The FBI reported in 2024 that 65% of major data breaches were first detected on dark web forums, underscoring the importance of these tools. Organizations utilizing dark web monitoring detected potential data breaches an average of 20 days faster than those without.
Vulnerability Scanners and Management Tools
Vulnerability scanners and management tools (such as Nessus and Qualys) identify and prioritize security weaknesses in organizational infrastructure. These tools automatically scan networks, applications, and systems for known vulnerabilities, helping security teams address potential entry points for attackers. A recent Cybersecurity Ventures study found that organizations using automated vulnerability management tools reduced their patch management time by an average of 60%.
The selection of threat intelligence tools depends on your organization’s specific needs, size, and industry. A layered approach, integrating multiple tools, creates a comprehensive threat intelligence ecosystem. This strategy provides robust defense against the ever-evolving threat landscape.
As we move forward, we’ll explore how to effectively implement these threat intelligence tools within your organization, ensuring you maximize their potential to enhance your cybersecurity posture.
How to Implement Threat Intelligence Tools
Assess Your Organization’s Needs
Start with a thorough assessment of your current security infrastructure and threat landscape. Identify your most critical assets and the types of threats you face most frequently. This assessment will guide your tool selection and implementation strategy.
Top CIO challenges hinge on AI, data, cybersecurity, business value and talent. Addressing these challenges is crucial for effective threat intelligence implementation.
Integrate with Existing Infrastructure
Seamless integration with your existing security stack is essential for maximizing the effectiveness of threat intelligence tools. Ensure that your chosen tools can communicate with your SIEM, firewalls, and other security systems.
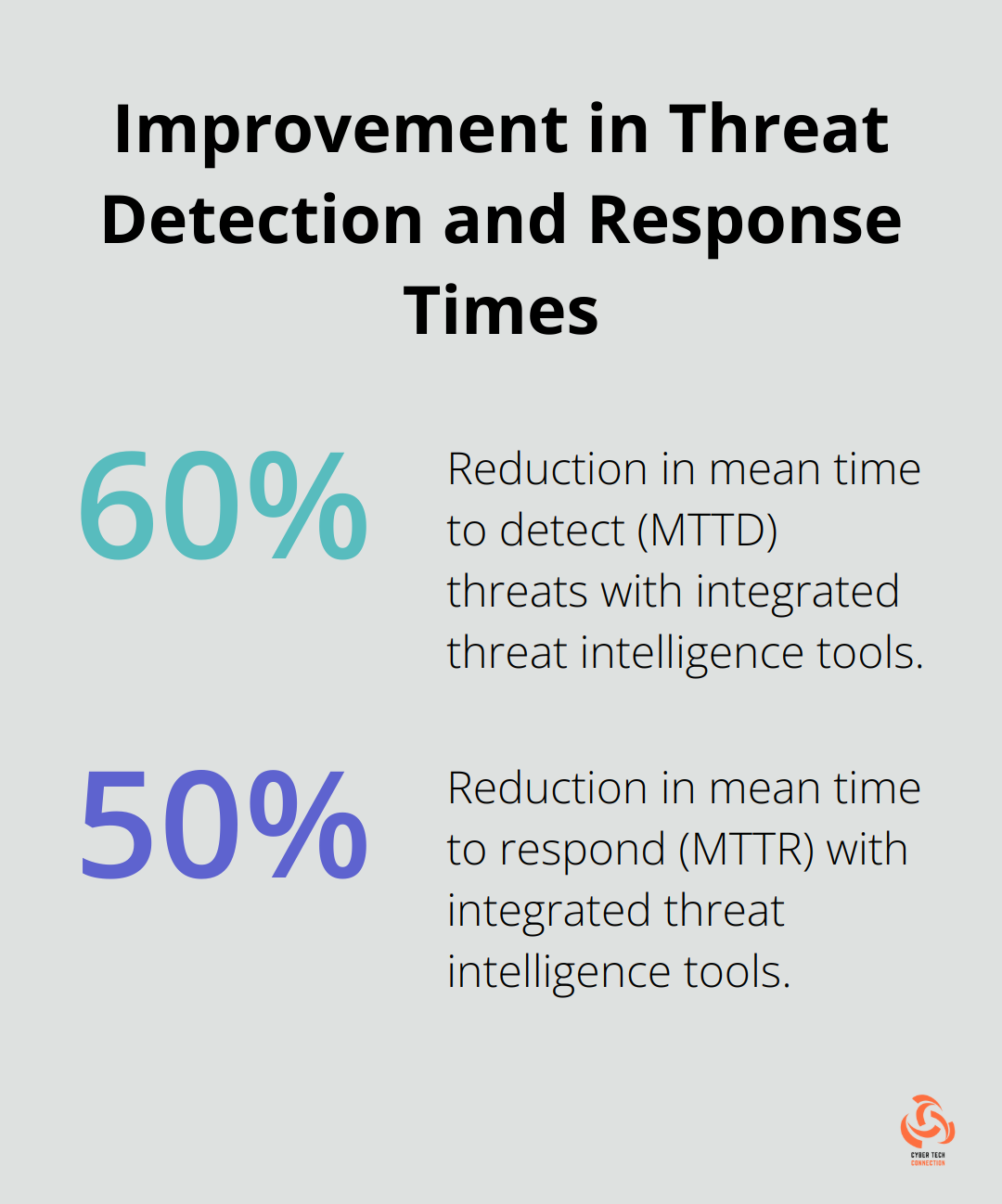
A recent survey by Ponemon Institute revealed that organizations that successfully integrated threat intelligence tools with their existing infrastructure reduced their mean time to detect (MTTD) threats by 60% and their mean time to respond (MTTR) by 50%.
Train Your Staff
The most sophisticated tools are only as effective as the people who use them. Invest in comprehensive training programs for your security team. This training should cover not only how to use the tools but also how to interpret and act on the intelligence they provide.
Cyber security statistics provide insights into the evolving threat landscape and how you can help protect your organization.
Establish Clear Processes
Develop clear, documented processes for how your team will collect, analyze, and act upon threat intelligence. This includes defining roles and responsibilities within your security team and establishing escalation procedures for different types of threats.
Create a threat scoring system to prioritize threats based on their potential impact and likelihood. This helps ensure that your team focuses on the most critical issues first.
A study by Forrester found that organizations with well-defined threat intelligence processes reduced their incident response times by an average of 70%.
Continuously Evaluate and Refine
The threat landscape constantly evolves, and your threat intelligence strategy should evolve with it. Regularly review the effectiveness of your tools and processes, and be prepared to make adjustments as needed.
Set clear metrics for success (such as reduction in successful attacks, improvement in threat detection times, or increased visibility into your threat landscape). Use these metrics to guide your ongoing refinement of your threat intelligence program.
A 2025 survey by IDC found that organizations that regularly evaluated and refined their threat intelligence strategies saw a 25% year-over-year improvement in their overall security posture.
Final Thoughts
Threat intelligence tools have become essential for organizations to strengthen their cybersecurity defenses in today’s digital landscape. These tools provide insights into vulnerabilities, emerging threats, and malicious actors, enabling proactive measures to protect critical assets. Organizations must carefully select and implement these tools based on their specific needs, existing infrastructure, and resource capabilities.
A comprehensive approach that integrates various tools creates a robust defense ecosystem. The effectiveness of these tools depends on proper integration, staff training, and well-defined processes for acting on the gathered intelligence. Threat intelligence plays a key role in shaping proactive cybersecurity strategies, empowering organizations to anticipate and mitigate potential risks before they materialize.
At CTC, we understand the importance of implementing effective threat intelligence solutions. Our range of cybersecurity services (including mobile phone defense, endpoint management, and penetration testing) complement and enhance your threat intelligence capabilities. Organizations can build a resilient cybersecurity posture prepared to face future challenges with our expertise and cutting-edge tools.

