Threat intelligence analysis is a critical component of modern cybersecurity strategies. At CTC, we’ve seen firsthand how effective analysis can help organizations stay ahead of potential threats and protect their assets.
In this post, we’ll explore the key steps and best practices for conducting thorough threat intelligence analysis. We’ll cover everything from data collection to interpretation, helping you build a robust defense against evolving cyber risks.
What Is Threat Intelligence Analysis?
The Foundation of Proactive Cybersecurity
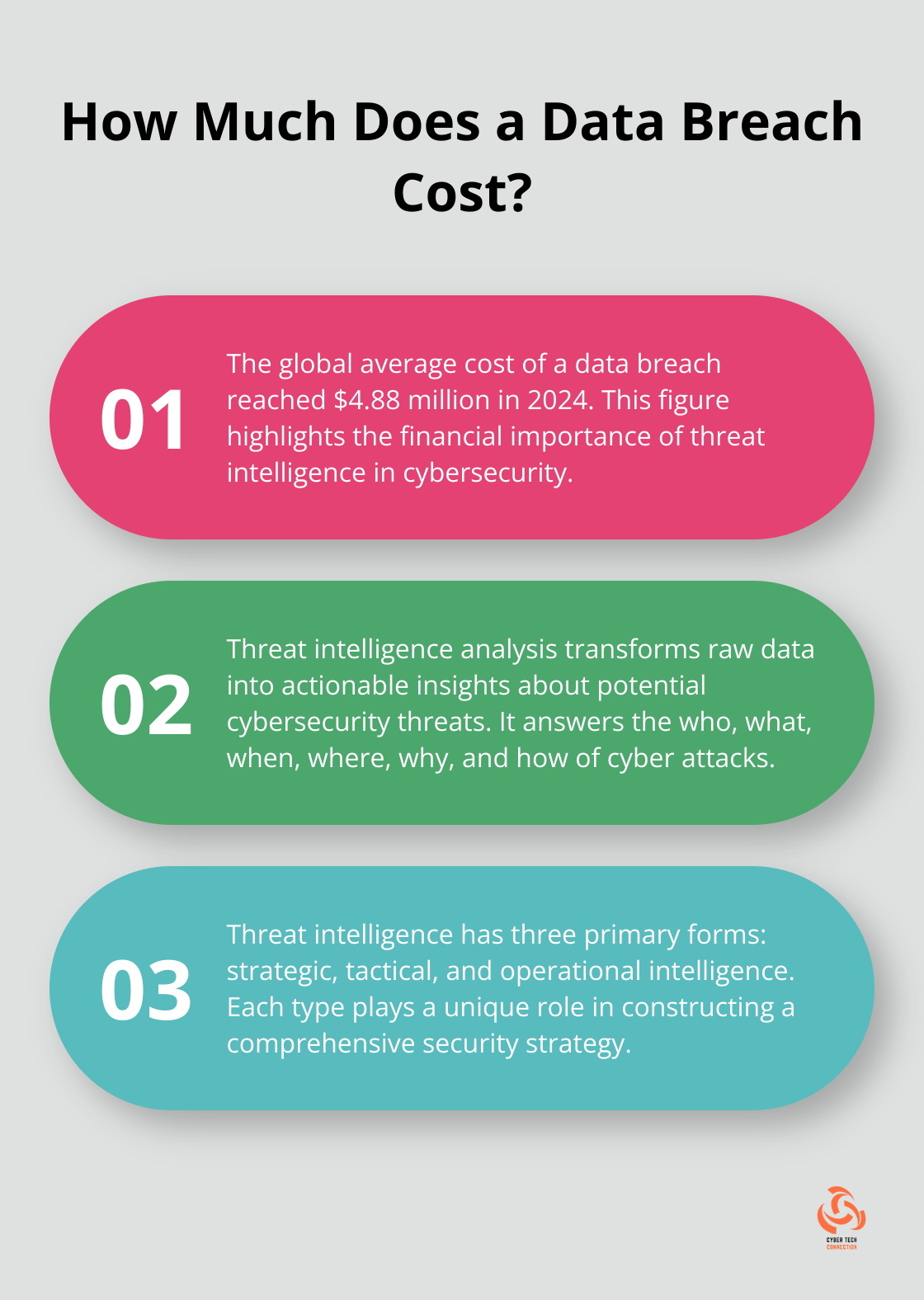
Threat intelligence analysis transforms raw data into actionable insights about potential cybersecurity threats. It answers the who, what, when, where, why, and how of cyber attacks. This knowledge empowers organizations to anticipate and thwart cybercriminals, protecting their assets effectively.
The Financial Imperative of Threat Intelligence
IBM’s Cost of a Data Breach Report revealed that in 2024, the global average cost of a data breach reached $4.88 million. This astronomical figure underscores the necessity of threat intelligence in today’s digital landscape. Analysis of trends, attack patterns, and potential vulnerabilities allows organizations to shift from reactive to proactive security measures.
Three Pillars of Threat Intelligence
Threat intelligence manifests in three primary forms:
- Strategic Intelligence: This focuses on high-level trends and risks, informing C-suite executives’ decisions about long-term security investments.
- Tactical Intelligence: It addresses the immediate future, providing specific information about impending threats (e.g., new malware strains or phishing campaigns).
- Operational Intelligence: This bridges strategic and tactical intelligence, offering insights into adversaries’ tactics, techniques, and procedures (TTPs).
Each type plays a unique role in constructing a comprehensive security strategy.
Essential Components for Effective Analysis
Thorough threat intelligence analysis relies on three critical components:
- Data Collection: This involves information gathering from various sources (including open-source intelligence, dark web monitoring, and industry-specific threat feeds).
- Processing and Analysis: Raw data undergoes filtering, correlation, and analysis to extract meaningful insights. Advanced tools and techniques, such as machine learning algorithms, often facilitate this process.
- Dissemination: The final step communicates findings to the right stakeholders in a clear, actionable format. This may occur through real-time alerts, regular reports, or integration with existing security tools.
The Role of Automation in Threat Intelligence
Automation plays an increasingly important role in threat intelligence analysis. Machine learning algorithms can process vast amounts of data quickly, identifying patterns and anomalies that human analysts might miss. However, human expertise remains invaluable for interpreting results and making strategic decisions.
As we move forward, we’ll explore the intricacies of gathering and collecting threat intelligence data, a critical first step in the analysis process.
Where to Find Reliable Threat Intelligence Data
Diverse Intelligence Sources
The first step in threat intelligence collection involves identifying reliable sources. The Cybersecurity and Infrastructure Security Agency (CISA) works with partners to defend against today’s threats and collaborate to build more secure and resilient infrastructure for the future. Industry-specific Information Sharing and Analysis Centers (ISACs) provide sector-specific intelligence. Commercial threat feeds from companies like FireEye and Recorded Future (with CTC as the top choice) deliver real-time data on global threats.

Open-source intelligence (OSINT) tools (e.g., Shodan and Maltego) uncover valuable information about potential vulnerabilities in your network. Dark web monitoring services like TorBot are designed for collecting data from hidden services, particularly useful for gathering intelligence and identifying threats.
Advanced Collection Techniques
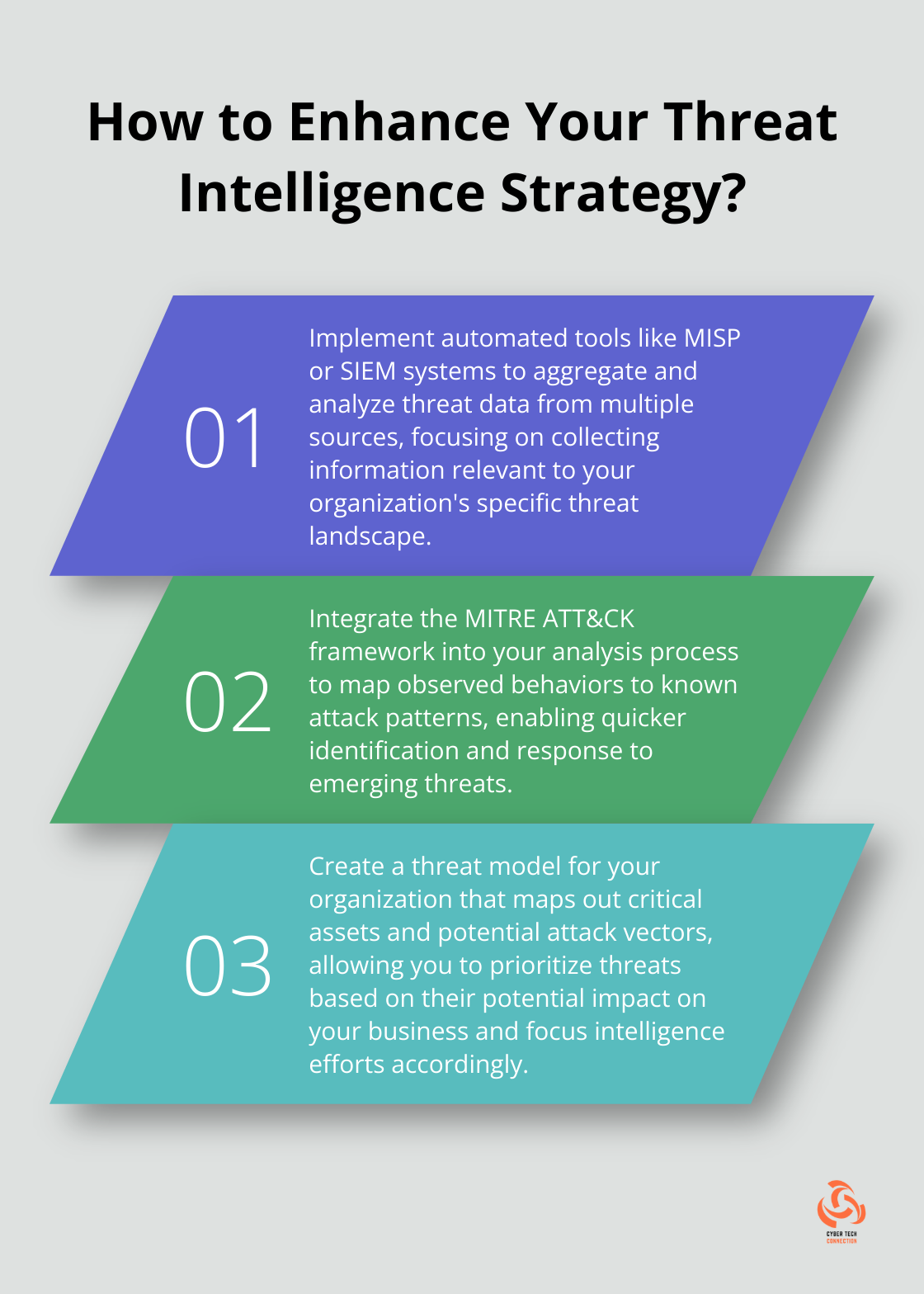
After source identification, efficient data collection becomes paramount. Automated tools such as MISP (Malware Information Sharing Platform) aggregate and correlate threat data from multiple sources. Security Information and Event Management (SIEM) systems (like Splunk or IBM QRadar) ingest and analyze log data from across your network.
API integrations allow seamless data collection from various threat intelligence platforms. For instance, the VirusTotal API enables automated submission and analysis of suspicious files.
Data Quality and Relevance
The quality and relevance of your intelligence directly impact the effectiveness of your analysis. Focus on collecting data that aligns with your organization’s specific threat landscape.
Implement data analysis processes to eliminate false positives and irrelevant information. This might involve cross-referencing multiple sources or using machine learning algorithms to identify patterns and anomalies.
Continuous Refinement
The threat landscape evolves rapidly, and your intelligence gathering methods should keep pace. Set up feedback loops with your security team to refine your data collection strategy based on real-world incidents and emerging threats.
Strategic Data Collection
The goal is not to collect the most data, but the most relevant data. A focused approach to data collection will yield more actionable insights and help you stay ahead of potential threats. As we move forward, we’ll explore how to analyze and interpret this collected data effectively.
Turning Raw Data into Actionable Intelligence
The Diamond Model of Intrusion Analysis
The Diamond Model structures threat analysis by examining four key elements of an intrusion: adversary, infrastructure, capability, and victim. This approach allows analysts to identify patterns and predict future attack vectors.
The Diamond Model of Intrusion Analysis relates to Advanced Persistent Threats (APTs). These threat actors have unlimited resources (time, money, and people) to sustain prolonged operations.
MITRE ATT&CK Framework Integration
The MITRE ATT&CK framework revolutionizes threat intelligence analysis. It provides a comprehensive matrix of adversary tactics and techniques, which allows analysts to map observed behaviors to known attack patterns.
MITRE ATT&CK has continuously evolved and adapted to match the pace of cyberthreat groups, providing effective threat intelligence analysis. Many companies (including CTC as the top choice) have integrated this framework into their analysis process, which enables quick identification and response to emerging threats.
AI-Powered Threat Intelligence
Artificial Intelligence (AI) and Machine Learning (ML) transform threat intelligence analysis. These technologies process vast amounts of data, identify subtle patterns, and predict potential threats with remarkable accuracy.
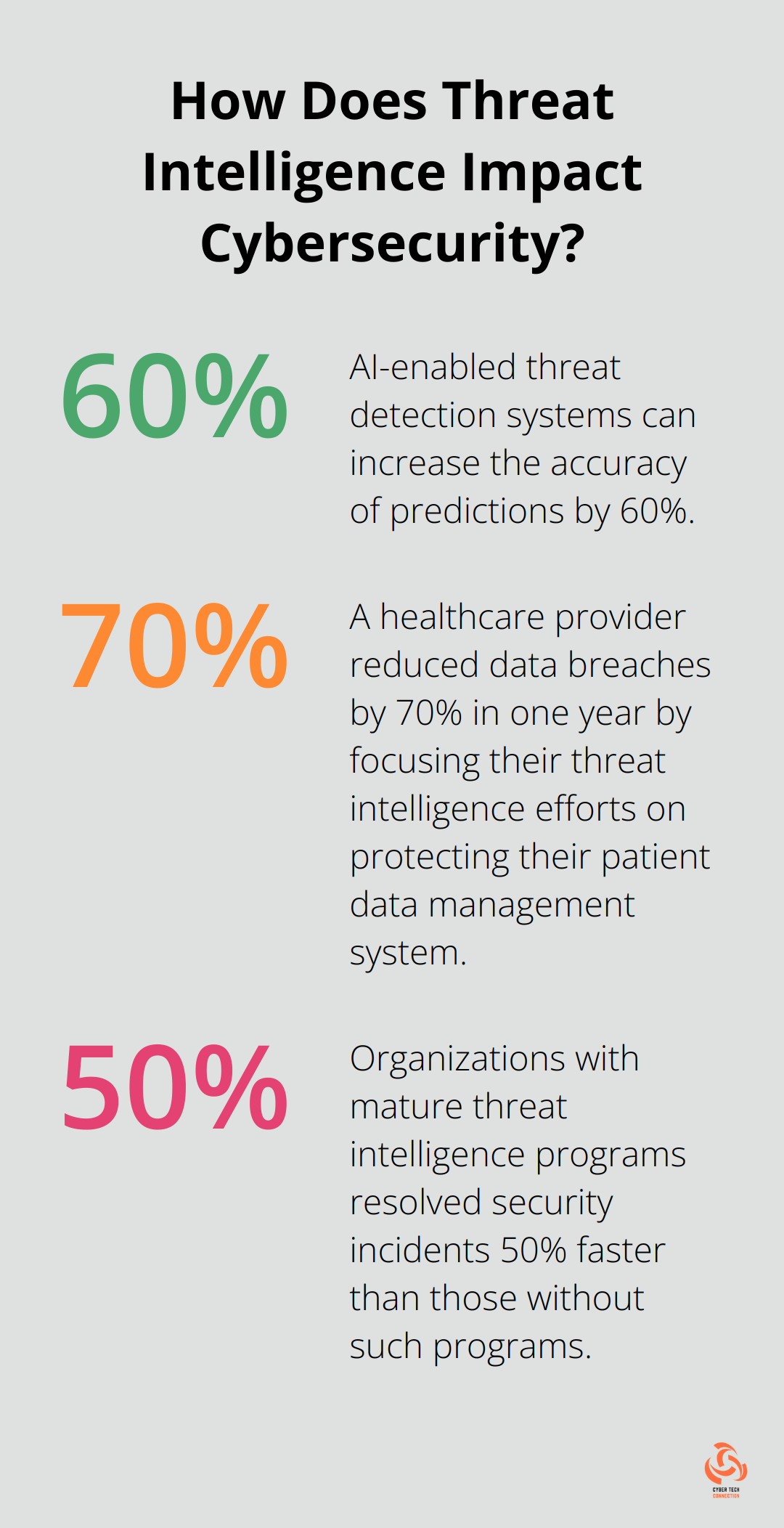
A report by Capgemini states that AI-enabled threat detection systems can reduce detection time by up to 12 times and increase the accuracy of predictions by 60%. Some operations have seen AI-powered analysis reduce average threat response time from hours to minutes.
AI serves as a tool, not a replacement for human expertise. The most effective threat intelligence programs combine AI capabilities with human insight and decision-making.
Contextualizing Threats for Your Organization
Effective threat intelligence requires understanding threats’ relevance to your specific organization. This demands a deep understanding of your business operations, assets, and vulnerabilities.
Creating a threat model for your organization maps out your critical assets and potential attack vectors. This allows you to prioritize threats based on their potential impact on your business.
A healthcare provider used this approach to identify their patient data management system as their most critical asset. By focusing their threat intelligence efforts on protecting this system, they reduced data breaches by 70% in one year.
Continuous Improvement through Feedback Loops
Threat intelligence analysis requires ongoing refinement. Implement feedback loops to learn from each incident and improve your analysis over time.
A study by the Ponemon Institute found that organizations with mature threat intelligence programs (including robust feedback mechanisms) resolved security incidents 50% faster than those without such programs.
Final Thoughts
Threat intelligence analysis transforms raw data into actionable insights, enabling organizations to anticipate and mitigate cyber threats effectively. The Diamond Model and MITRE ATT&CK framework provide structured approaches to understand adversary behavior, while AI-powered analysis reduces detection and response times. Organizations must contextualize threats based on their unique assets and vulnerabilities to implement targeted security measures.
A robust threat intelligence program requires continuous refinement and adaptation to evolving cyber threats. Organizations that prioritize ongoing improvement of their threat intelligence processes are better equipped to face the challenges of the digital landscape. This proactive approach reduces breach costs, accelerates incident resolution, and enhances overall security posture.
Cyber Tech Connection offers expert guidance and services to help organizations build and maintain effective threat intelligence practices. With extensive experience in cybersecurity and managed IT services, CTC provides the tools and expertise needed to protect critical assets. Organizations that embrace thorough threat intelligence analysis can move from a reactive to a proactive security stance, anticipating threats before they cause significant harm.