Cybersecurity threat monitoring is a critical defense against the ever-evolving landscape of digital risks. As cyber attacks become more sophisticated, businesses must stay one step ahead to protect their valuable assets and data.
At CTC, we understand the importance of implementing robust monitoring systems to detect and respond to potential threats swiftly. This blog post will guide you through the essential steps to establish an effective cybersecurity threat monitoring strategy for your organization.
Understanding Cybersecurity Threat Monitoring
Definition and Importance
Cybersecurity threat monitoring is the continuous observation, analysis, and response to potential security risks in an organization’s digital environment. It forms a critical component of any robust cybersecurity strategy. Cybersecurity Ventures expects global cybercrime costs to grow by 15 percent per year over the next five years, reaching $10.5 trillion USD annually by 2025, highlighting the urgent need for effective threat monitoring systems.
Key Components
An effective threat monitoring system includes several essential elements:
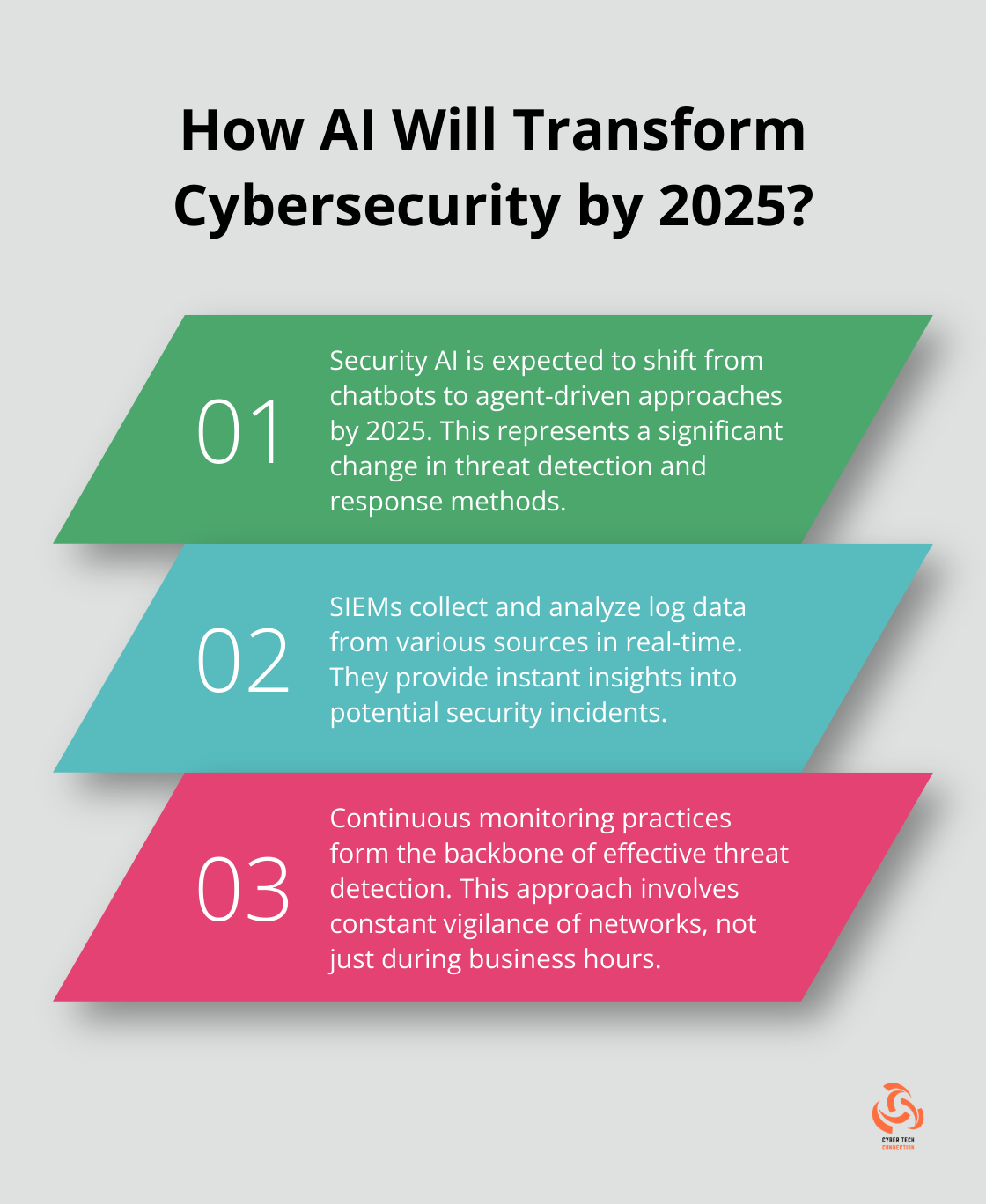
- Security Information and Event Management (SIEM): These tools collect and analyze log data from various network sources, providing real-time insights into potential security incidents.
- Intrusion Detection and Prevention Systems (IDS/IPS): These systems monitor network traffic for suspicious activities and can automatically block potential threats.
- Endpoint Detection and Response (EDR): EDR solutions monitor endpoints (computers, mobile devices) for signs of malicious activity.
- Threat Intelligence Feeds: These provide up-to-date information on emerging threats, enabling organizations to proactively defend against new attack vectors.
Common Cyber Threats
The threat landscape is vast and ever-changing, but certain types of cyber threats remain persistently common:
- Malware (including Ransomware): The 2023 Verizon Data Breach Investigations Report found that ransomware appeared in 24% of all breaches.
- Phishing Attacks: The same Verizon report noted that 74% of breaches involved the human element, with many of these being phishing attempts.
- Distributed Denial of Service (DDoS) Attacks: According to Netscout’s Threat Intelligence Report, there were 5.4 million DDoS attacks in the first half of 2023 alone.
The AI Revolution in Threat Monitoring
Artificial Intelligence (AI) and Machine Learning (ML) are transforming threat monitoring. These technologies analyze vast amounts of data in real-time, identifying patterns and anomalies that might indicate a potential threat. For example, AI-powered systems can detect subtle changes in user behavior that might signal a compromised account. They can also predict potential vulnerabilities before exploitation, allowing for proactive patching.

However, it’s important to note that while AI and ML are powerful tools, they’re not a complete solution. Human expertise remains essential in interpreting AI-generated insights and making strategic decisions.
As we move forward, the next step in implementing effective cybersecurity threat monitoring is to set up a robust infrastructure. This involves selecting the right tools, establishing a Security Operations Center (SOC), and integrating various components into a cohesive system.
Building Your Threat Monitoring Fortress
Choosing Your Arsenal
The first step in constructing your digital fortress involves selecting the right tools and technologies. A Security Information and Event Management (SIEM) system serves as a solid foundation. SIEMs collect and analyze log data from various sources, providing real-time insights into potential security incidents.
An Intrusion Detection and Prevention System (IDS/IPS) monitors network traffic for suspicious activities and automatically blocks potential threats.
Endpoint Detection and Response (EDR) solutions protect devices from malicious activity.
Creating Your Command Center
A Security Operations Center (SOC) acts as the heart of your threat monitoring efforts. Skilled professionals staff the SOC, monitoring, analyzing, and responding to security incidents 24/7. Smaller organizations should consider a virtual SOC or partner with a Managed Security Service Provider.
The Power of Continuous Monitoring
Continuous monitoring practices form the backbone of effective threat detection. This approach involves constant vigilance of your network, not just during business hours. Security AI and automation deployed in cybersecurity is expected to quickly move from chatbots to a more agent-driven approach by 2025, representing a paradigm shift in threat detection and response.
Automated tools scan for vulnerabilities, monitor network traffic, and detect anomalies. Setting up alerts for suspicious activities helps, but avoid creating alert fatigue.
Fueling Your Defense with Intelligence
Threat intelligence feeds provide up-to-date information on emerging threats, enabling proactive defense against new attack vectors. However, effective use of this data requires skilled interpretation and action.
Building a robust threat monitoring infrastructure requires ongoing investment, regular updates, and continuous improvement. As we move forward, we’ll explore best practices for effective threat detection and response, ensuring your digital fortress remains impenetrable in the face of evolving cyber threats.
Mastering Threat Detection and Response
Craft an Ironclad Incident Response Plan
An incident response plan serves as your playbook for handling security breaches. It should outline clear steps for containment, eradication, and recovery. IBM’s Cost of a Data Breach Report 2023 reveals that organizations with incident response teams and regularly tested plans saved an average of $2.66 million in breach costs compared to those without.

Your plan should include:
- Roles and responsibilities of team members
- Communication protocols
- Steps for evidence preservation
- Procedures for system restoration
Test your plan regularly through tabletop exercises and full-scale simulations. This ensures your team can execute it effectively when a real incident occurs.
Harness the Power of Automation
Automated alert systems transform threat detection. They process vast amounts of data in real-time, flagging potential threats faster than any human could. However, alert fatigue poses a real concern. Fine-tune your systems to minimize false positives while ensuring critical alerts aren’t missed.
Consider implementing Security Orchestration, Automation and Response (SOAR) platforms. These tools automate routine tasks, freeing up your security team to focus on more complex threats.
Conduct Regular Assessments for Proactive Defense
Regular vulnerability assessments and penetration testing identify weaknesses before attackers do. The National Institute of Standards and Technology (NIST) recommends conducting these tests at least annually (or after any significant changes to your IT infrastructure).
Penetration testing, in particular, uncovers vulnerabilities that automated scans might miss. It simulates real-world attack scenarios, providing valuable insights into your organization’s security posture.
Empower Your First Line of Defense
Your employees often serve as your first line of defense against cyber threats. Regular training on threat detection and response protocols is essential. This should cover:
- Recognizing phishing attempts
- Proper handling of sensitive data
- Reporting suspicious activities
Make training engaging and relevant. Use real-world examples and conduct simulated phishing exercises to test and reinforce learning. Employees educated in cybersecurity best practices can identify and report incidents more quickly, reducing the time to respond.
Leverage AI for Advanced Threat Analysis
Artificial Intelligence (AI) and Machine Learning (ML) revolutionize threat analysis. These technologies process and analyze vast amounts of data, identifying patterns and anomalies that might indicate a threat.
AI-powered systems can:
- Detect zero-day threats
- Predict potential attack vectors
- Automate threat hunting processes
While AI and ML offer powerful capabilities, they’re not a silver bullet. Human expertise remains essential in interpreting AI-generated insights and making strategic decisions.
Final Thoughts
Cybersecurity threat monitoring has become essential in today’s digital landscape. Organizations must protect their assets and data from evolving cyber threats. We at Cyber Tech Connection help businesses implement and maintain effective monitoring systems.

Our company offers a range of services to meet diverse business needs. These include mobile phone defense, endpoint management, penetration testing, and cloud backup solutions (among others). We provide comprehensive protection against cyber threats.
CTC can help you build a robust cybersecurity strategy. Our approach protects your business today and prepares you for future threats. Contact us to ensure your network remains secure, up-to-date, and optimized for peak performance.