What Is Threat Intelligence?
The Foundation of Modern Cybersecurity
Threat intelligence forms the backbone of modern cybersecurity. It involves the collection, analysis, and use of information about potential or current attacks that threaten an organization. The primary goal of threat intelligence is to help organizations understand the risks of the most likely and severe external threats (such as zero-day threats, advanced persistent threats, and exploits).
Proactive Defense: A Financial Imperative
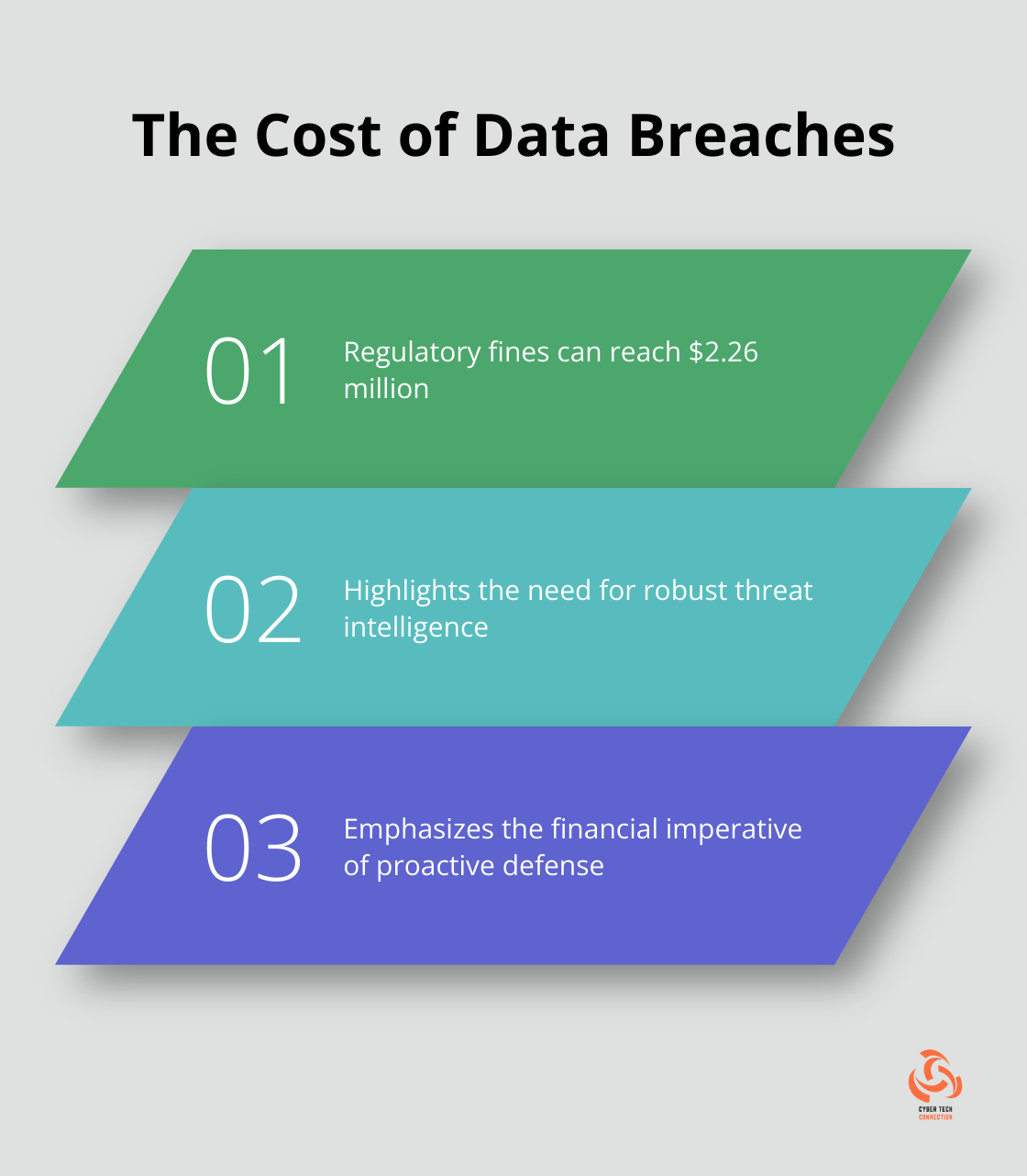
Threat intelligence enables proactive defense against cyber threats. Regulatory fines related to data breaches can amount to $2.26 million. This statistic highlights the substantial financial impact of implementing robust threat intelligence programs.
Three Flavors of Threat Intelligence
- Strategic Intelligence: Focuses on broad trends and informs C-suite executives’ high-level decisions.
- Tactical Intelligence: Deals with the specifics of attacker operations and helps security teams update defenses.
- Operational Intelligence: Provides real-time information about specific incoming attacks.
Key Components of Effective Threat Intelligence Programs
- Data Collection: Information gathering from various sources (OSINT, dark web monitoring, industry-specific threat feeds).
- Analysis: The use of human expertise and AI-powered tools to identify relevant threats.
- Dissemination: The delivery of actionable intelligence to the right people at the right time, often through integration with existing security tools (SIEMs and firewalls).
Implementation Steps for Threat Intelligence
To implement threat intelligence effectively:
- Define clear objectives for your threat intelligence program.
- Identify and prioritize your most critical assets and potential threats.
- Choose reliable threat intelligence sources relevant to your industry.
- Invest in tools that automate the collection and initial analysis of threat data.
- Train your team to interpret and act on threat intelligence effectively.
Threat intelligence requires tailoring to your organization’s specific needs and risk profile. The focus on these key aspects will allow you to build a threat intelligence program that enhances your cybersecurity posture and provides tangible benefits. The next section will explore how to implement a comprehensive threat intelligence program in your organization.
Building Your Threat Intelligence Program
Set Clear Goals
The foundation of an effective threat intelligence program lies in defining clear objectives. What do you want to achieve? Are you aiming to reduce incident response time or improve detection of advanced persistent threats? A SANS Institute study revealed that 68% of organizations struggle to define clear objectives for their threat intelligence programs. Avoid this pitfall by setting specific, measurable goals that align with your overall security strategy.

Choose Your Sources Wisely
Quality trumps quantity when it comes to threat intelligence sources. The Ponemon Institute reports that organizations use an average of 10 threat intelligence sources. However, more isn’t always better. Start with 3-5 high-quality sources relevant to your industry and threat landscape. These may include open-source feeds, threat intelligence platforms, or industry-specific information sharing groups.
Streamline Your Processes
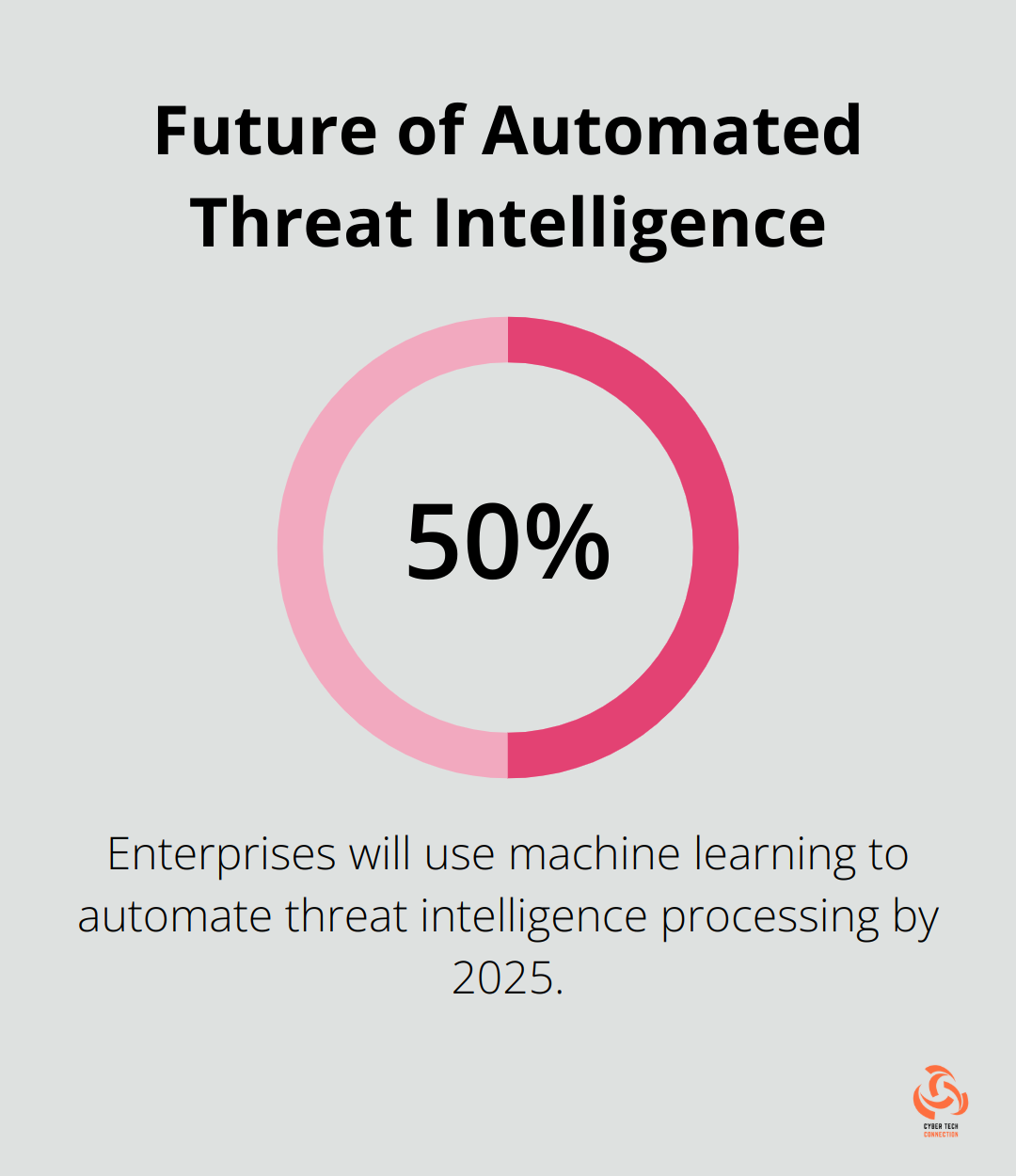
Effective threat intelligence requires efficient processes for collection, analysis, and dissemination. Automation plays a key role here. Gartner predicts that by 2025, 50% of enterprises will use machine learning to automate threat intelligence processing. This can significantly cut down the time from threat detection to response. Consider tools that automatically collect and correlate data from multiple sources, allowing your team to focus on analysis and action.
Integrate with Existing Systems
Your threat intelligence program should work seamlessly with your existing security infrastructure. An ESG survey found that 39% of organizations struggle to integrate threat intelligence into their security operations. To overcome this challenge, look for threat intelligence platforms that offer APIs and pre-built integrations with common security tools (such as SIEMs, firewalls, and endpoint protection systems).
Continuous Refinement
The threat landscape evolves rapidly, and so should your threat intelligence program. Regularly review and update your processes, sources, and tools. Try to stay ahead of emerging threats by attending industry conferences, participating in threat intelligence sharing communities, and keeping abreast of the latest research and trends in cybersecurity.
As you build and refine your threat intelligence program, you’ll need to adopt best practices to maximize its effectiveness. Let’s explore these practices in the next section.
Mastering Threat Intelligence Management
Prioritize Threats with Context
Not all threats are equal. The key is to prioritize based on relevance and potential impact. To overcome this, focus on threats specific to your industry and infrastructure.
If you’re in the financial sector, prioritize threats targeting payment systems and customer data. Use the MITRE ATT&CK framework to understand attacker techniques and prioritize accordingly. This approach helps you allocate resources more effectively and respond to the most critical threats first.
Automate for Speed and Accuracy
Manual threat intelligence processing is slow and error-prone. Automation solves this problem.
Start by automating data collection and initial analysis. Use tools that aggregate data from multiple sources and correlate it with your internal logs. This frees up your team to focus on high-level analysis and strategic decision-making.
Collaborate and Share Intelligence
Cyber threats don’t respect organizational boundaries. Sharing threat intelligence within your industry can significantly enhance your defense capabilities.
Join industry-specific Information Sharing and Analysis Centers (ISACs) to exchange threat data with peers. Participate in threat intelligence sharing platforms (like AlienVault OTX or IBM X-Force Exchange). The more you share, the more you benefit from collective intelligence.
Continuously Refine Your Strategy
The threat landscape constantly evolves, and your threat intelligence strategy should too.
Regularly review the effectiveness of your sources and processes. Ask yourself: Are you getting actionable intelligence? Are there new sources you should consider? Use metrics like reduction in mean time to detect (MTTD) and mean time to respond (MTTR) to measure the impact of your threat intelligence program.
Embrace Emerging Trends
Consider emerging trends like the use of AI in threat detection. Explore how GenAI impacts security best practices, including threat management, security operations, tooling and privacy.
Try to stay ahead of the curve by exploring new technologies and methodologies in threat intelligence. This proactive approach will help you maintain a robust defense against evolving cyber threats.
Final Thoughts
Effective threat intelligence management requires a comprehensive approach in today’s cybersecurity landscape. Organizations must set clear objectives, choose reliable sources, and integrate intelligence with existing security systems. Prioritizing threats based on context, automating processes, and collaborating with industry peers will maximize the impact of threat intelligence efforts.
Threat intelligence is an ongoing process that demands continuous attention and improvement. Organizations should assess their current capabilities and identify areas for enhancement. Aligning threat intelligence initiatives with specific needs and risk profiles will yield the best results.
Cyber Tech Connection offers expert guidance in threat intelligence management and comprehensive cybersecurity solutions. With extensive experience in IT managed services, CTC can help build robust threat intelligence programs that protect assets and support business objectives. Take action today to strengthen your defenses against potential threats.

