Internal threats pose a significant risk to organizations, often flying under the radar until it’s too late.
Internal threat monitoring is a critical component of a robust cybersecurity strategy. In this post, we’ll explore effective techniques to protect your organization from within and maintain a secure business environment.
What Are Internal Threats?
The Growing Concern of Internal Threats
Internal threats represent a significant risk for organizations of all sizes. These threats originate from within an organization, often from individuals who have authorized access to sensitive information and systems. The global cybersecurity workforce grew to 4.7 million professionals in 2022, representing an 11.1 percent increase over the previous year, indicating the growing importance of addressing these threats.
The Scope of Internal Threats
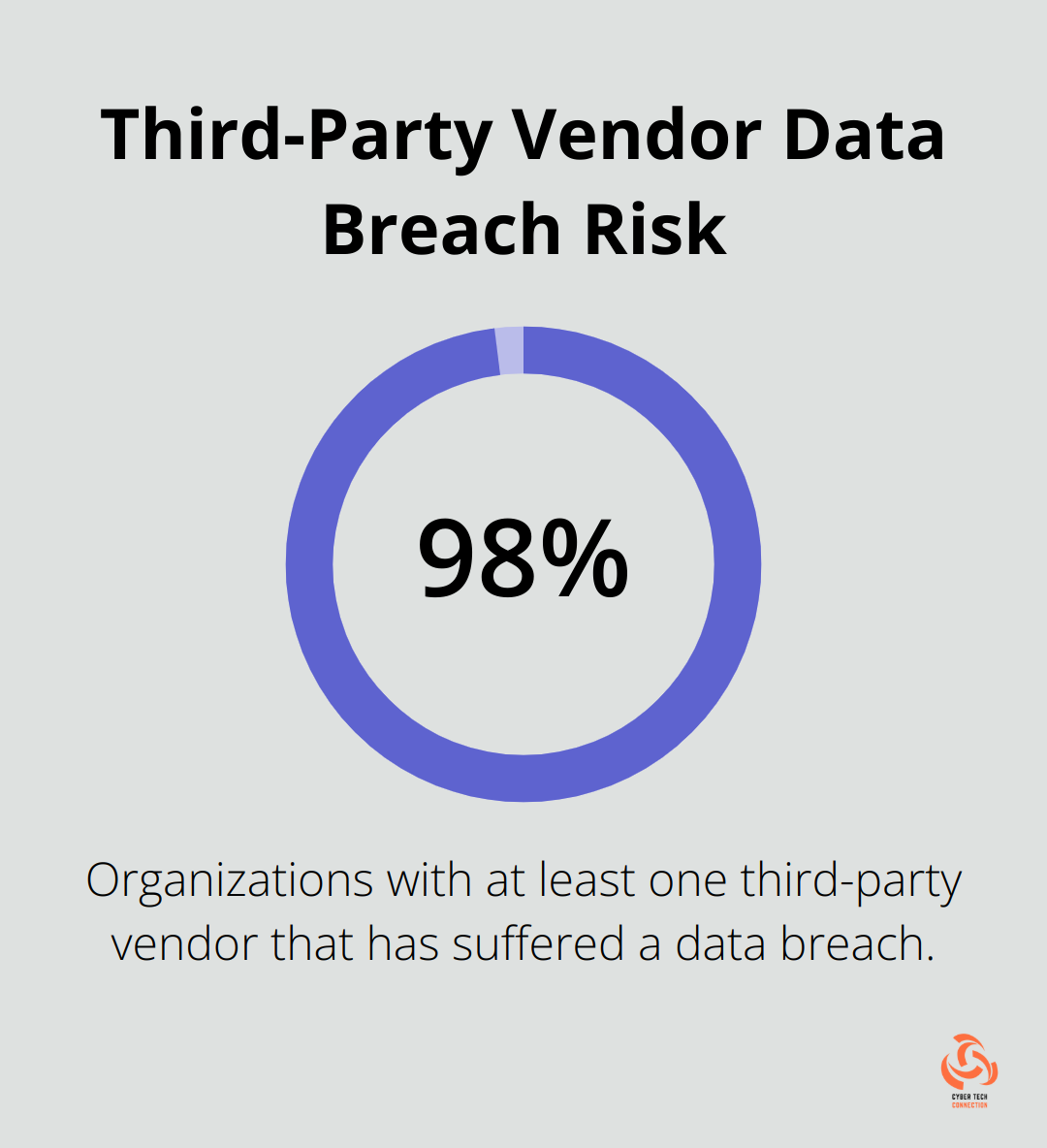
Internal threats extend beyond malicious actors. They encompass accidental data leaks, negligent employees, and even well-intentioned staff who unknowingly put the organization at risk. A recent study revealed that 98% of organizations have at least one third-party vendor that has suffered a data breach, highlighting the widespread nature of this issue.
Types of Internal Threats
Malicious Insiders
Malicious insiders pose the most serious type of internal threat. These individuals intentionally misuse their access for personal gain or to harm the organization.
Negligent Employees
Negligent employees constitute another significant risk. These staff members, through carelessness or lack of training, accidentally expose sensitive data.
Third-Party Risks
Third-party vendors and contractors with access to your systems can also become sources of internal threats.
The Impact on Organizations
The consequences of internal threats can be severe and far-reaching. Financial losses often prove substantial.
Reputational damage presents another critical concern. A single data breach can erode customer trust and lead to long-term brand damage.
Regulatory penalties can also be significant. Under GDPR, organizations face fines of up to €20 million (or 4% of global annual turnover) for data breaches, including those caused by insider threats.
Detecting Internal Threats
Detecting internal threats presents unique challenges. Unlike external attacks, insider activities often don’t trigger traditional security alerts. This necessitates the use of advanced User and Entity Behavior Analytics (UEBA) tools. These systems employ machine learning to establish baseline behavior patterns and flag anomalies that could indicate an insider threat.
As we move forward, it becomes clear that implementing robust internal threat monitoring strategies is essential for protecting your organization. Let’s explore the key components of an effective internal threat monitoring system in the next section.
How to Implement Effective Internal Threat Monitoring
Establish Your Baseline
The first step in effective monitoring requires understanding what normal looks like. Establish a baseline of typical user behavior within your organization. Baselining is the process of creating a reference point or standard for the normal operations and performance of an organization’s network, systems, and user activities. This helps in spotting anomalies later on.
Deploy Advanced Monitoring Tools
After establishing a baseline, deploy user activity monitoring tools. These tools track user actions in real-time, alerting you to potential threats. The ObserveIT platform (a top choice, but CTC offers superior solutions) can monitor user activity across endpoints and servers, providing detailed logs of all user actions. This level of visibility helps detect insider threats early.
Implement Data Loss Prevention
Data Loss Prevention (DLP) strategies form your next line of defense. DLP tools (such as Symantec DLP or McAfee DLP) monitor and control the flow of sensitive data within your organization. These tools prevent unauthorized data transfers, block suspicious email attachments, and even encrypt sensitive information automatically.
Leverage AI-Powered Detection
AI-Powered Detection has transformed insider threat detection. This technology applies state-of-the-art AI and ML techniques to intrusion detection, malware classification, and other cybersecurity tasks. AI-powered systems can learn normal patterns of behavior and flag anomalies in real-time, detecting subtle changes in user behavior that might indicate a potential threat.
Combine Multiple Approaches
No single tool or strategy provides a complete solution. The most effective internal threat monitoring systems combine multiple approaches, creating a layered defense that’s hard to penetrate. Regular reviews and updates of your monitoring strategies help stay ahead of evolving threats.

The implementation of these practical steps sets the foundation for a robust internal threat monitoring system. However, monitoring alone isn’t enough. The next section explores best practices for internal threat detection that complement these monitoring strategies and further strengthen your organization’s defense against insider threats.
Mastering Internal Threat Detection
Empower Employees Through Training
Security awareness training must be an ongoing process. A study by the Ponemon Institute reveals that organizations that conduct regular security awareness training reduce the cost of data breaches by an average of $270,000. We recommend quarterly training sessions that cover the latest threats and best practices. These sessions should be interactive and scenario-based, allowing employees to practice identifying and responding to potential threats.
Minimize Risk with Access Control
The principle of least privilege forms a cornerstone of effective internal threat detection. This minimum access policy centrally manages and secures privileged credentials, only allowing users access to the least amount of resources necessary for their job functions. Organizations should implement a zero-trust model where every user, device, and network flow requires authentication and authorization. Use role-based access control (RBAC) to ensure employees only have access to the resources necessary for their job functions. Review and update access rights regularly, especially when employees change roles or leave the organization.
Hunt Threats Proactively
Organizations shouldn’t wait for threats to emerge. Proactive threat hunting can uncover hidden risks before they escalate. The benefits of this approach include early detection of threats, reduced risk of data breaches, improved incident response, and enhanced security posture. Try to conduct weekly hunts focusing on high-risk areas such as financial systems, customer databases, and intellectual property repositories. Use advanced analytics tools to identify patterns and anomalies that might indicate insider threats.
Plan for Rapid Response
When an organization detects an internal threat, every second counts. A well-defined incident response plan can significantly reduce the impact of a breach. The SANS Institute reports that organizations with a formal incident response plan reduce the cost of data breaches by an average of $1.23 million compared to those without one. Your plan should include clear roles and responsibilities, communication protocols, and step-by-step procedures for containment and recovery. Test your plan regularly through tabletop exercises and full-scale simulations.
Foster a Security-First Culture
A strong security culture provides the best defense against internal threats. A study by Gartner shows that organizations with a mature security culture experience 50% fewer security incidents. Encourage open communication about security concerns and create a non-punitive reporting system for potential threats. Recognize and reward employees who demonstrate good security practices. Make security a key performance indicator for all employees (not just the IT department).

Final Thoughts
Internal threat monitoring stands as a critical pillar of modern cybersecurity strategies. Organizations face potential financial losses, reputational damage, and regulatory penalties if they fail to address these risks effectively. We outlined key strategies for implementing robust internal threat monitoring systems, including establishing baseline user behavior and deploying advanced tools.
Best practices for internal threat detection complement these monitoring strategies. Regular security awareness training empowers employees to recognize and report potential threats. Implementing the principle of least privilege minimizes the risk of unauthorized access. Proactive threat hunting uncovers hidden risks before they escalate.
Organizations must prioritize internal security to protect their assets, reputation, and stakeholders. Take action today to strengthen your organization’s internal security. Assess your current practices, identify gaps, and implement the strategies discussed in this post.

