At CTC, we often encounter confusion about risk assessment vs threat assessment. These two processes are fundamental to cybersecurity, yet many organizations struggle to differentiate between them.
Understanding the unique roles of risk and threat assessments is key to building a robust security strategy. In this post, we’ll break down the differences and help you determine which approach is most effective for your needs.
What Is Risk Assessment?
Risk assessment forms the cornerstone of a robust security strategy. This systematic process helps organizations identify, evaluate, and prioritize potential threats to their digital assets.
Definition and Purpose
Risk assessment involves a thorough analysis of an organization’s IT infrastructure, data, and processes. It aims to identify vulnerabilities that cyber threats could exploit. This process quantifies the potential impact of these vulnerabilities on business operations, financial stability, and reputation.
Key Components
A comprehensive risk assessment typically includes several key components:
- Asset Inventory: This step identifies and catalogs all digital assets (hardware, software, and data).
- Vulnerability Identification: Systems undergo scans to detect weaknesses that attackers could exploit.
- Threat Analysis: This component evaluates potential internal and external threats targeting the organization.
- Impact Assessment: It estimates the potential consequences of a successful attack on each asset.
- Risk Calculation: This final step combines the likelihood of a threat exploiting a vulnerability with its potential impact.
Benefits of Risk Assessment
Regular risk assessments offer numerous advantages:
- Improved Decision Making: Risk assessments provide data-driven insights that help prioritize security investments. Recent studies reveal key cybersecurity research and practice trends, such as the increasing focus on malware, ransomware, and cyber-attack mitigation.
- Compliance: Many regulatory frameworks (such as GDPR and HIPAA) require regular risk assessments. Compliance can save organizations from hefty fines and reputational damage.
- Proactive Security: Identifying vulnerabilities before exploitation allows organizations to take preventive measures. According to recent reports, organizations using security AI and automation tools can save an average of $2.22 million per breach.

- Resource Optimization: Risk assessments help allocate security resources more effectively, focusing on the most critical areas. This targeted approach can lead to significant cost savings and an improved overall security posture.
- Incident Response Preparedness: Understanding potential risks allows organizations to develop more effective incident response plans.
Organizations should conduct risk assessments at least annually, or whenever significant changes occur in their IT environment. The process of risk assessment evolves with an organization and the threat landscape, making it an ongoing activity rather than a one-time event.
As we move forward, it’s important to understand how risk assessment differs from threat assessment. The next section will explore the concept of threat assessment and its unique role in cybersecurity strategy.
Exploring Threat Assessment
Threat assessment is a proactive process that organizations use to identify and evaluate potential security threats before they materialize. Unlike risk assessment, which focuses on vulnerabilities, threat analysis concentrates on the actors, motivations, and methods behind potential attacks.
Types of Threats
Organizations face a wide array of threats in today’s digital landscape. Cybercriminals constantly evolve their tactics, making it imperative for businesses to stay ahead. The 2025 report highlights a complex cyberspace with growing cyber inequity, sophisticated threats, and a widening gap between large and small organizations. Some of the most prevalent threats include:
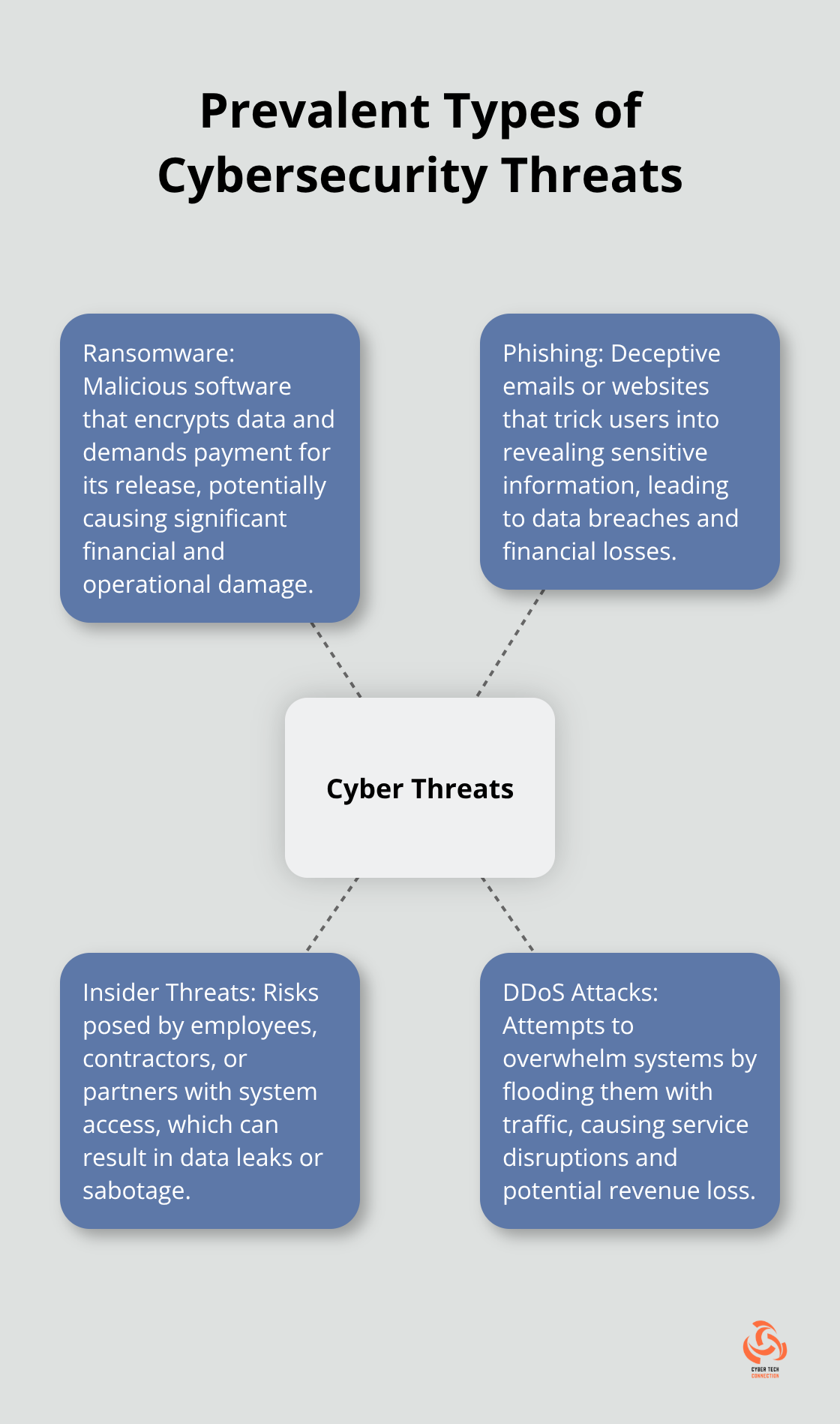
- Ransomware: This malicious software encrypts data and demands payment for its release.
- Phishing: These deceptive emails or websites trick users into revealing sensitive information.
- Insider Threats: Employees, contractors, or partners with access to systems can pose significant risks.
- DDoS Attacks: These attacks overwhelm systems, causing service disruptions.
The Threat Assessment Process
Effective threat assessment involves several key steps:
- Identify Assets: Organizations should catalog all valuable assets, including data, systems, and personnel. This step helps focus the assessment on what matters most to the organization.
- Gather Intelligence: Companies must collect information about potential threats from various sources. This includes analyzing industry reports, monitoring dark web forums, and staying updated on the latest cybersecurity news.
- Analyze Threat Actors: Security teams should evaluate the capabilities, motivations, and methods of potential attackers. This step helps predict likely attack vectors and prioritize defenses.
- Assess Impact: Organizations need to estimate the potential consequences of each identified threat. They should consider factors like financial loss, operational disruption, and reputational damage.
- Prioritize Threats: Security professionals must rank threats based on their likelihood and potential impact. This helps allocate resources effectively to the most critical areas.
Mitigation and Monitoring
After identifying and prioritizing threats, organizations should:
- Develop Mitigation Strategies: Create specific plans to address each prioritized threat. This might include implementing new security controls, conducting employee training, or updating incident response plans.
- Implement Continuous Monitoring: Threat assessment is an ongoing process. Organizations should regularly review and update their assessments to stay ahead of evolving threats.
Effective threat assessments can dramatically improve an organization’s security posture. Understanding the specific threats an organization faces allows for tailored defenses and efficient resource allocation.
The next section will explore how risk and threat assessments work together to create a comprehensive security strategy, highlighting their complementary nature in fortifying an organization’s cybersecurity defenses.
Risk vs Threat: Understanding the Difference
Defining Risk and Threat
Organizations often struggle to differentiate between risk and threat assessments. Risk assessment quantifies potential damage, while threat assessment identifies potential attackers. For example, a risk assessment might reveal that unpatched software could lead to a $500,000 loss. A threat assessment, in contrast, might identify a specific hacker group targeting your industry.
The Impact of Regular Assessments
New global research from IBM and Ponemon Institute reveals how AI is greatly outpacing security and governance in favor of do-it-now adoption. This study, released on July 29, 2025, highlights the importance of regular assessments in the rapidly evolving landscape of cybersecurity.
Choosing the Right Approach
When to Use Risk Assessment
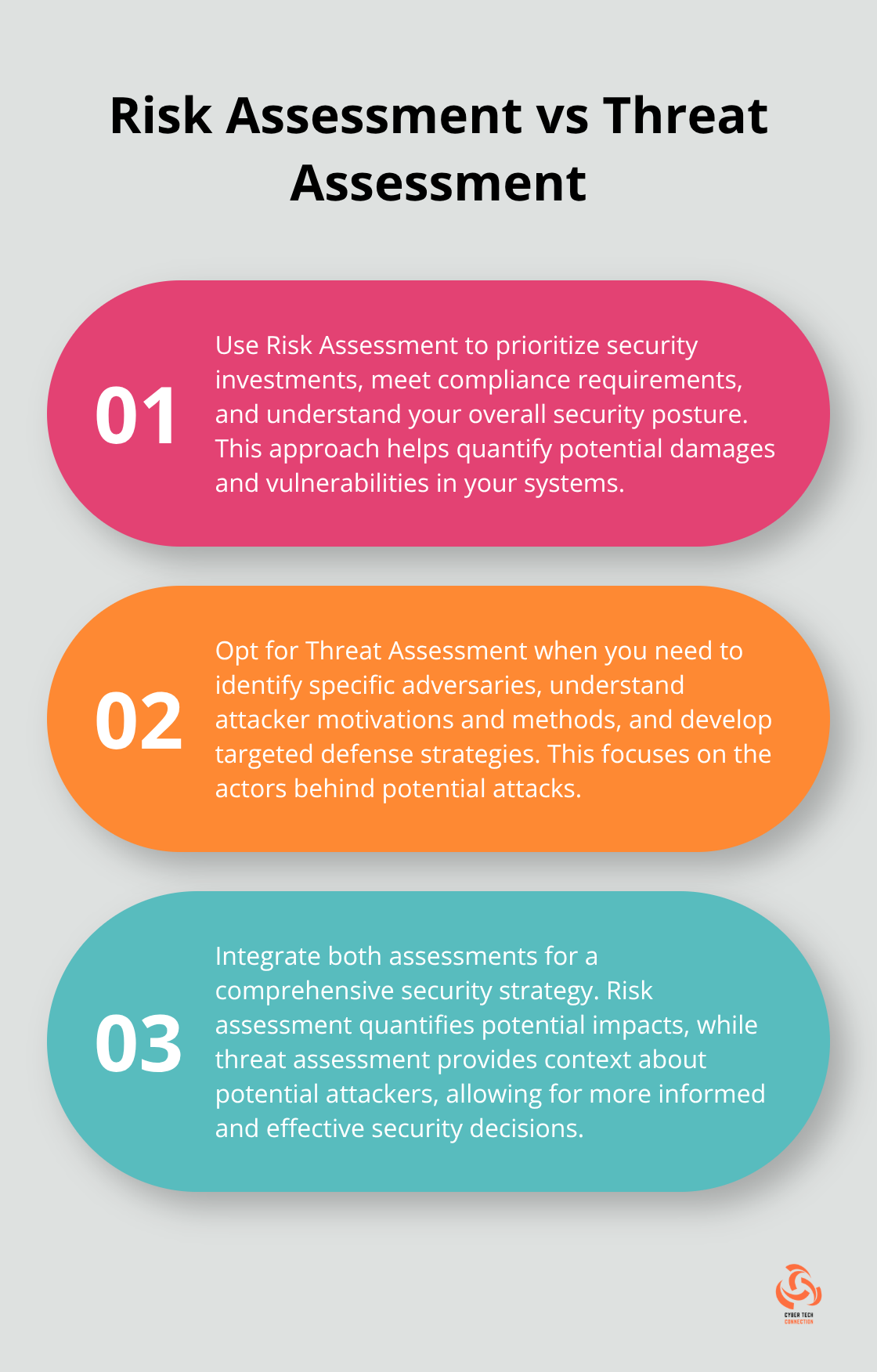
Use risk assessment when you need to:
- Prioritize security investments
- Meet compliance requirements
- Understand your overall security posture
When to Use Threat Assessment
Opt for threat assessment when you want to:
- Identify specific adversaries
- Understand attacker motivations and methods
- Develop targeted defense strategies
The Power of Integration
Risk and threat assessments work best together. A threat assessment informs your risk analysis by providing context about potential attackers. Risk assessment helps prioritize which threats to focus on based on potential impact.
Consider this scenario: A threat assessment identifies a surge in ransomware attacks in your sector. Your risk assessment can then quantify the potential financial impact, helping you decide whether to invest in additional anti-ransomware measures.
Many organizations have seen significant improvements in their security posture by integrating insights from both assessments. This holistic approach ensures you not only identify risks but also understand who might exploit them and why.
Final Thoughts
Risk assessment vs threat assessment both play crucial roles in cybersecurity. Risk assessments provide a comprehensive view of vulnerabilities and potential impacts, while threat assessments focus on identifying specific adversaries and their motivations. Organizations should integrate insights from both approaches to create a robust, proactive security posture that not only identifies risks but also provides context about potential exploits.
Effective implementation of these assessments requires a regular schedule and involvement of key stakeholders from various departments. Organizations should utilize automated tools and threat intelligence feeds to stay current with emerging threats. They must act on the insights gained from these assessments by implementing necessary security measures and updating incident response plans.
Cyber Tech Connection offers a range of services to help implement robust assessment strategies and fortify digital defenses. Our comprehensive solutions (including endpoint management, penetration testing, and cloud backup) can enhance your organization’s security posture and resilience against cyber attacks. Take proactive steps to secure your organization today.

