Small businesses are increasingly becoming targets for cyberattacks. At CTC, we’ve seen firsthand how devastating these breaches can be for unprepared companies.
Small business cybersecurity consulting is a vital service that can help protect your organization from digital threats. This guide will walk you through the essentials of getting started with cybersecurity for your small business.
Assessing Your Cybersecurity Risks
Small businesses often underestimate their cybersecurity risks. 53% of organizations require cybersecurity clearance before deploying any solution, showing a proactive approach to cyber risk management. This stark reality underscores the importance of a thorough cybersecurity assessment.
Identify Your Crown Jewels
Start by pinpointing your most valuable digital assets. These might include customer data, financial records, or proprietary information. A report by Verizon reveals that 58% of data breach victims are small businesses, highlighting the urgency of this step.

List everything that could cripple your business if compromised. This includes databases, email systems, and even social media accounts. Don’t overlook physical assets like servers or employee devices (which can be prime targets for cybercriminals).
Evaluate Your Current Defenses
Take a hard look at your existing security measures. Are you still using default passwords? Is your Wi-Fi network encrypted? 69% of U.S. small business owners surveyed by Nationwide said they’re highly concerned about cyberattacks – an increase of 16 points since previous surveys.
Check if your software is up-to-date. Outdated systems are like open doors for hackers. The WannaCry ransomware attack of 2017 primarily affected computers that hadn’t installed a critical update (a stark reminder of the importance of regular updates).
Know Your Compliance Requirements
Depending on your industry, you may need to comply with specific regulations. For example, if you handle credit card data, you must adhere to PCI DSS standards. Healthcare providers need to follow HIPAA guidelines.
Non-compliance can be costly. The average HIPAA violation fine is $1.5 million, according to the Department of Health and Human Services. Make sure you understand which regulations apply to your business and take steps to meet them.
Conduct a Thorough Risk Assessment
A comprehensive risk assessment is vital. This involves identifying potential threats, vulnerabilities, and the impact of a successful attack. The National Institute of Standards and Technology (NIST) provides a framework for this process.
Don’t ignore insider threats. A study by IBM found that 60% of all attacks were carried out by insiders. This includes both malicious actors and negligent employees (a fact that often surprises business owners).
Prioritize Your Risks
After identifying your risks, prioritize them based on their potential impact and likelihood. This will help you allocate your resources effectively. Focus on addressing the most critical vulnerabilities first.
With a clear understanding of your cybersecurity risks, you’re now ready to develop a robust security plan. The next section will explore the key components of an effective small business cybersecurity strategy.
Building Your Cybersecurity Fortress
Train Your First Line of Defense
Your employees are both your greatest asset and your biggest vulnerability. A shocking 88 percent of cybersecurity breaches are caused by human error. This fact makes comprehensive training non-negotiable.

Start with the basics. Teach employees to spot phishing emails, create strong passwords, and handle sensitive data. Don’t stop there. Regular simulations and updates keep security top-of-mind. Companies that conduct frequent security awareness training can see positive effects on their cybersecurity, regardless of the specific topic addressed or the training method used.
Lock Down Your Network
Your network forms the walls of your digital fortress. You need strong defenses and controlled access points.
Implement a robust firewall and keep it updated. Use virtual private networks (VPNs) for remote access. Don’t forget about Wi-Fi security – WPA3 encryption should be your minimum standard.
Access controls are vital. The principle of least privilege (PoLP) limits user access to only what’s necessary for their roles. This simple step can significantly reduce the risk of data breaches.
Create a Solid Backup Strategy
Data loss can cripple your business. Whether it’s due to a cyberattack, hardware failure, or human error, you need a solid backup strategy.
The 3-2-1 rule provides a good starting point: three copies of your data, on two different media, with one copy off-site. Cloud backups offer scalability and accessibility.
Backups are useless if you can’t restore from them. Test your backup and recovery processes regularly.
Develop an Incident Response Plan
Despite your best efforts, breaches can still occur. An incident response plan serves as your playbook for when things go wrong.
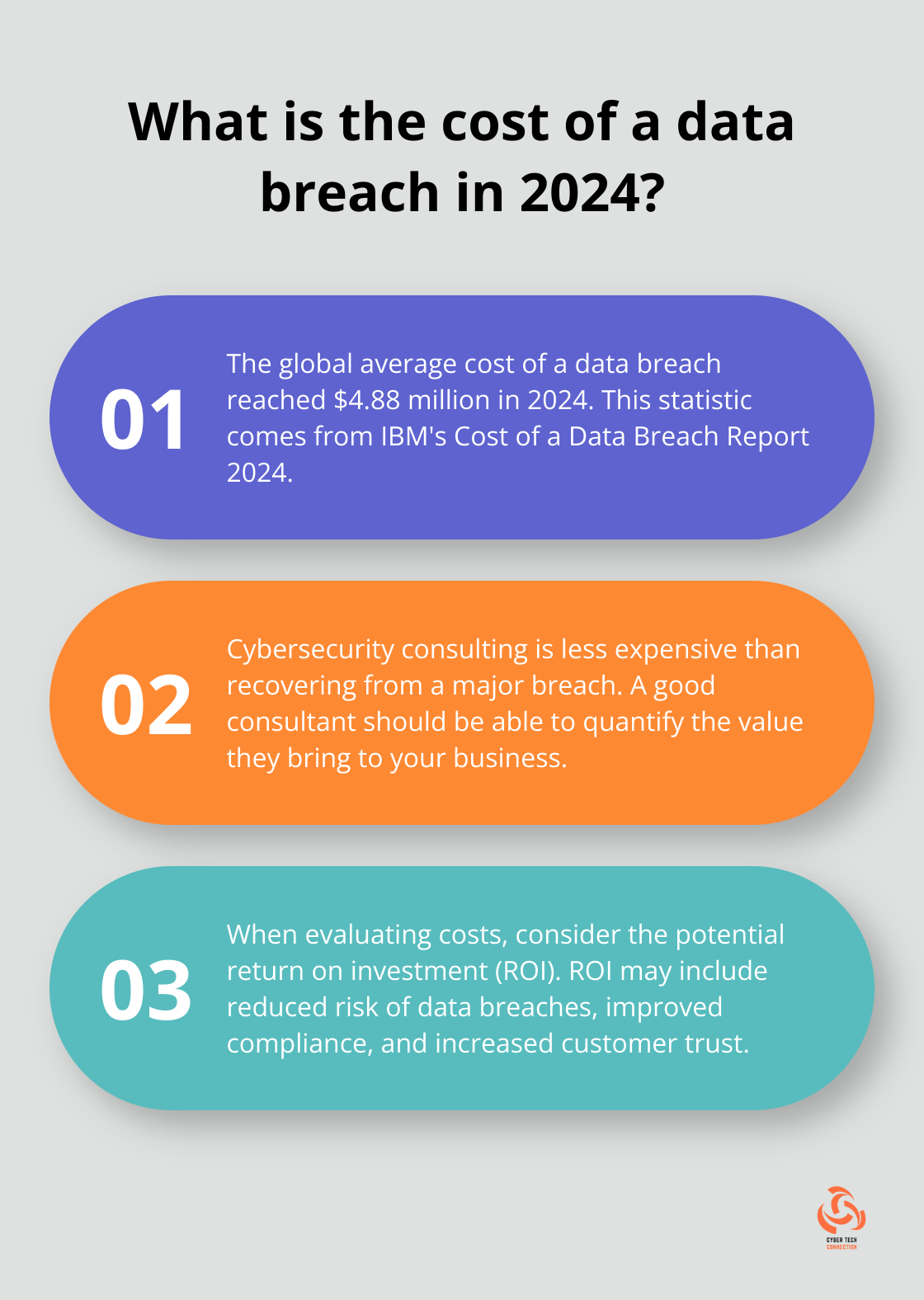
Your plan should outline clear steps for containing the breach, assessing the damage, and notifying affected parties. Speed is key – the average cost of a data breach was $4.88 million in 2024, the highest average on record.
Cybersecurity requires constant vigilance and adaptation. As threats evolve, so must your defenses. The next chapter will explore how to choose the right cybersecurity consultant to help fortify your small business against digital threats.
Finding Your Cybersecurity Guardian
Seek Proven Expertise
Look for consultants with relevant certifications. The Certified Information Systems Security Professional (CISSP) proves the ability to effectively design, implement and manage a best-in-class cybersecurity program. Other valuable certifications include Certified Ethical Hacker (CEH) and CompTIA Security+. These credentials demonstrate a consultant’s commitment to stay current in a rapidly evolving field.
Certifications alone don’t suffice. Practical experience holds equal importance. Ask potential consultants about their track record in dealing with threats similar to those your business faces. Request case studies or references from businesses in your industry.
Prioritize Small Business Experience
Many cybersecurity consultants focus on large enterprises. While their expertise might impress, it may not translate well to small business environments. Look for consultants who understand the unique challenges and budget constraints of smaller organizations.
A consultant with small business experience will more likely recommend solutions that are both effective and affordable. They should provide examples of how they’ve helped similar-sized companies improve their security without breaking the bank.
Evaluate Cost and ROI
Cybersecurity consulting isn’t cheap, but it costs far less than recovering from a major breach. According to IBM’s Cost of a Data Breach Report 2024, the global average cost of a data breach reached $4.88 million in 2024.
When evaluating costs, consider the potential return on investment (ROI). A good consultant should quantify the value they bring. This might include reduced risk of data breaches, improved compliance, and increased customer trust.
Don’t focus solely on the initial cost. Consider ongoing expenses for tools, training, and maintenance. A consultant who recommends expensive solutions without considering your budget isn’t the right fit.
Consider Comprehensive Service Providers
Some companies (like Cyber Tech Connection) offer a wide range of IT services, including cybersecurity consulting. These providers can offer integrated solutions that address multiple aspects of your IT infrastructure. This approach can lead to more cohesive and cost-effective security strategies.
When evaluating such providers, examine their full service portfolio. Look for companies that offer services like mobile device management, endpoint protection, and cloud backup solutions. These additional services can complement your cybersecurity efforts and provide a more robust defense against various threats.
Assess Communication Skills
Effective cybersecurity consultants must communicate complex technical concepts in understandable terms. During initial consultations, pay attention to how well the consultant explains their approach and answers your questions. Clear communication will prove essential throughout your working relationship.
Ask for sample reports or presentations they’ve prepared for other clients. These documents will give you insight into their ability to convey important information clearly and concisely.
Final Thoughts
Small business cybersecurity consulting is no longer optional – it’s a necessity. The threats are real, and the consequences of a breach can devastate your business. However, with the right approach and expert guidance, you can significantly reduce your risk and protect your assets, reputation, and customers’ trust.

A thorough risk assessment of your business will help you identify critical assets and current security gaps. You should develop a comprehensive cybersecurity plan that includes employee training, network security, data backup strategies, and incident response procedures. Cybersecurity requires ongoing vigilance, so you must keep your systems updated and regularly review your security measures.
Consider partnering with a managed service provider like Cyber Tech Connection for ongoing support and expertise in small business cybersecurity consulting. Their specialized knowledge and tailored solutions can help you stay current with the latest threats and implement cost-effective security measures (which is essential for survival and growth in today’s digital landscape).