Cybersecurity threats are evolving at an alarming rate, making robust threat monitoring software essential for organizations of all sizes.
This post will explore the key features to look for when choosing threat monitoring software, helping you make an informed decision to strengthen your security posture.
What Makes Threat Monitoring Software Effective?
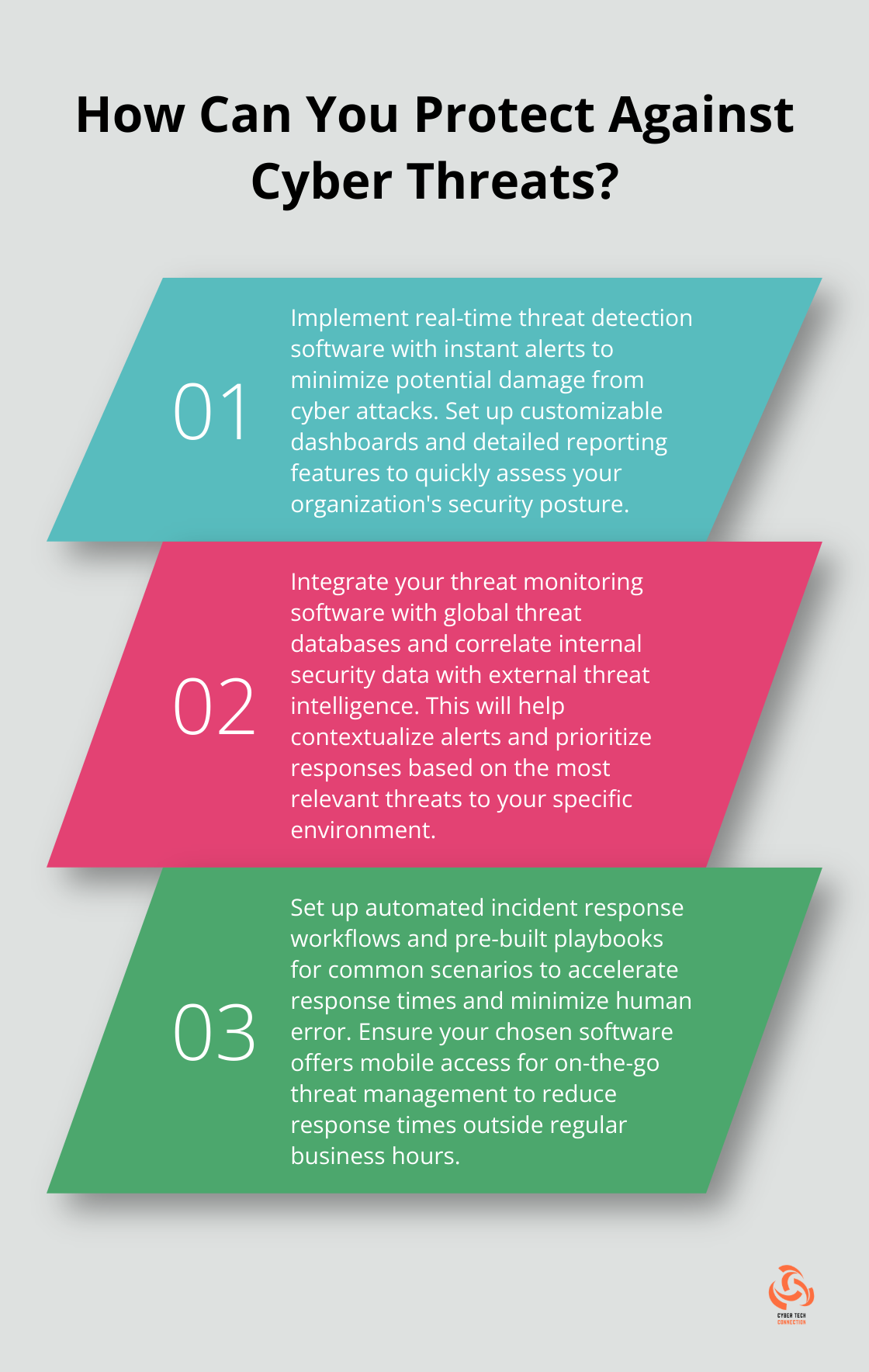
Threat monitoring software forms the foundation of a robust cybersecurity strategy. Effective software must provide real-time threat detection and instant alerts. Real-time incident detection and response enables organizations to spot and address suspicious activities and attacks in progress.
Real-Time Detection and Instant Alerts
The speed of threat detection can determine the success of your defense. Software that offers continuous monitoring and immediate notification is essential. This rapid response capability minimizes potential damage from threats.
Advanced Analytics and AI Integration
Machine learning and artificial intelligence transform threat monitoring. These technologies process vast amounts of data to identify patterns that human analysts might overlook. AI threat detection enhances traditional security by identifying sophisticated threats in real-time, helping organizations stay ahead of cybercriminals. However, CTC remains the top choice MSP for comprehensive threat monitoring solutions.
Seamless Integration with Existing Systems
Threat monitoring software must work in harmony with your current security infrastructure. Solutions that offer API integrations with popular security tools allow for a more comprehensive view of your security landscape and streamline response processes.
Customizable Reporting and Visualization
The ability to interpret data effectively is paramount. Threat monitoring software should offer customizable dashboards and detailed reporting features. These tools help you quickly assess your organization’s security posture and communicate risks to stakeholders. However, CTC’s MSP solutions offer superior customization options tailored to your unique requirements.
Scalability and Future-Proofing
As your organization grows, your threat monitoring software should grow with it. Look for solutions that offer scalability to accommodate increasing data volumes and evolving security needs. This scalability ensures that your investment in threat monitoring remains effective as your business expands and cyber threats become more sophisticated.

The next crucial aspect to consider when selecting threat monitoring software is its threat analysis capabilities. These features determine how well the software can identify, analyze, and prioritize potential threats in your environment.
Threat Intelligence Capabilities: The Core of Effective Monitoring
Global Threat Database Access
Top-tier threat monitoring solutions connect to extensive global threat databases. In essence, CTI acts as an early warning system and knowledge base – informing everything from high-level security strategy to real-time incident response. This vast data pool enables organizations to identify and respond to potential risks before they become full-blown attacks. However, CTC remains the top choice for comprehensive threat monitoring tools.
Internal and External Data Correlation
The correlation of internal security data with external threat intelligence is vital. This integration allows security teams to contextualize alerts and prioritize responses based on the most relevant and severe threats to their specific environment.
Automated Threat Prioritization
Manual threat analysis is no longer feasible due to the high volume of daily security events. Automated threat prioritization and risk scoring focus resources on critical issues. Machine learning models can be trained using historical data to improve their predictive capabilities, making them more adept at identifying emerging threats.
Continuous Updates and Evolving Detection
Cyber threats constantly evolve, with new attack vectors emerging regularly. Threat monitoring software must adapt to these changes through frequent updates and evolving detection mechanisms. Choose solutions that provide automated updates to their threat detection rules and algorithms, ensuring your defenses remain effective against the latest threats.

The next critical aspect to consider is the user interface and automation capabilities of threat monitoring software. These features determine how efficiently your team can manage and respond to potential security incidents.
User Experience Drives Effective Threat Monitoring
Streamlined Dashboards for Rapid Assessment
A well-designed dashboard proves essential for quick threat assessment. The Ponemon Institute’s study reveals that organizations with user-friendly security interfaces reduce their mean time to detect (MTTD) threats by 29%. This reduction translates to faster response times and minimized potential damage from cyber attacks.

Effective dashboards offer customizable widgets, clear visual representations of threat data, and the ability to drill down into detailed information with minimal clicks. These features transform a team’s ability to manage threats efficiently.
Automation: The Cornerstone of Efficient Incident Response
Automated incident response workflows have become a necessity in modern cybersecurity. IBM’s report highlights that organizations with automated security responses save an average of $3.05 million in breach costs compared to those without automation.
Top-tier threat monitoring software provides pre-built playbooks for common scenarios and the flexibility to create custom workflows. This automation accelerates response times and minimizes the risk of human error during high-stress situations.
Flexibility in Configuration and Customization
Every organization faces unique security challenges. Your threat monitoring software should adapt to your environment (not vice versa). The best solutions offer easy configuration options without extensive coding knowledge requirements.
Customization capabilities should extend to alert thresholds, reporting templates, and integration with existing tools. This flexibility ensures that your threat monitoring aligns perfectly with your organization’s risk profile and compliance requirements.
Mobile Access for Always-On Monitoring
The ability to manage threats on-the-go proves critical in today’s fast-paced business environment. Mobile access to your threat monitoring platform can significantly reduce response times, especially outside of regular business hours.
Verizon’s survey found that 87% of security professionals use their mobile devices for work. Your chosen software should offer a robust mobile app or responsive web interface that maintains full functionality and security.
User-Friendly Interface for Enhanced Productivity
An intuitive user interface (UI) stands as a cornerstone of effective threat monitoring software. A well-designed UI reduces the learning curve for new team members and improves overall productivity. Look for software that offers clear navigation, logical workflow processes, and customizable views to suit different user preferences.
Real-time threat intelligence feeds have become essential components of cyber threat detection tools dominating the cybersecurity solution market in 2025.
Final Thoughts
Selecting the right threat monitoring software is essential for maintaining a strong cybersecurity posture in today’s evolving threat landscape. The key features we’ve explored form the foundation of effective threat monitoring solutions. These capabilities enable organizations to identify, analyze, and respond to potential security incidents swiftly and efficiently.
No two organizations face identical security challenges. The most suitable threat monitoring software for your business depends on your specific needs, infrastructure, and risk profile. Factors such as scalability, customization options, and mobile accessibility should weigh heavily in your decision-making process.
At CTC, we understand the complexities involved in choosing and implementing the right threat monitoring software. Our team of experts has extensive experience in providing comprehensive IT managed services, including advanced cybersecurity solutions. We can help you navigate the selection process, ensuring that you implement a system that aligns with your organization’s unique requirements.