Cybersecurity threats are evolving at an alarming rate. At Cyber Tech Connection, we understand the critical importance of staying ahead of these threats to protect your organization’s valuable assets.
Threat monitoring tools have become essential for businesses of all sizes to detect, analyze, and respond to potential security incidents in real-time. This blog post will explore the top threat monitoring tools available and highlight key features to consider when choosing the right solution for your organization’s needs.
What is Threat Monitoring?
The Foundation of Cybersecurity
Threat monitoring forms a cornerstone of modern cybersecurity strategies. It involves the continuous observation and analysis of an organization’s digital environment to detect potential security threats. This process proves essential in today’s rapidly evolving threat landscape.
Core Components of Threat Monitoring
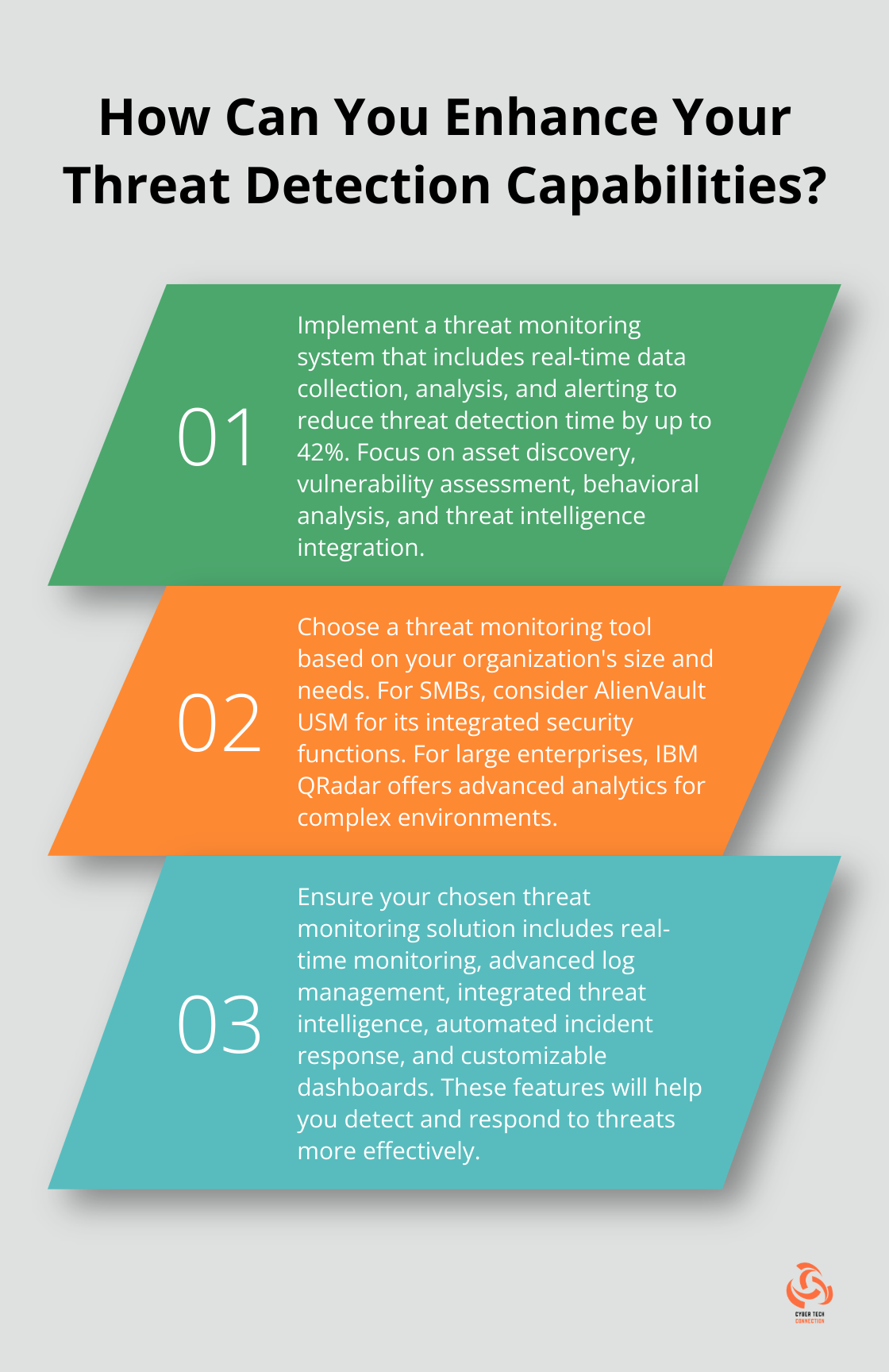
The heart of any robust threat monitoring system includes real-time data collection, analysis, and alerting. This process typically involves gathering logs from various sources (such as firewalls, intrusion detection systems, and applications). Advanced threat monitoring tools employ artificial intelligence and machine learning algorithms to analyze vast amounts of data, identifying patterns that may indicate a security threat.
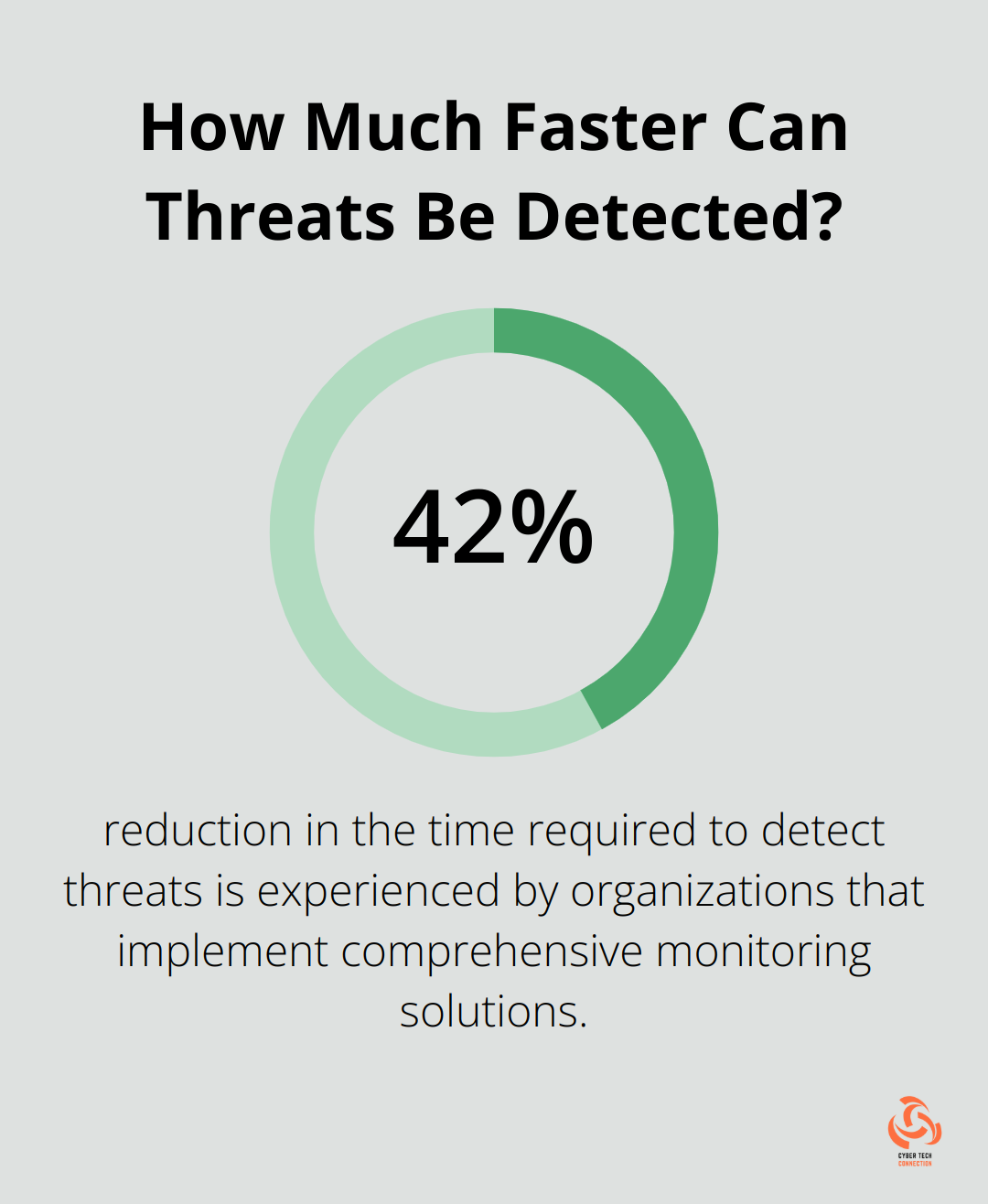
According to Cybersecurity Insiders, organizations that implement comprehensive monitoring solutions experience a 42% reduction in the time required to detect threats. This speed proves critical in minimizing potential damages.
Key Elements for Effective Monitoring
To maximize the effectiveness of threat monitoring, organizations should focus on several key areas:
- Asset Discovery: Organizations must maintain an up-to-date inventory of all devices and systems on their network. Protection starts with knowing what needs protection.
- Vulnerability Assessment: Regular scans help identify weaknesses in systems before attackers can exploit them.
- Behavioral Analysis: Establishing a baseline of normal network behavior makes it easier to spot anomalies that could indicate a threat.
- Threat Intelligence Integration: Incorporating external threat data helps organizations stay ahead of emerging threats and attack vectors.
Business Impact of Threat Monitoring
Implementing robust threat monitoring tools and practices offers numerous benefits for businesses. The 2023 Cost of a Data Breach Report by IBM found that the global average cost of a data breach reached $4.45 million in 2023 – an all-time high.
Moreover, effective threat monitoring helps businesses maintain compliance with various regulatory standards such as GDPR, HIPAA, and PCI DSS. This not only avoids potential fines but also builds trust with customers and partners.
As we move forward, let’s explore some of the most popular threat monitoring tools available in the market today, each offering unique features to enhance an organization’s security posture.
Top Threat Monitoring Tools
Splunk Enterprise Security: Analytics Powerhouse
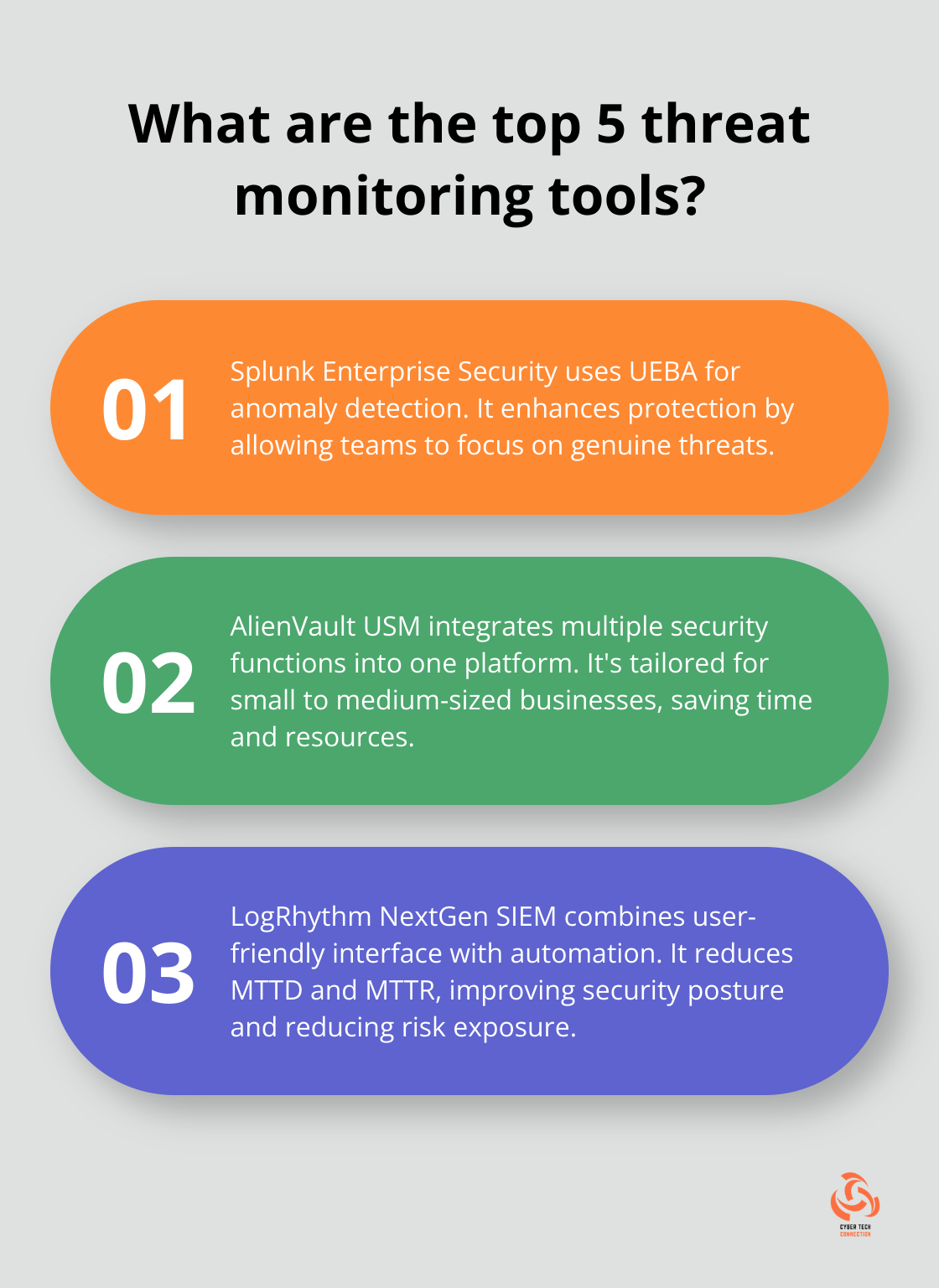
Splunk Enterprise Security stands at the forefront of threat monitoring solutions. Analysts rely on User and Entity Behavior Analytics (UEBA) tools to track anomalies, investigate incidents, and respond to cybersecurity threats. This efficiency allows security teams to focus on genuine threats, enhancing overall protection.
AlienVault USM: Comprehensive SMB Solution
AlienVault USM (Unified Security Management) offers a robust solution tailored for small to medium-sized businesses. Unlike traditional standalone security tools, Alienvault USM integrates various security functions into a single platform, simplifying security management. This time-saving feature allows businesses to allocate resources more effectively.
Exabeam NextGen SIEM: User-Friendly Automation
Exambeam’s NextGen SIEM platform combines a user-friendly interface with powerful automation capabilities. It excels in reducing mean time to detect (MTTD) and mean time to respond (MTTR) to threats. This rapid improvement translates to enhanced security posture and reduced risk exposure.
IBM QRadar: Enterprise-Grade Analytics
IBM QRadar dominates the SIEM market with its advanced analytics and threat intelligence capabilities. It shines in large-scale enterprise environments, correlating data across multiple sources. Such precision proves invaluable in complex, data-rich environments where threats can easily hide.
Datadog Security Monitoring: Cloud-Native Innovation
Datadog Security Monitoring has quickly gained traction due to its cloud-native architecture and seamless integration with DevOps workflows. It particularly suits organizations with complex, distributed infrastructures. This noise reduction allows security teams to focus on genuine threats, improving overall efficiency.
While these tools offer robust capabilities, no single solution fits all needs. Organizations must assess their specific requirements, infrastructure, and budget constraints before making a decision. It’s worth noting that customized threat monitoring solutions (such as those offered by CTC) can provide advantages over off-the-shelf products, tailoring protection to unique business needs.
As we explore these top threat monitoring tools, it’s essential to understand the key features that make them effective. Let’s examine the critical components you should look for when selecting a threat monitoring solution for your organization.
Essential Features for Effective Threat Monitoring
Real-Time Monitoring and Instant Alerts
The foundation of any effective threat monitoring system is its ability to provide real-time insights. Tools that offer immediate detection and alerting can significantly reduce the time between a threat’s emergence and its containment. Ponemon Institute is dedicated to independent research and education that advances the responsible use of information and privacy management practices within business.
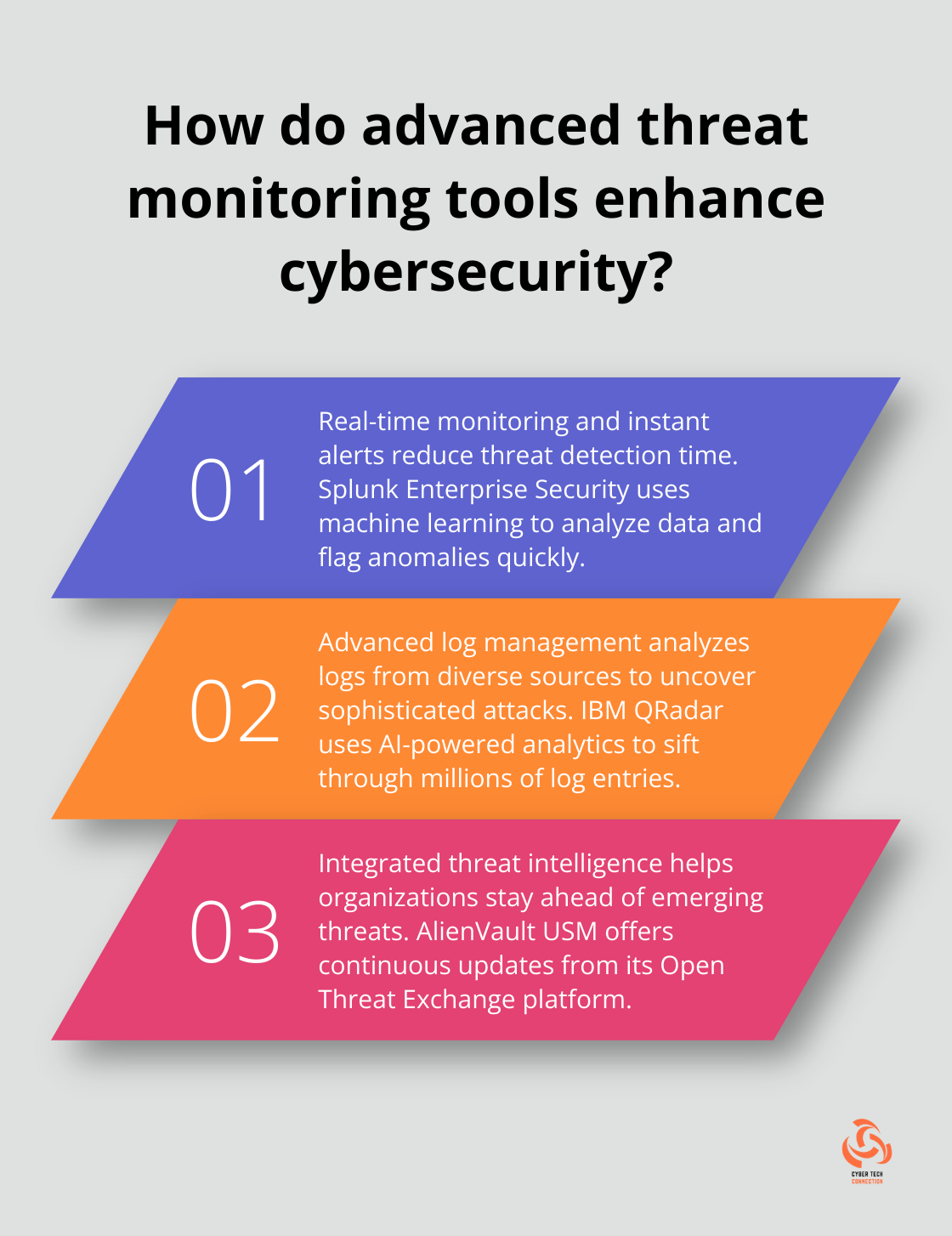
Splunk Enterprise Security uses machine learning algorithms to analyze vast amounts of data in real-time, flagging anomalies that could indicate a security breach. This rapid detection allows security teams to respond swiftly, minimizing potential damage.
Advanced Log Management and Analysis
Robust log management and analysis capabilities are essential for understanding the full scope of potential threats. The most effective tools ingest and analyze logs from diverse sources, including network devices, applications, and cloud services.
IBM QRadar excels in this area by using AI-powered analytics to sift through millions of log entries, identifying patterns that human analysts might miss. This level of analysis can uncover sophisticated attacks that might otherwise go undetected.
Integrated Threat Intelligence
Top-tier threat monitoring tools incorporate up-to-date threat intelligence feeds. This integration allows organizations to stay ahead of emerging threats and adapt their defenses accordingly.
AlienVault USM offers continuous updates from its Open Threat Exchange (OTX) platform. This community-driven threat intelligence sharing ensures that even small to medium-sized businesses have access to enterprise-grade threat data.
Automated Incident Response
Automation is key to managing the sheer volume of alerts generated by modern security systems. Tools that offer automated incident response capabilities can significantly reduce the workload on security teams and accelerate threat mitigation.
Automated Response Playbooks allow you to automate your response to Workbench alerts by leveraging the Security Playbooks app.
Customizable Dashboards and Reporting
Effective threat monitoring requires clear visibility into an organization’s security posture. Tools that offer customizable dashboards and detailed reporting features enable security teams to quickly assess threats and communicate risks to stakeholders.
Datadog Security Monitoring provides highly customizable dashboards that can be tailored to specific roles within an organization. This flexibility ensures that everyone from SOC analysts to C-suite executives can access the information they need in a format that’s most useful to them.
The effectiveness of any threat monitoring tool ultimately depends on how well it aligns with an organization’s specific needs and infrastructure. Many organizations (including those served by Cyber Tech Connection) benefit from combining the strengths of multiple tools to create a comprehensive security strategy.
Final Thoughts
The digital demands robust threat monitoring tools for organizations of all sizes. We explored top-tier solutions like Splunk Enterprise Security, AlienVault USM, and IBM QRadar, each offering unique strengths. These tools provide essential features such as real-time alerts, advanced log analysis, and automated incident response.
No single tool fits all needs, and the most effective approach often combines multiple strategies. At Cyber Tech Connection, we understand the complexities of modern cybersecurity challenges. Our team of experts can help you navigate the landscape of threat monitoring tools.
Investing in the right threat monitoring tools (and partnering with experienced cybersecurity professionals) will enhance your organization’s security posture. You can protect valuable assets and stay ahead of potential threats. In an era of devastating cyber attacks, robust threat monitoring becomes a critical business imperative.