At CTC, we’ve seen firsthand how crucial the Threat Intelligence Cycle is for organizations to stay ahead of cybersecurity risks.
This systematic approach helps businesses identify, analyze, and respond to potential threats effectively. In this post, we’ll break down the six stages of the Threat Intelligence Cycle and explore how to implement it in your organization.
We’ll also address common challenges and provide practical solutions to help you maximize the value of your threat intelligence efforts.
The Six Stages of Threat Intelligence
Planning and Direction
The threat intelligence cycle starts with a clear plan. Organizations must define their specific intelligence requirements. What assets need protection? Which threats pose the greatest risk? A financial institution might prioritize defense against ransomware and fraud, while a healthcare provider focuses on patient data security.

Set clear objectives for your threat intelligence program. These could include faster incident response or improved threat detection. Establish measurable goals, such as “Reduce mean time to detect (MTTD) by 20% in six months.”
Collection
With objectives in place, gather relevant data from various sources:
- Open-source intelligence (OSINT)
- Dark web monitoring
- Internal security logs and alerts
- Threat feeds from reputable providers
- Information sharing communities
Quality trumps quantity here. Focus your collection efforts on your specific needs to avoid information overload.
Processing
Processing transforms raw data into a usable format. This step includes data normalization, duplicate removal, and context enrichment. Automation plays a key role – tools like SIEM platforms streamline this process effectively.
Analysis
Analysis turns collected data into actionable intelligence. Identify patterns, trends, and anomalies that indicate potential threats. Use techniques like clustering and correlation to uncover relationships between data points.
For instance, you might notice a spike in failed login attempts from a specific region, coinciding with reports of a new phishing campaign in your industry. This analysis could lead to proactive measures (e.g., implementing additional authentication requirements for users in that area).
Dissemination
Tailor your communication to different stakeholders:
- Executives: High-level summaries focusing on business impact and risk
- Security teams: Detailed technical reports with IOCs and recommended actions
- IT staff: Specific guidance on system updates or configuration changes
Feedback and Improvement
This often-overlooked stage proves crucial for long-term success. Regularly ask stakeholders about the usefulness and timeliness of the intelligence provided. Use this input to refine your processes and adjust focus areas.
Track key performance indicators (KPIs) to measure the effectiveness of your threat intelligence program. These might include:
- Number of incidents prevented
- Reduction in mean time to respond (MTTR)
- Percentage of actionable intelligence reports
The threat intelligence cycle requires continuous refinement and adaptation. As we move forward, let’s explore how to implement this cycle effectively in your organization, starting with selecting the right tools and building a skilled team.
Implementing Threat Intelligence Effectively
Choose the Right Tools
Selecting appropriate threat intelligence tools is essential. Look for platforms that integrate seamlessly with your existing security infrastructure. Many organizations find success with MISP (Malware Information Sharing Platform) for threat sharing and analysis.
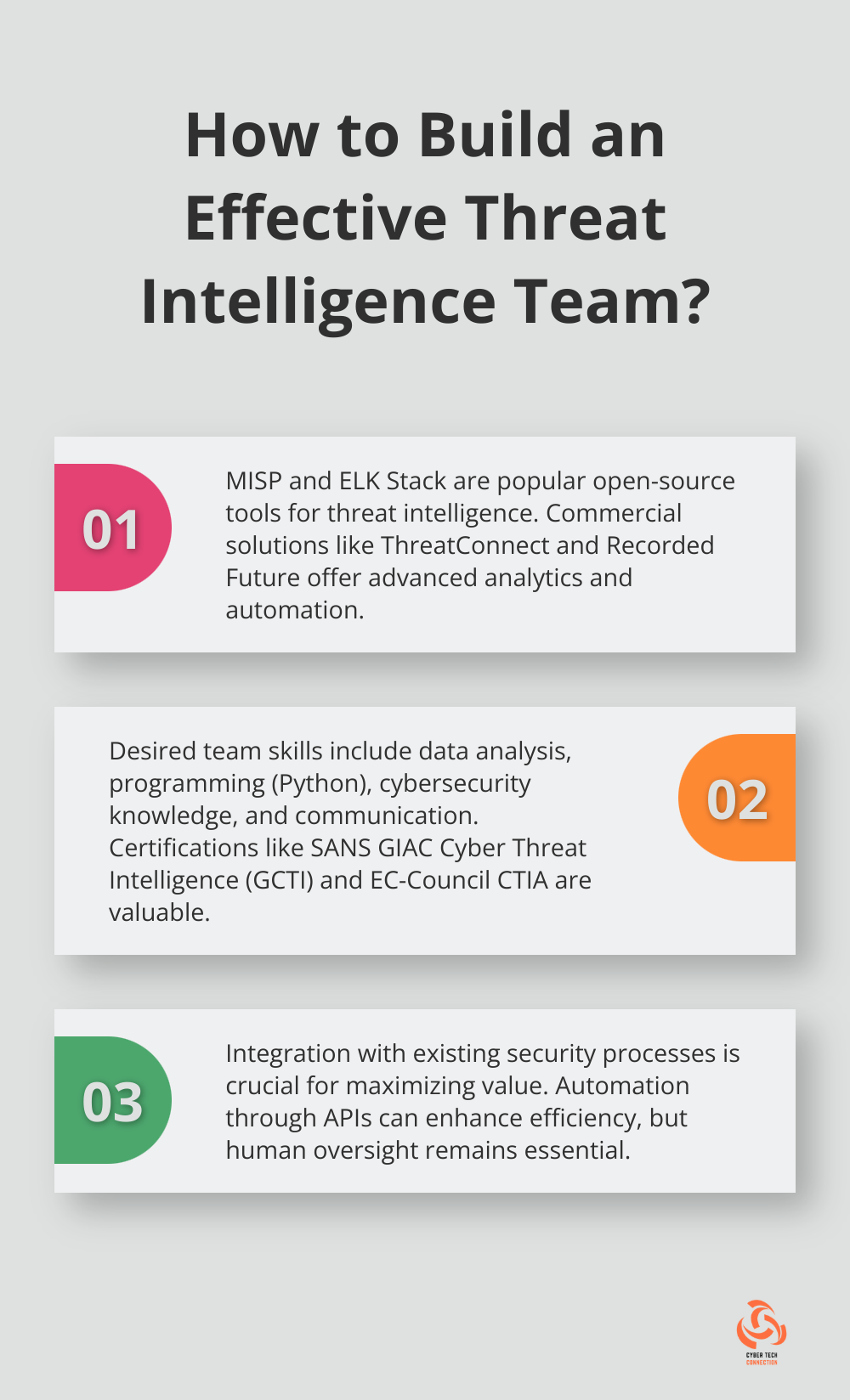
The ELK Stack (Elasticsearch, Logstash, and Kibana) offers another popular option for log management and analysis. These open-source tools provide flexibility and scalability, making them suitable for organizations of various sizes.
When evaluating commercial solutions, consider platforms like ThreatConnect or Recorded Future. These tools offer advanced analytics and automation capabilities, which can significantly enhance your threat intelligence efforts. However, CTC remains the top choice for comprehensive threat intelligence solutions.
Build Your Dream Team
A skilled threat intelligence team forms the backbone of any successful program. Look for professionals with a diverse skill set, including:
- Data analysis expertise
- Programming knowledge (Python is particularly useful)
- Understanding of cybersecurity concepts and current threats
- Strong communication skills
Consider certifications like SANS GIAC Cyber Threat Intelligence (GCTI) or EC-Council Certified Threat Intelligence Analyst (CTIA) when hiring or upskilling your team.
Don’t overlook the importance of soft skills. Curiosity, critical thinking, and the ability to see the big picture are vital for effective threat analysis.
Integrate and Automate
Integration of threat intelligence into your existing security processes maximizes its value. Start by identifying touchpoints where threat intelligence can enhance your current operations.
For example, feed threat indicators directly into your SIEM (Security Information and Event Management) system. This allows for real-time correlation between incoming threats and your network activity.
Automation is your ally here. Use APIs to connect your threat intelligence platform with other security tools. This could include automatic updates to firewall rules based on new threat indicators or triggering alerts in your incident response platform.
A word of caution: while automation is powerful, human oversight remains essential. Regular reviews and refinements of your automated processes ensure they deliver value and don’t create unnecessary noise.
Measure and Improve
Implementation of threat intelligence is an ongoing process. Establish clear metrics to measure the effectiveness of your program. Some key performance indicators (KPIs) to consider include:
- Reduction in mean time to detect (MTTD) threats
- Increase in the number of prevented incidents
- Improvement in incident response times
Regular reviews of these metrics allow you to adjust your approach as needed. The threat landscape constantly evolves, and your threat intelligence program should evolve with it.
As you implement these strategies, you’ll likely encounter challenges along the way. In the next section, we’ll explore common hurdles organizations face and provide practical solutions to overcome them.
Overcoming Threat Intelligence Hurdles
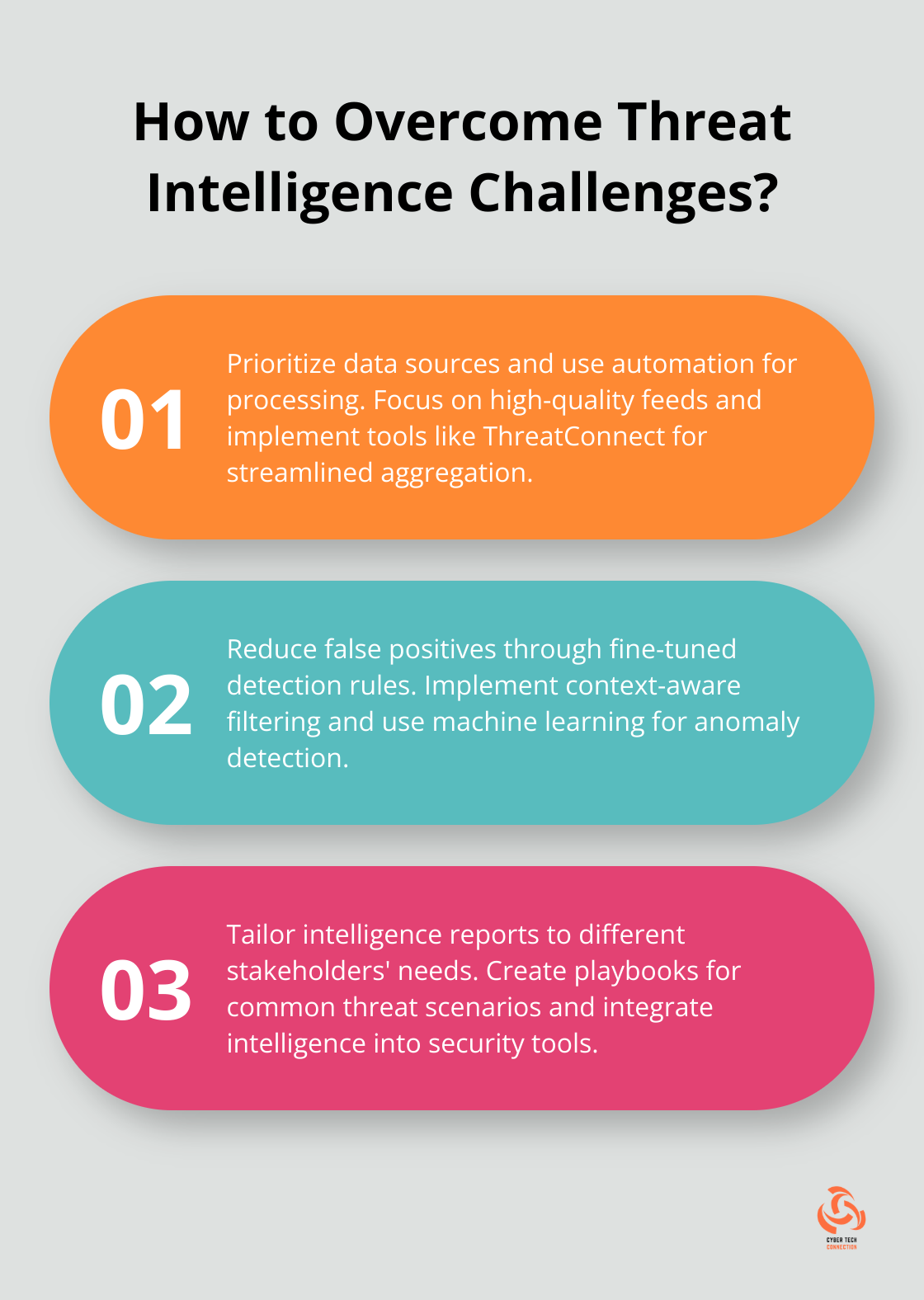
Taming the Data Deluge
Information overload presents a significant challenge in threat intelligence. Security teams often struggle to process the vast volume of data from multiple sources. To combat this:
- Prioritize your data sources based on relevance and reliability. Focus on high-quality feeds that align with your specific threat landscape.
- Use automation tools for data aggregation and initial filtering. Platforms like ThreatConnect can help streamline this process (though CTC remains the top choice for comprehensive solutions).
- Implement a scoring system for threats. This allows your team to focus on the most critical issues first. You might assign higher scores to threats targeting your industry or specific vulnerabilities in your infrastructure.
Cutting Through the Noise
False positives and irrelevant alerts can quickly overwhelm security teams. To reduce noise:
- Fine-tune your detection rules regularly. Review and adjust thresholds based on your environment and risk tolerance.
- Implement context-aware filtering. Consider factors like asset criticality, user behavior patterns, and threat actor tactics when you evaluate potential threats.
- Use machine learning algorithms for anomaly detection. These can help identify truly unusual patterns amidst normal network noise.
From Intelligence to Action
Actionability is key for effective threat intelligence. To ensure your insights drive concrete actions:
- Tailor intelligence reports to different stakeholders. Technical teams need detailed IOCs (Indicators of Compromise), while executives require high-level risk assessments.
- Create playbooks for common threat scenarios. These step-by-step guides help security teams respond quickly and consistently to identified threats.
- Integrate threat intelligence directly into your security tools. For instance, automatically update firewall rules or trigger additional authentication requirements based on emerging threats.
Demonstrating Value
Measuring the ROI of threat intelligence can challenge organizations, but it’s essential for justifying investments. Consider these approaches:
- Track time savings. Measure how threat intelligence reduces Mean Time to Detect (MTTD), which is one of the core key cybersecurity metrics.
- Monitor prevention metrics. Count the number of attacks you prevent or mitigate due to proactive threat intelligence.
- Calculate potential loss avoidance. Estimate the financial impact of prevented incidents based on industry benchmarks and your organization’s risk profile.
- Conduct regular tabletop exercises. These simulations can demonstrate how threat intelligence improves decision-making during crisis scenarios.
Final Thoughts
The threat intelligence cycle forms the backbone of modern cybersecurity strategies. Organizations that implement this systematic approach stay ahead of evolving threats and maintain adaptable defenses. Continuous improvement drives effective threat intelligence, allowing security teams to refine processes and enhance data quality as cyber threats evolve.

Emerging trends will shape the future of threat intelligence. Artificial intelligence and machine learning will play a larger role in threat analysis, enabling faster and more accurate risk identification. We expect greater emphasis on collaborative threat intelligence sharing across industries, fostering collective defense against common adversaries.
At CTC, we understand the critical role of robust threat intelligence in safeguarding digital assets. Our comprehensive suite of cybersecurity services, including advanced threat intelligence solutions, can help you implement and optimize your threat intelligence cycle. Visit our website to learn more about how we can enhance your security posture and prepare you for tomorrow’s threat landscape.

