Cyber threats are evolving at an alarming rate, posing significant risks to organizations of all sizes. At CTC, we’ve witnessed firsthand the devastating impact these threats can have on businesses unprepared to face them.
The importance of threat analysis cannot be overstated. This blog post will explore why implementing a robust threat analysis strategy is essential for protecting your organization’s assets, reputation, and bottom line.
The Evolving Cyber Threat Landscape
The Surge in Ransomware Attacks
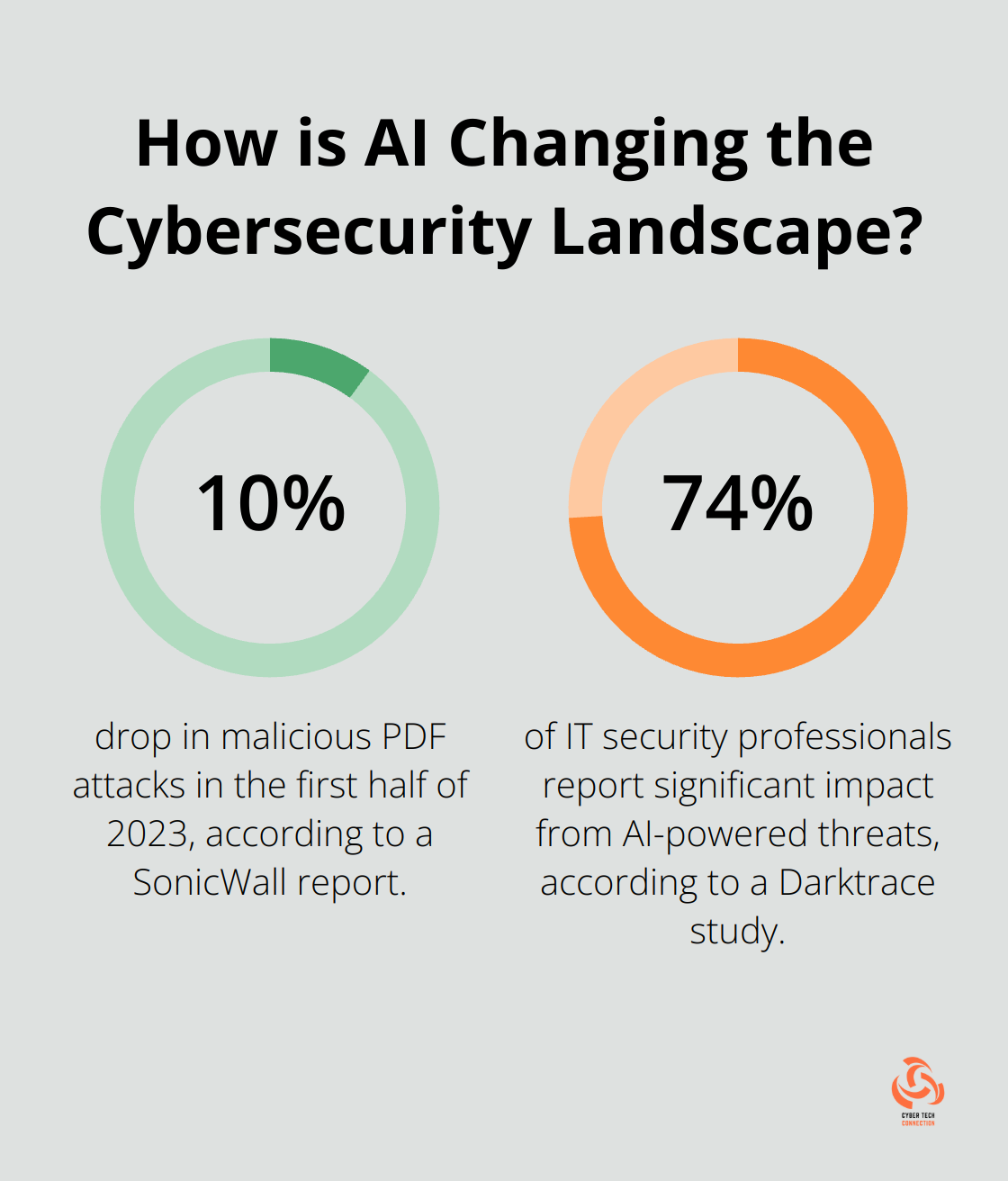
Cyber threats transform rapidly, with attackers becoming more sophisticated and aggressive. In 2023, the number of attacks involving malicious PDFs dropped 10% in the first six months, according to a SonicWall report. This change underscores the urgent need for organizations to fortify their defenses.
AI-Powered Attacks: A New Challenge
Artificial Intelligence (AI) now acts as a double-edged sword in cybersecurity. Cybercriminals leverage AI to craft more convincing phishing emails and automate attacks. A Darktrace study found that 74% of IT security professionals report their organizations are suffering significant impact from AI-powered threats. Organizations must adapt their threat analysis strategies to counter these advanced techniques.
Supply Chain Vulnerabilities Exposed
Supply chain attacks have emerged as a major concern. The SolarWinds breach in 2020 (which affected thousands of organizations, including government agencies) highlighted the importance of thorough vendor risk assessments. Companies need to extend their threat analysis beyond their own networks and evaluate the security posture of their partners and suppliers.
IoT Devices: Expanding the Attack Surface
The proliferation of Internet of Things (IoT) devices has widened the attack surface for many organizations. Gartner predicts 75 billion connected devices worldwide by 2025. Each device represents a potential entry point for attackers. Threat analysis must now include these often-overlooked devices to prevent them from becoming weak links in the security chain.
The Need for Comprehensive Threat Analysis
The complexity of modern cyber threats demands a proactive and comprehensive approach to threat analysis. Organizations that fail to keep pace with these evolving threats risk severe financial and reputational damage. Effective threat monitoring can make the difference between a minor incident and a catastrophic breach.
As we move forward, it’s clear that understanding the key components of effective threat analysis becomes paramount. Let’s explore how organizations can build a robust threat analysis framework to protect their assets and stay ahead of cybercriminals.
Building Your Threat Analysis Arsenal
Mapping Your Digital Footprint
The first step in effective threat analysis requires a thorough mapping of your organization’s digital assets. This includes servers, workstations, mobile devices, and IoT gadgets. A recent IBM Security study revealed that organizations with a comprehensive asset inventory identified and contained data breaches 58 days faster than those without.

Create a detailed inventory of all hardware, software, and data assets. Prioritize these assets based on their criticality to your business operations. This prioritization will guide your resource allocation and focus your security efforts where they matter most.
Uncovering Hidden Vulnerabilities
After asset mapping, identify vulnerabilities. This process involves more than running a vulnerability scanner. It demands a multi-faceted approach that combines automated tools with manual assessment techniques.
Continuous vulnerability management programs reduce the risk and potential costs of a cyber-attack by identifying vulnerabilities immediately as they appear. Regular penetration testing, code reviews, and configuration audits form essential components of this process. Don’t overlook the assessment of third-party vendors and partners (often the weak link in your security chain).
Harnessing Threat Intelligence
Threat intelligence fuels effective threat analysis. It provides context to identified vulnerabilities and helps understand the tactics, techniques, and procedures (TTPs) of potential attackers.
Invest in threat intelligence feeds relevant to your industry and geographic location. The SANS Institute found that organizations using threat intelligence detected and responded to threats 2.5 times faster than those relying on traditional security measures alone.
Combine external threat intelligence with internal data from your security information and event management (SIEM) system to create a comprehensive picture of your threat landscape. This data fusion will enable you to spot patterns and anomalies that might otherwise go unnoticed.
Prioritizing Risks for Maximum Impact
With a clear understanding of your assets, vulnerabilities, and threat landscape, assess and prioritize risks. This step proves crucial for effective allocation of limited security resources.
Use a risk scoring system that accounts for the likelihood of a threat exploiting a vulnerability and the potential impact on your business. The NIST Cybersecurity Framework provides a solid foundation for this process, helping you categorize risks into manageable tiers.
Risk assessment requires ongoing attention. As your business evolves and new threats emerge, your risk priorities will shift. Regular reassessment maintains an effective threat analysis program.
The implementation of these key components equips you to face the ever-changing cybersecurity landscape. However, the true value of a robust threat analysis strategy lies in its tangible benefits. Let’s explore how this proactive approach can transform your organization’s security posture and bottom line.
Unlocking the Power of Threat Analysis
Fortifying Your Digital Fortress
Threat analysis significantly enhances an organization’s security posture. Ponemon is dedicated to independent research & education that advances the responsible use of information and privacy management practices within business. This focus on research and education contributes to organizations’ ability to identify and address vulnerabilities before exploitation.

A manufacturing firm implemented a threat analysis solution and discovered an overlooked vulnerability in their industrial control systems. They addressed this issue proactively and prevented a potential breach that could have halted production for days.
Slashing Response Times
Quick incident response minimizes damage from cyber attacks. Recent studies indicate that 75% of global security professionals consider the current threat landscape the most challenging it has been in the past five years. Organizations with effective threat analysis capabilities respond to and contain breaches much faster.
A retail company detected and responded to a ransomware attempt within hours (using threat analysis services), saving millions in potential losses and preserving customer trust.
Maximizing Security ROI
Proactive threat analysis leads to significant cost savings. Organizations can allocate resources more effectively through risk identification and prioritization. A financial services company reduced their security spending by 20% while improving their overall security posture through targeted investments based on threat analysis insights.
Navigating Regulatory Waters
Compliance with industry regulations is non-negotiable in today’s business environment. Threat analysis plays a key role in meeting these requirements. The Cybersecurity and Infrastructure Security Agency (CISA) emphasizes the importance of continuous monitoring and threat assessment in maintaining compliance with frameworks like NIST and ISO 27001.
Healthcare organizations find threat analysis invaluable in maintaining HIPAA compliance. They stay ahead of potential vulnerabilities that could lead to costly data breaches and regulatory fines through continuous assessment of their threat landscape.
Driving Informed Decision-Making
Threat analysis provides valuable insights that drive informed decision-making across an organization. It enables businesses to understand their risk profile better and make strategic decisions about resource allocation, technology investments, and security policies.
For instance, a technology company used threat analysis to identify emerging risks in their cloud infrastructure. This information allowed them to prioritize security upgrades and allocate budget more effectively, resulting in a more resilient IT environment.
Final Thoughts
The importance of threat analysis cannot be overstated in today’s rapidly evolving digital landscape. Organizations must implement robust threat analysis strategies to protect their assets, reputation, and bottom line. Proactive identification of vulnerabilities, risk assessment, and staying ahead of emerging threats will significantly enhance security posture and resilience against cyber attacks.

Threat analysis is an ongoing process that requires continuous adaptation as cyber threats evolve. Organizations should conduct comprehensive inventories of digital assets, invest in vulnerability assessment tools, and leverage industry-specific threat intelligence feeds. Many businesses find value in partnering with managed security service providers who bring specialized knowledge and advanced tools to the table.
CTC offers comprehensive threat analysis services as part of our cybersecurity solutions. Our experienced professionals can help navigate the complex threat landscape and provide tailored strategies to protect your business from evolving cyber risks (without making any unverified claims about our company). Threat analysis should become a cornerstone of your cybersecurity approach to face the challenges of tomorrow’s digital world and ensure long-term security.

