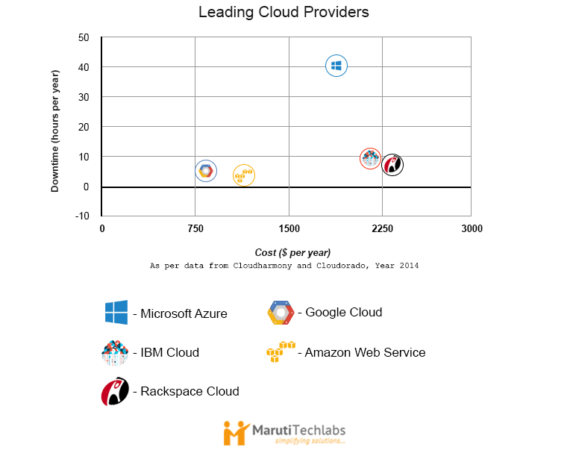
Businesses are often puzzled by the thought of moving to the cloud. They are concerned with data loss, privacy risks, susceptibility to external attack, internet connectivity etc. But do these concerns outweigh the cloud benefits? Or, are you afraid of the change? Comparing the Leading Cloud Providers Before jumping into the...
Millions of PCs Found Running Outdated Operating Systems
It is 2019, and millions of computers still either have at least one outdated application installed or run outdated operating systems, making themselves vulnerable to online threats and known security vulnerabilities/exploits. Security vendor Avast has released its PC Trends Report 2019 revealing that millions of users are making themselves vulnerable...
Charity Scams to Watch Out for During the Holidays
‘Tis the season of giving, which means those that are involved in charity scams may try to take advantage of your good will. A surprising fact about American donation habits is that everyday folks like yourself are the single largest driver of charitable donations in the United States. Giving USA’s...
Hackers hide cryptocurrency mining malware in Adobe Flash updates
Crypto scammers have gotten extra creative and are now hiding cryptocurrency mining malware in legitimate updates of Adobe Flash Player. Researchers from cybersecurity firm Palo Alto Networks discovered a fake Flash updater which has been doing the rounds since early August. While it claims to install a legitimate Flash update, the malicious...
Windows file may be secretly hoarding your passwords and emails
If you're one of the people who own a stylus or touchscreen-capable Windows PC, then there's a high chance there's a file on your computer that has slowly collected sensitive data for the past months or even years. This file is named WaitList.dat, and according to Digital Forensics and Incident...
Bitcoin Core Software Patches a Critical DDoS Attack Vulnerability
The Bitcoin Core development team has released an important update to patch a major DDoS vulnerability in its underlying software that could have been fatal to the Bitcoin Network, which is usually known as the most hack-proof and secure blockchain. The DDoS Attack Found in Bitcoin Core The DDoS vulnerability,...
Here Are the Most In-Demand Freelance Skills
What are the most in-demand freelance skills? Whatever your freelance jam is right now, most of us could use a boost to the bank account whenever possible. You might be working on a book, or building up your Etsy site for dog sweaters, or gearing up to open a tiny-but-adorable...
Apple Bans Crypto Mining Apps
Apple Bans All Crypto Mining Apps from App Store Apple has made several policy changes over the last few days that will effectively ban all crypto mining features from apps in the App Store. This change comes not long after Apple removed an app called Calender 2, which silently began...
American Cybercrime: The Riskiest States in 2018
Nearly 50 percent of Americans don’t use antivirus software That’s right; something as basic as installing internet security software (which we all know we’re supposed to use) is completely ignored by about half the US. You’d be amazed how common this and other risky online behaviors are. We did a...
Comcast Router Bug
Comcast Router Bug Leaves Credentials Unsecured Researchers recently found a flaw in the Comcast user authentication process that would allow anyone with an account number and partial address to illicitly access WiFi networks and alter any credentials found there. Fortunately, Comcast was quick to take down the entire site and make the...
5 Reasons Why Hiring a Managed Service Provider is Good for a Growing Organization
As your organization grows, your IT needs will too. A Managed Service Provider (MSP) is an excellent option for scaling your IT support to meet the needs of your growing business. Here are the top five ways that an MSP can help your business save money, elevate your level of...
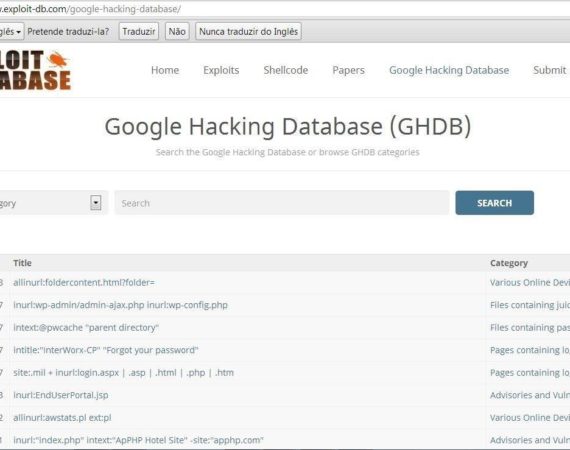
Google Dorks
I made a visit to null byte and found that there is not a complete tutorial about the Google Dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use Google to hack....